Security Investigator
Latest Dynatrace
What you'll learn
- Define and execute queries while combining functionalities.
- Search for relevant log information.
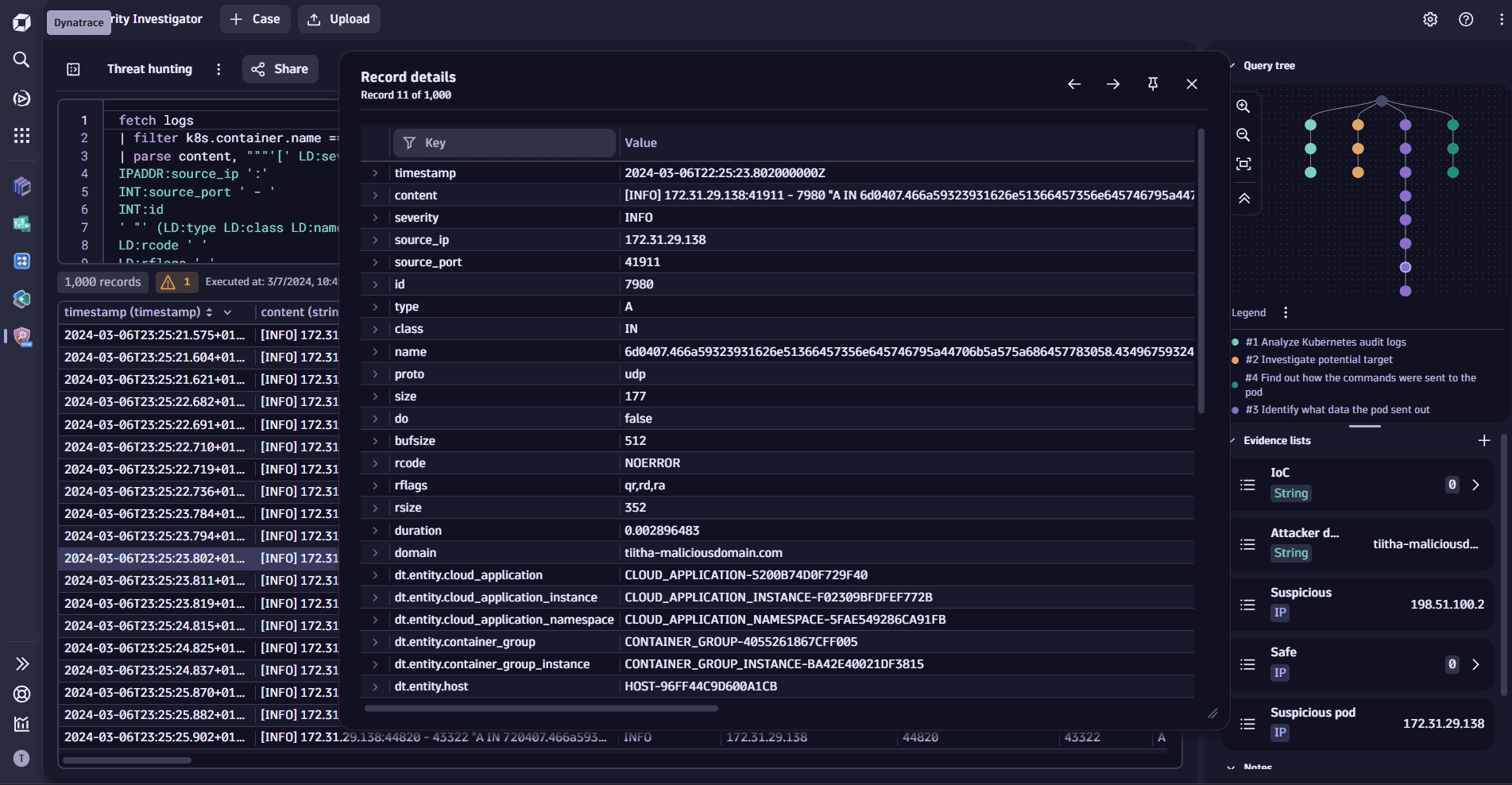
- Grasp structured information from log records.
- Extract fields and get instant feedback on patterns.
- Track your path, navigate to previous steps, view your investigation history.
- Define the time range for your data queries.
