Supported connectivity schemes for ActiveGates
- Latest Dynatrace
- 4-min read
- Published Jul 17, 2018
Dynatrace requires certain ports and paths to be opened and accessible through the monitored infrastructure, firewalls and other components. The ports are configurable and the default values are shown here.
Dynatrace SaaS connectivity scheme
All possible connections for the SaaS connectivity scheme, with preferred and alternative paths are shown below.
The solid arrows indicate the preferred paths. For example, OneAgent will connect to an Environment ActiveGate, if one is present. It will, however, connect to a the Dynatrace Saas Cluster directly, if no connection to an Environment ActiveGate is possible. The direction of arrows in the diagrams indicates which component initiates the connection.
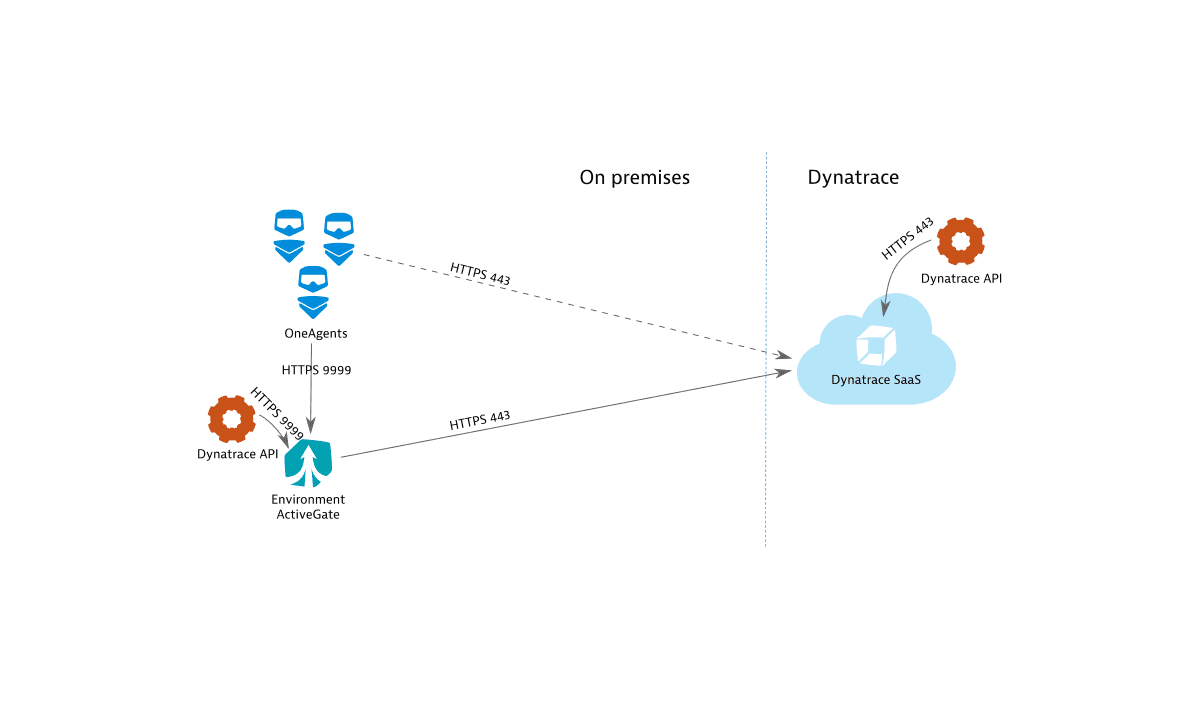
Port usage
- Environment ActiveGate receives connections on port 9999.
- Dynatrace SaaS Cluster receives connections on port 443.
If you run Browser monitors or HTTP monitors from private Synthetic locations, you need to make sure the Synthetic-enabled ActiveGate has access to the tested resource. If you use ActiveGate extensions, you need to make sure the ActiveGate executing the extensions has access to the monitored technology.
Network zones configuration means that OneAgents will prefer to communicate with ActiveGates from the same zone, before connecting to ActiveGates outside of the active zone.
