Application Security FAQ
- Latest Dynatrace
- Troubleshooting
See below for answers to some of the most frequently asked questions about Dynatrace Application Security, grouped by topics.
For troubleshooting articles related to Application Security, visit Dynatrace Community.
Detection and monitoring
How can I detect security risks?
With Dynatrace Application Security, you can not only identify and monitor vulnerabilities in applications (third-party libraries, application runtimes, custom code) in your production and pre-production environments, but also detect and block attacks on your applications automatically and in real time.
To get started, select any of the options below.
Latest Dynatrace
- To detect, prioritize, and monitor third-party, code-level, and runtime vulnerabilities, use
 Vulnerabilities.
Vulnerabilities. - To understand, triage, and investigate detection findings and alerts, use
 Threats & Exploits.
Threats & Exploits.
deprecated
- To detect and monitor third-party vulnerabilities, enable third-party vulnerability detection, then go to Third-Party Vulnerabilities (previous Dynatrace) or
 Third-Party Vulnerabilities.
Third-Party Vulnerabilities. - To detect and monitor code-level vulnerabilities, enable code-level vulnerability detection, then go to Code-Level Vulnerabilities (previous Dynatrace) or
 Code-Level Vulnerabilities.
Code-Level Vulnerabilities. - For a unified view of third-party and code-level vulnerabilities and information about host coverage, enable Runtime Vulnerability Analytics, then go to Security Overview (previous Dynatrace) or
 Security Overview.
Security Overview. - To detect and monitor attacks on vulnerabilities, enable Runtime Application Protection, then go to Attacks.
To learn more about the Runtime Vulnerability Analytics mechanism, see How it works.
What's the impact of enabling Application Security?
What should I consider before enabling Application Security? Can it impact anything?
When you enable Application Security:
- Expect some slight overhead, depending on your applications (it should be negligible in most cases).
- Be aware that Application Security consumes GiB-hours if you're using the Dynatrace Platform Subscription (DPS) licensing model, or Application Security units (ASUs) if you're using the Dynatrace classic licensing.
Can I manually start a security scan?
Does Application Security perform a scheduled job? What's the scheduled time interval? Can I manually start a security scan after deploying our changes in the environment?
There are no scheduled scans. Once you enable any Dynatrace Application Security functionality, your environment is automatically monitored for the selected functionality continuously and in real time.
Restrict permissions
How can I give someone view-only access to vulnerabilities?
Content below refers to the classic Third-Party Vulnerabilities (previous Dynatrace) or  Third-Party Vulnerabilities and Code-Level Vulnerabilities (previous Dynatrace) or
Third-Party Vulnerabilities and Code-Level Vulnerabilities (previous Dynatrace) or  Code-Level Vulnerabilities apps, which are deprecated.
Code-Level Vulnerabilities apps, which are deprecated.
To restrict specific users to view-only access, so they can view but not manage vulnerabilities, see Fine-tune permissions.
Resolution
Does Dynatrace resolve vulnerabilities?
Will Dynatrace resolve vulnerabilities or do I need to take any action to fix them?
Dynatrace Application Security does not resolve vulnerabilities. It identifies and monitors vulnerabilities in applications in your production and pre-production environments, and it helps you determine the root cause by providing rich context and information that helps you take the appropriate actions. For more information about capabilities, see
- Runtime Vulnerability Analytics: Capabilities
- Latest Dynatrace
 Vulnerabilities
Vulnerabilities
Once the root cause is gone, the vulnerability is automatically resolved. For more information about vulnerability resolution, see:
How do I fix detected vulnerabilities?
The rich and precise context and details provided on the vulnerabilities pages help you identify and understand vulnerabilities, prioritize them by risk, and automatically monitor and alert on newly discovered vulnerabilities. Based on this information, you can determine what actions are needed to fix the vulnerabilities.