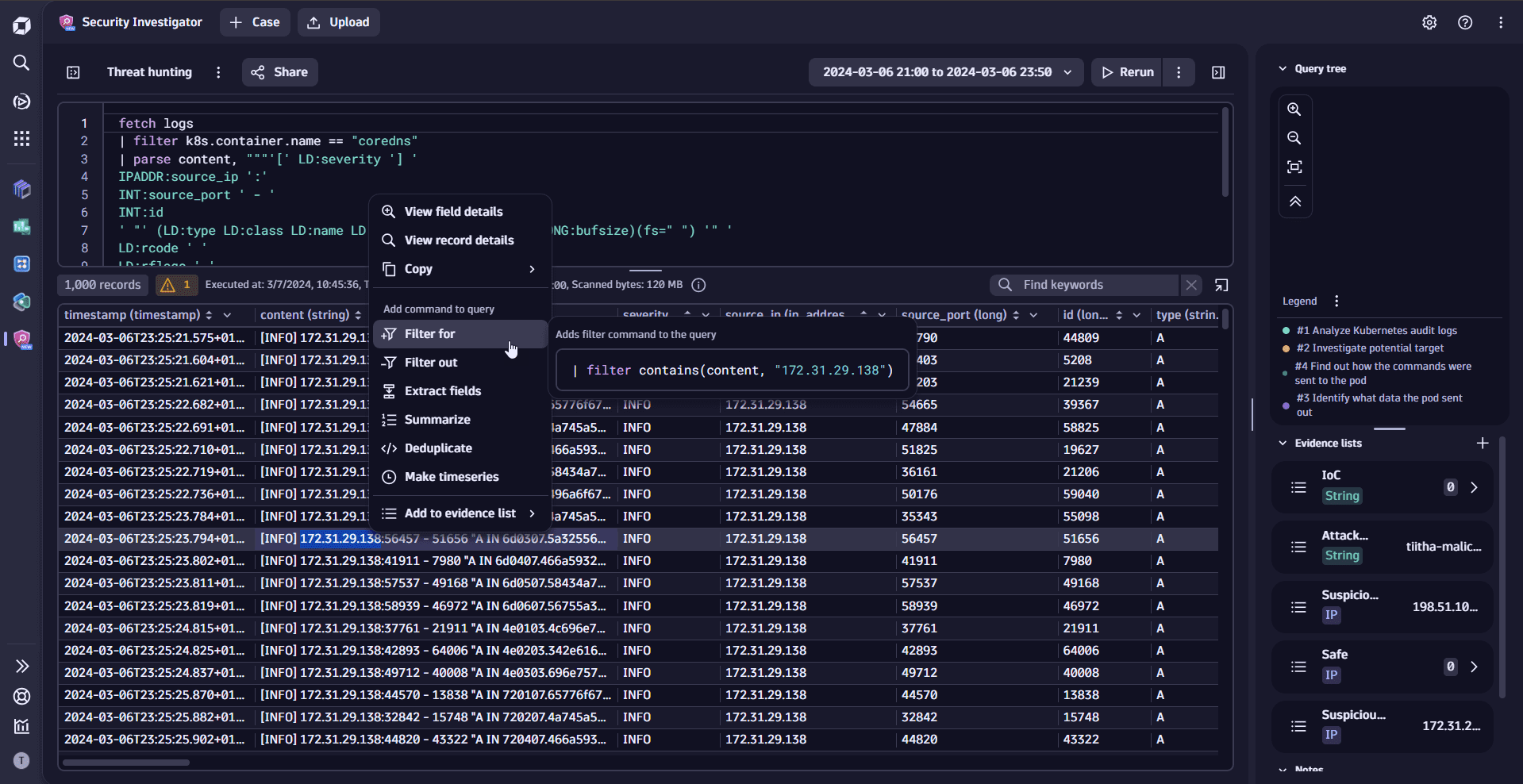
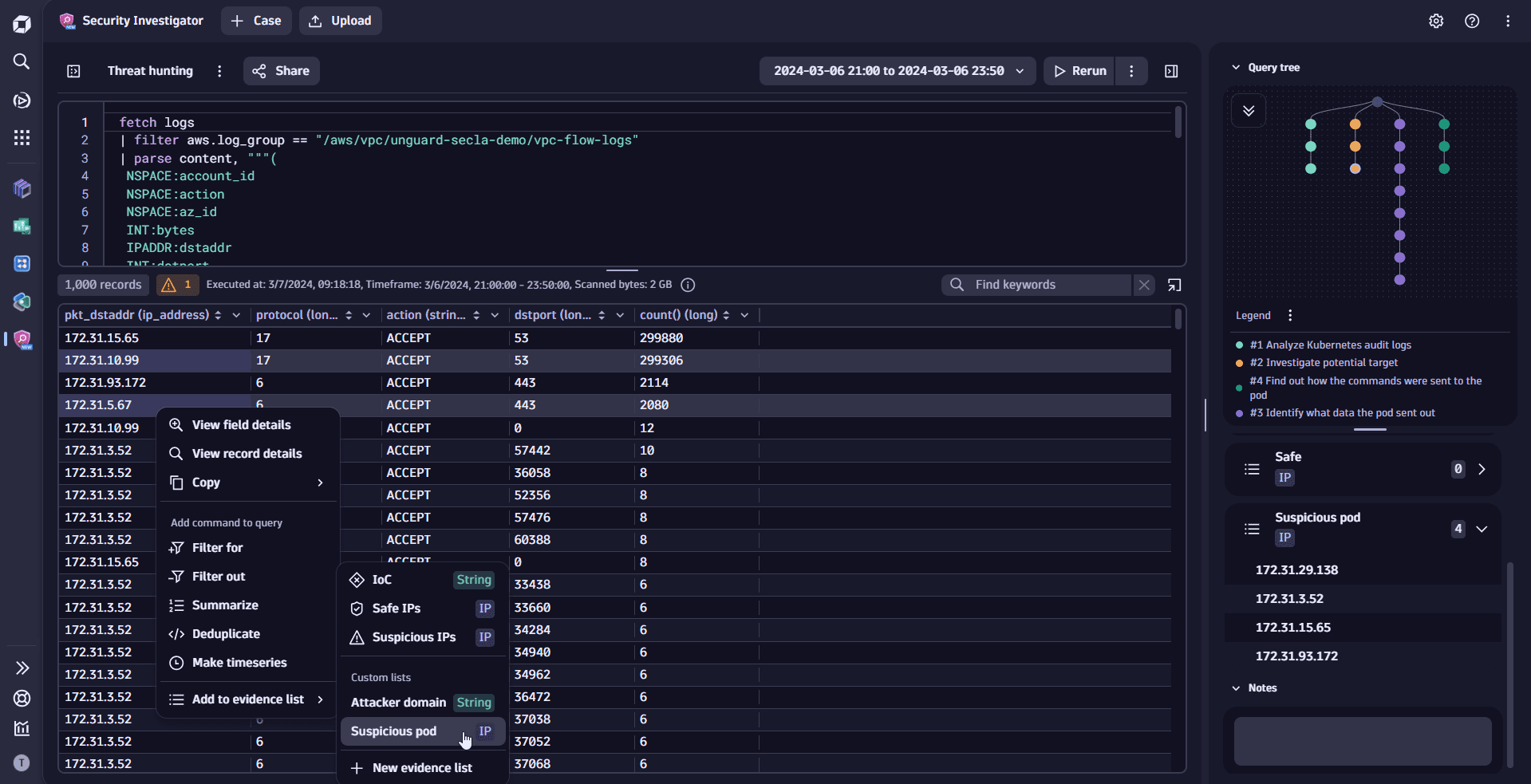
- Attach relevant findings as evidence, while preserving the investigation context.
- Collaborate with peers on threat hunting with controlled access.
- Interact with compatible apps for further insights.
Target audience
While Dynatrace Security Investigator  is primarily designed for security investigations, it's highly effective in conducting any detailed, evidence-driven investigation, no matter the field or nature of the inquiry.
is primarily designed for security investigations, it's highly effective in conducting any detailed, evidence-driven investigation, no matter the field or nature of the inquiry.
Key use cases include:
- Incident response
- Root cause analysis
- Threat hunting
- Fraud analysis and investigations
- Data forensics
Our diverse audience includes everyone involved in evidence-driven investigations, from security analysts and SREs to DevOps engineers and internal auditors handling major fraud investigations on large-scale events.
