Enrich threat observables with AbuseIPDB
- Latest Dynatrace
- How-to guide
Enrich threat observables with AbuseIPDB and analyze them in Dynatrace.
Get started
Overview
The Dynatrace integration with AbuseIPDB enhances alerts and detection investigations by providing valuable context for threat intelligence. This helps organizations combat online abuse, including cyber-attacks, spamming, and other malicious activities.
By enriching observability with reputation data from AbuseIPDB, you can conduct more efficient security investigations, automate alert triaging, and reduce noise through threat-aware prioritization. This streamlines incident response and enhances overall security posture.
Use cases
Once you set up the AbuseIPDB integration, you can leverage threat intelligence to enrich observables like IP addresses.
Key use cases include:
-
Enhance detection findings in
 Threats & Exploits with external reputation data.
Threats & Exploits with external reputation data. -
IP enrichment with the Workflows app
- In
 Workflows
Workflows  , create a new workflow or edit an existing one.
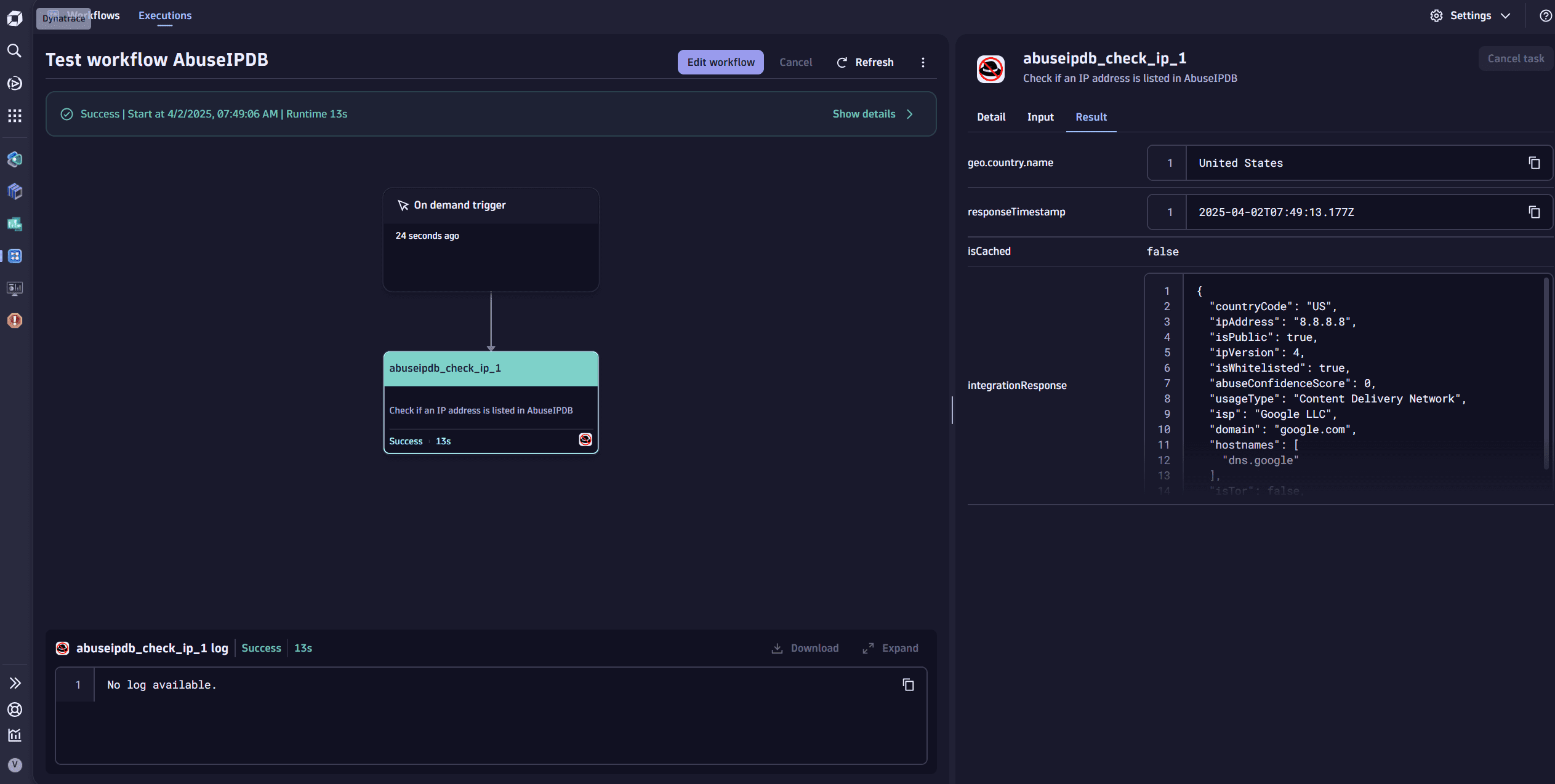
, create a new workflow or edit an existing one. - In the Choose action pane, search for AbuseIPDB and select the AbuseIPDB check IP action.
- Enter the parameters required for the action to run.
- Run the workflow to validate the action and review the results.
- Continue with your automation definition.
- In
-
Threat-informed security investigations Coming soon
Requirements
See below for the AbuseIPDB and Dynatrace requirements.
AbuseIPDB requirements
Register with AbuseIPDB and create an API v2 key.
Dynatrace requirements
The following IAM permissions are required:
app-engine:apps:runapp-settings:objects:readdocument:documents:readsettings:objects:readstorage:system:readsecurity-intelligence:enrichments:run
To run the enrichment workflow action, all the permissions above need to be enabled in  Workflows as well.
Workflows as well.
