Ingest vulnerability findings in OCSF format
- Latest Dynatrace
- How-to guide
This page has been updated to align with the new Grail security events table. For the complete list of updates and actions needed to accomplish the migration, follow the steps in the Grail security table migration guide.
Ingest vulnerability findings in OCSF format from any provider and analyze them on the Dynatrace platform.
Get started
Overview
In the following, you'll learn how to ingest vulnerability findings from any source or provider in a standard format (Open Cybersecurity Schema Framework (OCSF)) into Grail and analyze them on the Dynatrace platform, so you can get Dynatrace insights for vulnerability findings from any source or provider, and easily work with your data on the Dynatrace platform in a unified format.
Use cases
With the ingested data, you can accomplish various use cases, such as
Requirements
- Permissions:
- To query ingested data:
storage:security.events:read.
- To query ingested data:
Activation and setup
- In Dynatrace, open Hub.
- Look for OCSF and select Install.
- Select Set up, then select Configure new connection.
- Follow the on-screen instructions to set up the ingestion.
Details
How it works
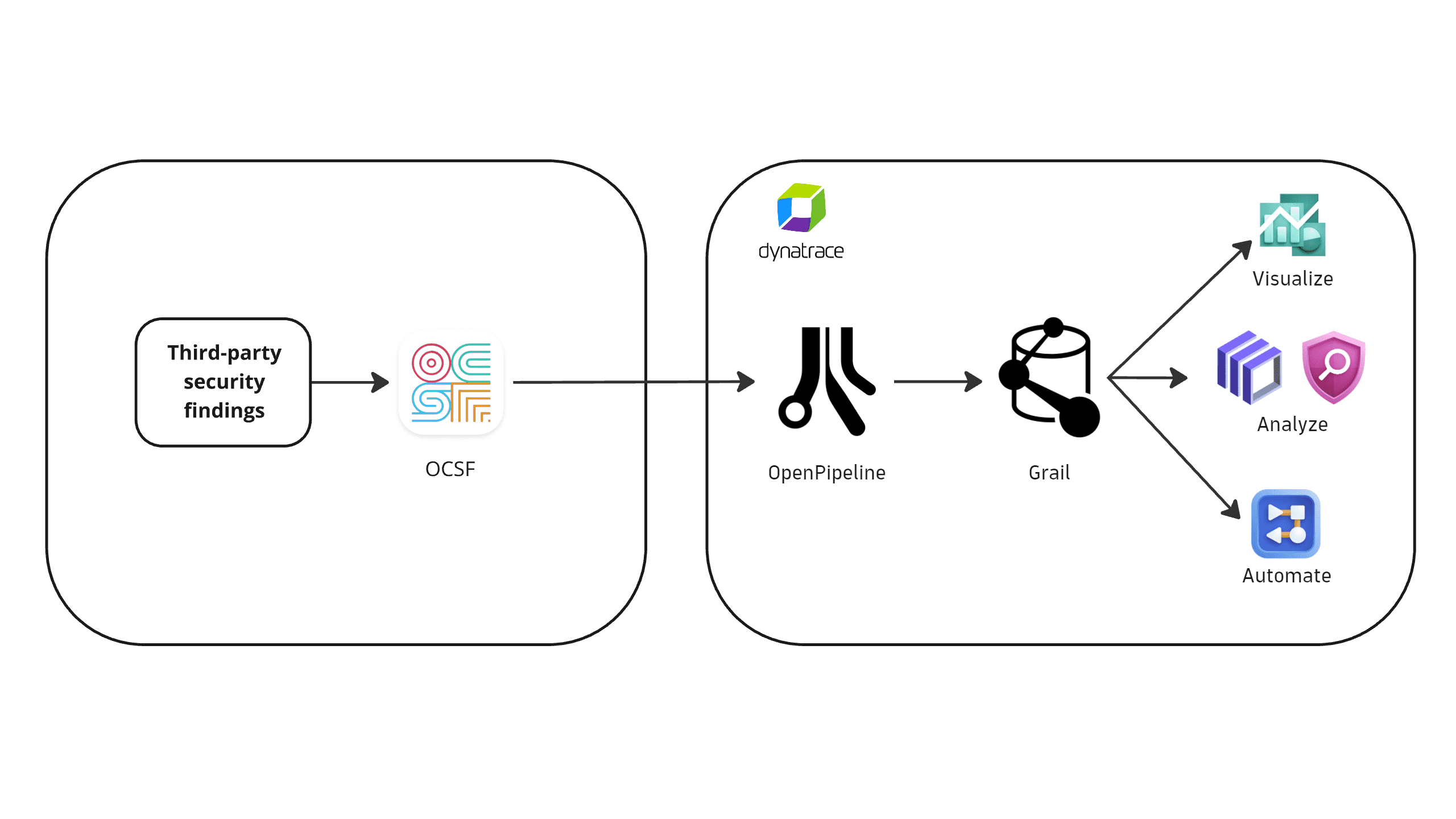
1. Feed OCSF-formatted data into Grail
You feed the OCSF-formatted data into Grail via our built-in security events OpenPipeline endpoint.
For instructions, see Get started.
2. Data is mapped to the Semantic Dictionary
The OpenPipe ingest endpoint receives the vulnerability findings and maps them according to the Semantic Dictionary.
They are stored in the default_securityevents bucket (see Built-in Grail buckets).
Ingested data is mapped to Dynatrace Semantic Dictionary. Original vendor data is also preserved alongside the mapped data.
3. Enjoy the data
Once data is ingested into Grail, you can visualize, analyze, and automate data using dashboards, workflows, and queries.
Monitor data
Once you ingest your OCSF data into Grail, you can monitor your data in the app (in Dynatrace, go to Settings, then search for and select OCSF).
You can view:
-
A chart of ingested data from all existing connections over time
- Available actions: Query ingested data
-
A table with information about your connections
- Available actions: Delete connection
Visualize and analyze findings
You can create your own dashboards or use our templates to visualize and analyze container vulnerability findings.
To use a dashboard template:
- In Settings, open OCSF.
- In the Try our templates section, select the desired dashboard template.
Automate and orchestrate findings
You can create your own workflows or use our templates to automate and orchestrate container vulnerability findings.
To use a workflow template:
- In Settings, open OCSF.
- In the Try our templates section, select the desired workflow template.
Query ingested data
You can query ingested data in  Notebooks or
Notebooks or  Investigations, using the data format in Semantic Dictionary.
Investigations, using the data format in Semantic Dictionary.
To query ingested data:
- In Settings, open OCSF.
- Select Open with .
- Select Investigations or Notebooks.
Support
For OCSF, Dynatrace supports vulnerability findings (regardless of the source) following the OCSF v1.1.0 format.
Delete connections
To stop sending events to Dynatrace:
- In Settings, open OCSF.
- For the connection you want to delete, select Delete.
- Follow the on-screen instructions to delete the resources. If you used values different from those specified in the setup dialog, adjust them accordingly.
This removes the Dynatrace resources created for this integration.
Licensing and cost
For billing information, see Events powered by Grail.