-
To investigate ingested logs, you need to set up log ingestion.
-
Permissions: For a list of permissions required, go to Dynatrace Hub
 , select Security Investigator
, select Security Investigator  , and display Technical information.
, and display Technical information. -
Basic knowledge of
Security Investigator  is designed to streamline evidence-driven investigations on data in Grail by
is designed to streamline evidence-driven investigations on data in Grail by
-
Eliminating manual, repetitive tasks
-
Providing contextual enrichment without tool-switching
-
Offering fast, detailed access to your data
-
Enhancing user experience for quick issue identification
It features assisted functionalities and automations to expedite and support investigation resolution, leveraging logs, metrics, and traces ingested into Grail.
To get started and create your first investigation scenario, open Security Investigator  and select
and select 
Try Security Investigator  and share your feedback to help us improve.
and share your feedback to help us improve.
Learning modules
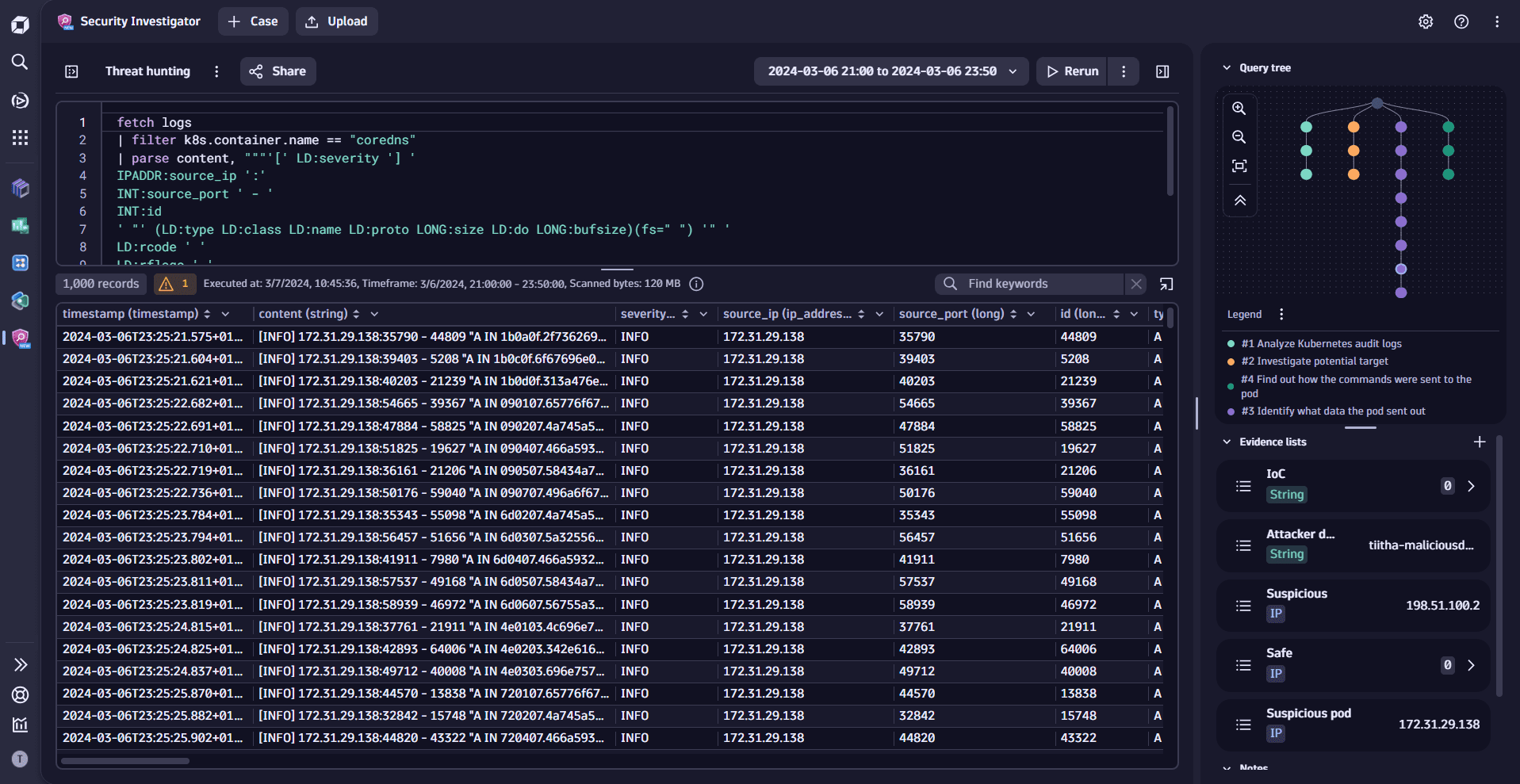
- Learn how to execute DQL queries in Security Investigator.