- Go to the settings menu in the upper-right corner of
 Workflows and select Authorization settings.
Workflows and select Authorization settings. - In Secondary permissions, search for and select the above-listed permissions.
- Select Save.
Activation and setup
-
In Dynatrace, open Hub.
-
Look for AbuseIPDB and select Install.
-
Select Set up , then select Configure new connection.
-
Follow the on-screen instructions to set up the connection using the API key obtained in Prerequisites.
Allowed outbound connections are extended automatically with
api.abuseipdb.com.1. How to set up outbound connections
- In Settings, go to General > External requests.
- In Allowlist, select New host pattern and add the domain.
-
Test the connection to ensure the correct configuration and save it.
Details
How it works
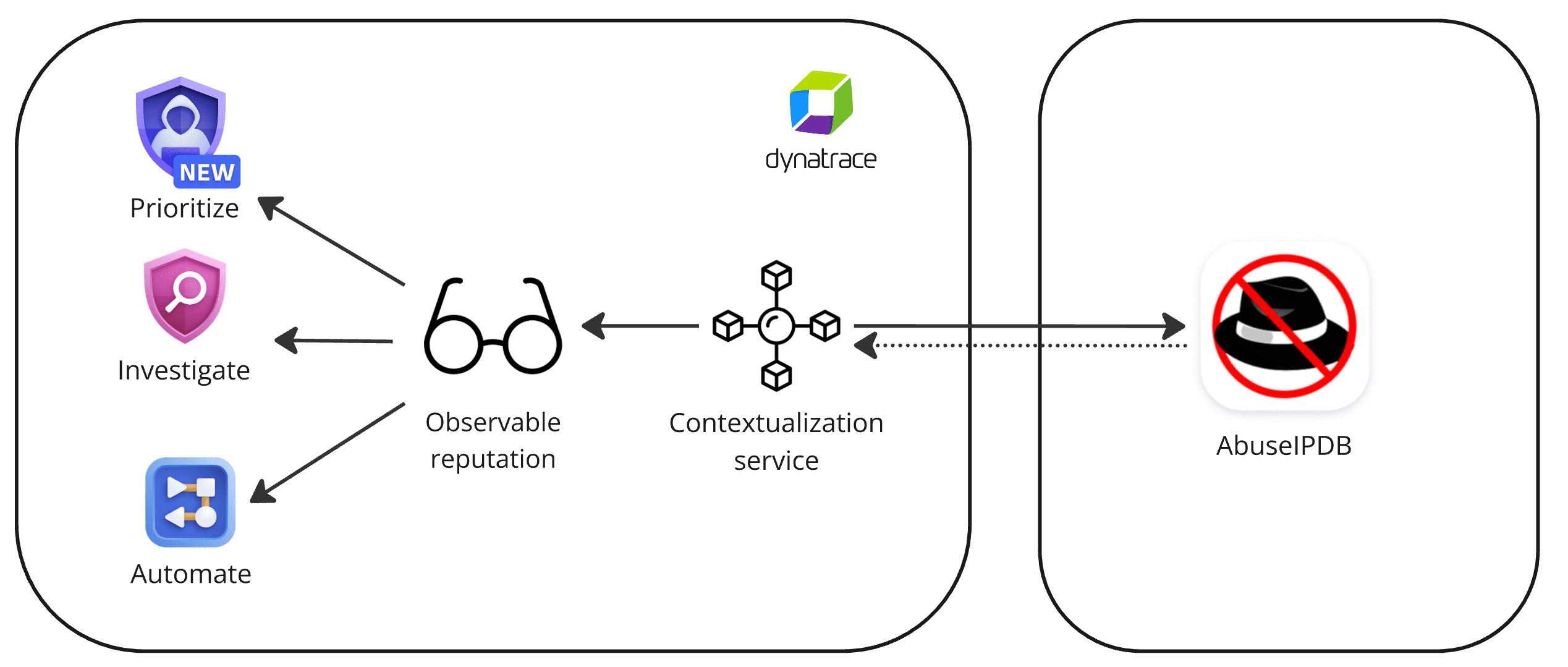
1. Install and configure the app
Dynatrace integration with AbuseIPDB is an app that you can install from Hub.
The app delivers a workflow action for observable enrichment in  Workflows.
Workflows.
To prevent accidental edits or deletions across environments, connection setup now includes owner-based access control. This ensures reliable automation, avoids unexpected configuration loss, and aligns with minimal access requirements.
For details on sharing and permissions, see Access control for Connectors.
2. Enrich observables
Various consumer apps can perform an on-demand enrichment of observables, for example, via a workflow action.
Dynatrace reaches out to AbuseIPDB to perform the observable enrichment.
Geolocation fields in enrichment results are sourced from the provider and can differ from the geolocation used in Dynatrace.
For more information, see FAQ: Geolocation differences.
3. Use the threat intelligence data
The threat intelligence context is displayed within the consumer apps or in  Workflows, helping you drive smarter decisions.
Workflows, helping you drive smarter decisions.
Licensing and cost
For billing information, see Events powered by Grail.
FAQ
Which observable types are currently supported?
Supported observables: IP addresses (more coming soon).
How will my AbuseIPDB API quotas will be affected from this integration?
For every new observable enrichment we perform a single API call.
Why does geolocation differ between enrichment results and Dynatrace?
Geolocation fields in enrichment results (such as geo.country.iso_code, geo.country.name, and city/coordinates if available) are provided directly by the external provider (in this case, AbuseIPDB).
These values reflect the AbuseIPDB geolocation data and may differ from the geolocation used in Dynatrace features (such as Real User Monitoring or platform‑level geolocation).
Differences can occur because of different databases, update cycles, or mapping rules.

