Ingest Amazon ECR container vulnerability findings and scan events
- Latest Dynatrace
- How-to guide
This page has been updated to align with the new Grail security events table. For the complete list of updates and actions needed to accomplish the migration, follow the steps in the Grail security table migration guide.
Ingest Amazon ECR container image vulnerability findings and scan events and analyze them in Dynatrace.
Get started
Overview
In the following, you'll learn how to ingest container vulnerability findings and scan events from AWS Elastic Container Registry (ECR) into Grail and analyze them on the Dynatrace platform, so you can gain insights into Amazon ECR container vulnerability findings and easily work with your data.
Use cases
With the ingested data, you can accomplish various use cases, such as
Requirements
-
Set up the desired Amazon ECR scan type. You have two options:
To determine which type of scan to choose, see Scan images for software vulnerabilities in Amazon ECR.
-
Install and configure the latest AWS CLI.
-
Select the AWS region where you want to create the Amazon ECR event forwarder.
Show me how
- In a terminal, run:
aws configure- Set your default region (for example,
us-east-1).
-
Permissions:
- You need an Admin user to define a custom policy with the
app-engine:apps:installpermission to install the app. For details, see Dynatrace access. - To query ingested data:
storage:security.events:read.
- You need an Admin user to define a custom policy with the
-
Tokens:
- Generate an access token with the
openpipeline.events_securityscope and save it for later. For details, see Dynatrace API - Tokens and authentication.
- Generate an access token with the
Activation and setup
- In Dynatrace, open Hub.
- Look for Amazon ECR and select Install.
- Select Set up, then select Configure new connection.
- Follow the on-screen instructions to set up the ingestion.
Details
How it works
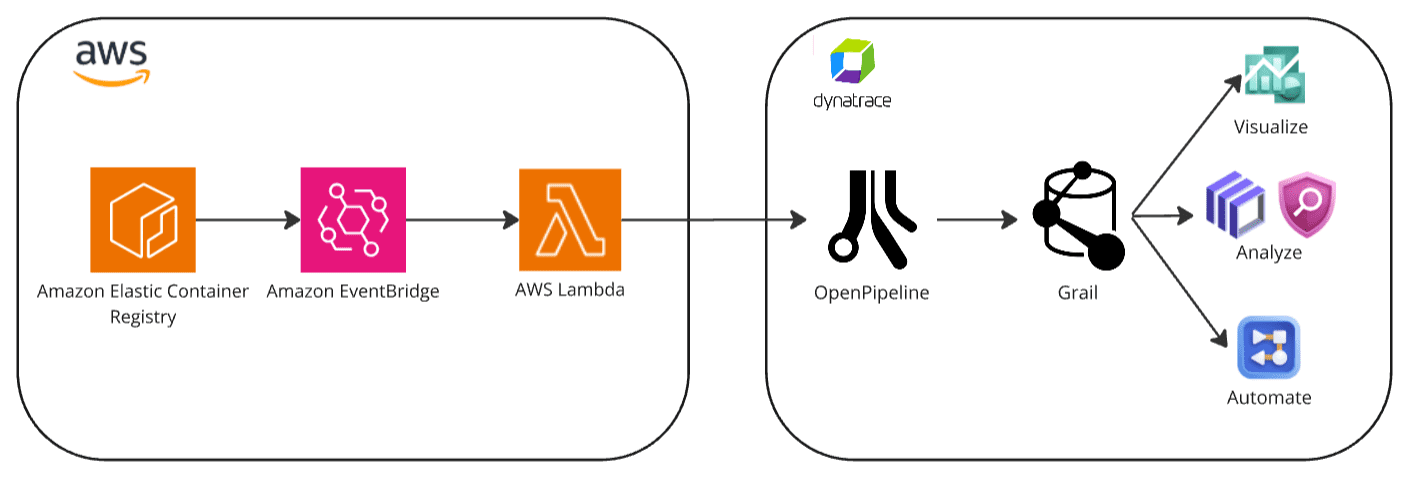
1. Container image vulnerabilities are ingested into Dynatrace
Container image vulnerabilities reported in Amazon ECR are ingested into Dynatrace via a dedicated OpenPipeline security events ingest endpoint, using an Amazon EventBridge event forwarding set up with an AWS CloudFormation template.
2. Vulnerability findings are processed and stored in Grail
The OpenPipeline ingest endpoint processes and maps the security findings according to the Semantic Dictionary conventions.
These are stored in a bucket called default_securityevents (for details, see: Built-in Grail buckets).
Monitor data
Once you ingest your Amazon ECR data into Grail, you can monitor your data in the app (in Dynatrace, go to Settings > Amazon ECR).