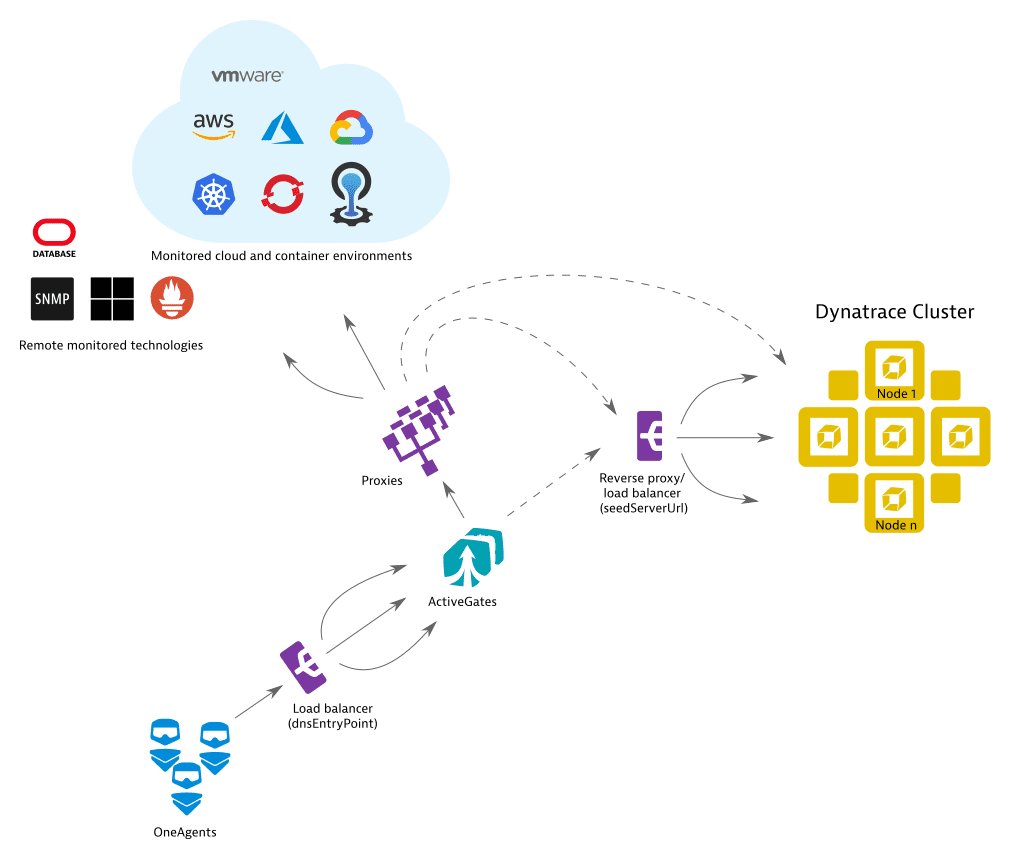
Proxy and load balancer configuration
All Dynatrace components (OneAgents, ActiveGates, Dynatrace Cluster) detect their hostnames and distribute them as communication endpoints among each other to achieve the highest possible connection robustness.
This works automatically, unless there are networking devices (proxies, load balancers) in your environment, which should be taken into account, and of which Dynatrace is not aware.
The diagram below shows all possible proxy and load balancer (reverse proxy) placements for an ActiveGate deployment. For simplicity, direct connections—those that are not through proxies or load balancers–are not shown in this diagram. Alternative connections (those that connect through one or more proxies or load balancers), are shown as dashed lines.
- If there is a load balancer between OneAgents and an ActiveGate, you should specify the load balancer's address as the
dnsEntryPointproperty in the ActiveGate configuration. - If there is a load balancer between ActiveGate and the next communication endpoint that traffic should be routed through, configure
seedServerUrlandignoreClusterRuntimeInfo - If a proxy is used to reach the Dynatrace Cluster or any of the monitored clouds, configure a proxy.
ActiveGate headers
You can configure the ActiveGate headers in your firewall.
Header
Value
User-Agent
-
Environment ActiveGate:
ruxit/<dynatrace-version> <activegate-instance-id> <environment-id>Example values
Environment and Multi-environment ActiveGate:
ruxit/1.229.163.20211109-103203 0x37badd8e c04442b4-7ea6-4ec4-a5c4-7f94c7cf25faCluster ActiveGate:
ruxit/1.229.163.20211109-103203 0x37badd8e -
HTTP monitors:
DynatraceSynthetic/<dynatrace-version>Example value
DynatraceSynthetic/1.258.0.20221207-142354 -
Browser monitors:
RuxitSynthetic/<dynatrace-version>Example value
Mozilla/5.0 (Windows NT 6.3;WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/37.0.2062.124 Safari/537.36 RuxitSynthetic/1.258.0.20221207-142354
dynatrace-gateway-type
- Environment ActiveGate:
PRIVATE - Managed or SaaS ActiveGate:
PUBLIC
- Multi-environment ActiveGate:
MULTI_TENANT
Authorization
Basic <TOKEN>