- Extract structured and actionable insights from your log records.
- Learn how to analyze results via filtering in Security Investigator.
- Learn how to extract fields with DPL Architect from Security Investigator.
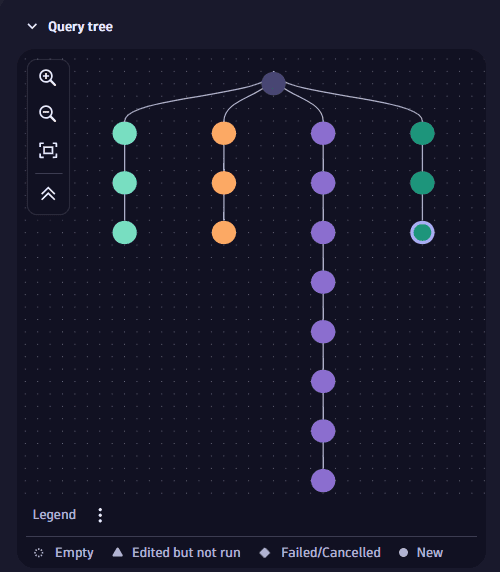
- Learn how to work with the query tree in Security Investigator.
- Learn how to define timeframes in Security Investigator.
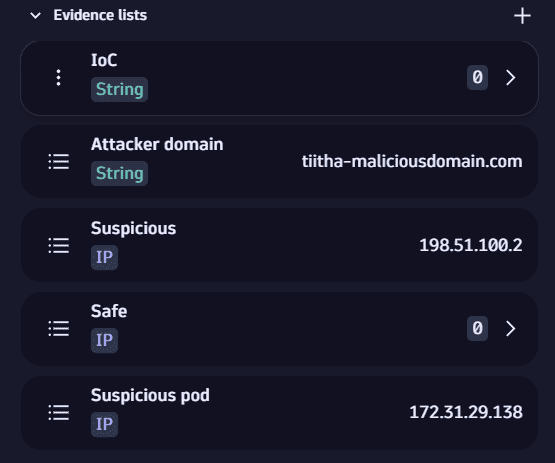
- Learn how to manage evidence in Security Investigator.
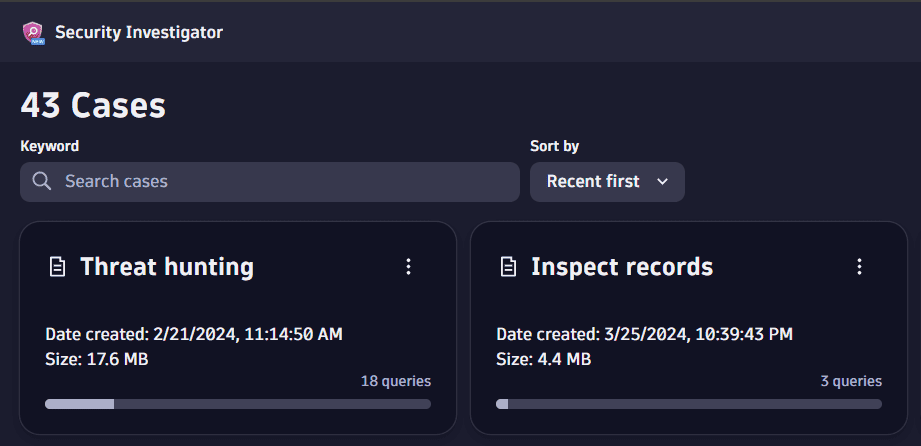
- Ways to manage cases with Security Investigator.
- Manage templates with Security Investigator.
- Learn how to collaborate with other apps from Security Investigator.