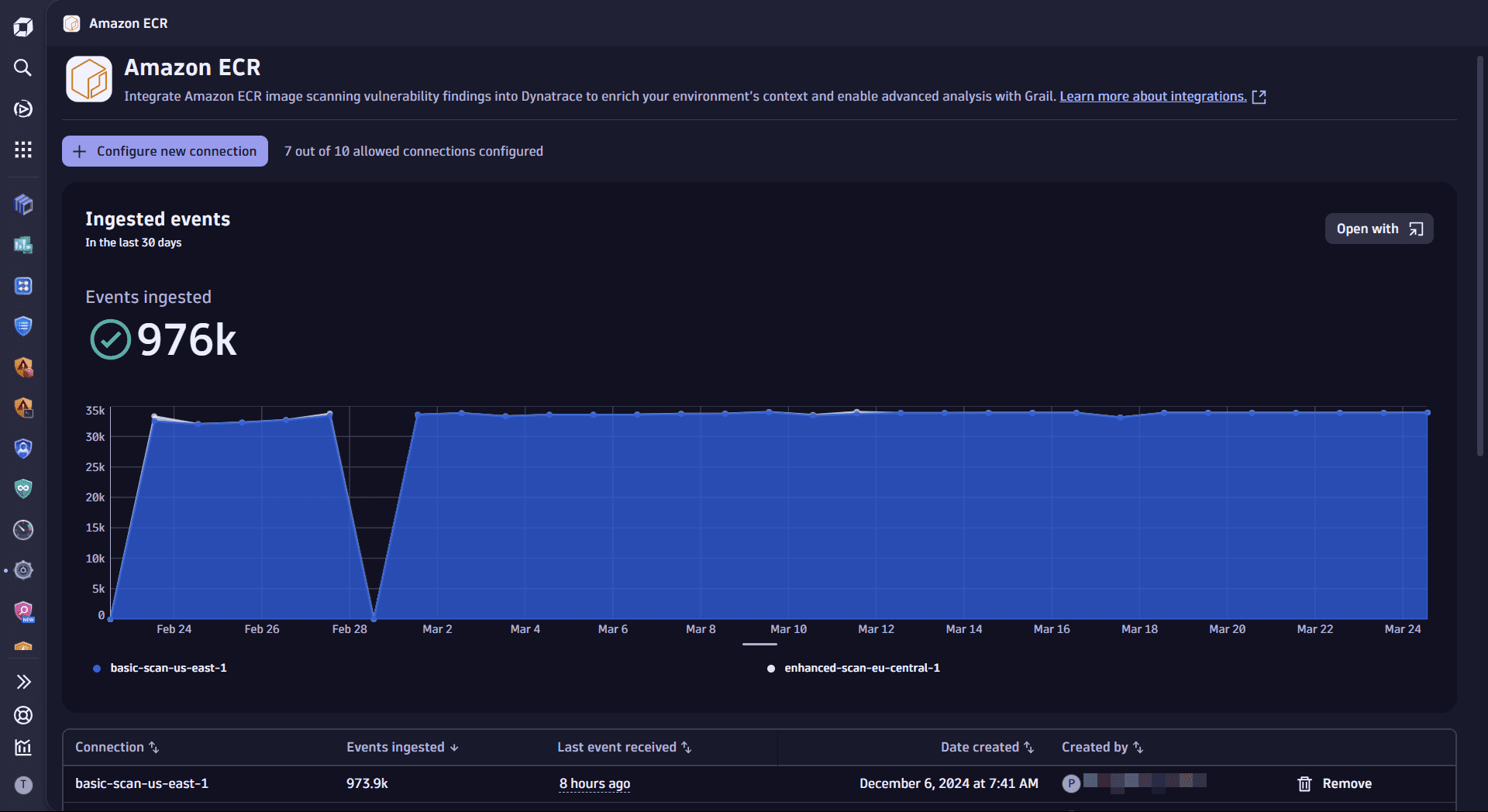
You can view
-
A chart of ingested data from all existing connections over time
- Available actions: Query ingested data
-
A table with information about your connections
- Available actions: Remove connection
Visualize and analyze findings
You can create your own dashboards or use our templates to visualize and analyze container vulnerability findings.
To use a dashboard template
- In Dynatrace, go to Settings > Amazon ECR.
- In the Try our templates section, select the desired dashboard template.
Automate and orchestrate findings
You can create your own workflows or use our templates to automate and orchestrate container vulnerability findings.
To use a workflow template
- In Dynatrace, go to Settings > Amazon ECR.
- In the Try our templates section, select the desired workflow template.
Query ingested data
You can query ingested data in  Notebooks or
Notebooks or  Investigations, using the data format in Semantic Dictionary.
Investigations, using the data format in Semantic Dictionary.
To query ingested data
- In Dynatrace, go to Settings > Amazon ECR.
- Select Open with .
- Select Investigations or Notebooks.
Delete connections
To stop sending events to Dynatrace
- In Dynatrace, go to Settings > Amazon ECR.
- For the connection you want to delete, select Delete.
- Follow the on-screen instructions to delete the resources. If you used values different from those specified in the setup dialog, adjust them accordingly.
This removes the Dynatrace resources created for this integration.
Licensing and cost
For billing information, see Events powered by Grail.