For example:
Latest Dynatrace
In  Vulnerabilities, you can:
Vulnerabilities, you can:
deprecated
In Third-Party Vulnerabilities (previous Dynatrace) or  Third-Party Vulnerabilities, you can:
Third-Party Vulnerabilities, you can:
- Use the recommended fixes from Davis Security Advisor to upgrade to a non-vulnerable version of the vulnerable component
- Set up tracking links for affected entities and follow up with their remediation progress
When is a vulnerability marked as resolved?
I removed the vulnerable component, but the vulnerability still shows as open. When does it get resolved?
A vulnerability is marked as Resolved under the following conditions:
-
No process group or Kubernetes node has reported any vulnerable components for more than two hours.
-
The root cause of the vulnerability is no longer present; for example, the vulnerable component has been removed or the affected process has been terminated.
This condition applies regardless of how much time has passed since the last report.
Why is my vulnerability still open if there's no affected process group anymore?
Content below refers to the classic Third-Party Vulnerabilities (previous Dynatrace) or  Third-Party Vulnerabilities app, which is deprecated.
Third-Party Vulnerabilities app, which is deprecated.
A vulnerability is still reported if it's still present in other management zones. To see the affected process groups, select All in the management zone filter.
Can a vulnerability be resolved while there are still affected entities?
No. A vulnerability is resolved if there are no longer any affected entities.
Why are some vulnerabilities resolved without any mitigation?
After enabling Runtime Vulnerability Analytics, 19 critical vulnerabilities were found. Now they are down to three without any mitigation from our side. Why are some vulnerabilities resolved without any mitigation?
A vulnerability is resolved automatically if the root cause is no longer present. To learn more, see Third-party vulnerability resolution/Code-level vulnerability resolution.
Why do some vulnerabilities keep being resolved and reopened?
A vulnerability keeps being resolved and reopened when a process using the vulnerable library isn't running all the time:
-
When the process is terminated, the vulnerability is resolved.
-
When the process is restarted, the vulnerability is reopened.
For details about the reasons why vulnerabilities are resolved and reopened, see Resolution.
To determine which processes are affected, see:
- Latest Dynatrace What is at risk (affected and related entities)
- deprecated Remediation tracking for processes.
Why do resolved vulnerabilities show up in every management zone?
Content below refers to the classic Third-Party Vulnerabilities (previous Dynatrace) or  Third-Party Vulnerabilities app, which is deprecated.
Third-Party Vulnerabilities app, which is deprecated.
Management zone information is not directly attached to a vulnerability. It derives from the vulnerable entities that are affected by the respective vulnerability: a process in a management zone that uses a vulnerable library causes a third-party vulnerability in the respective management zone.
A vulnerability is resolved if there are no vulnerable entities anymore. In the vulnerability list, all resolved vulnerabilities displayed are not filterable by management zone anymore, as that information is not attached to them.
Why am I getting zero resolved process groups for resolved vulnerabilities in my management zone?
Content below refers to the classic Third-Party Vulnerabilities (previous Dynatrace) or  Third-Party Vulnerabilities app, which is deprecated.
Third-Party Vulnerabilities app, which is deprecated.
For resolved vulnerabilities, I would like to examine resolved process groups to understand which entities were previously affected, but there are zero resolved process groups in my management zone. Why?
On the Vulnerabilities pages, in the Process group overview section, if there are zero resolved process groups displayed for a resolved vulnerability in your management zone, it means that none of the entities that were previously affected and resolved are in that management zone. To find the respective entities, switch the management zone filter to All.
Restart required
Is restart required after enabling or disabling an Application Security feature or functionality?
See below the restart requirements by functionality.
-
Third-party vulnerabilities: An application process restart is required in the following case:
- In Discovery mode, after you enable code-module injection
-
Code-level vulnerabilities: An application process restart is required in the following cases:
- After each step in Enable code-level vulnerability detection:
- Enable Code-level Vulnerability Analytics
- Configure the global code-level vulnerability detection control per technology
- Enable OneAgent monitoring
- After you enable a monitoring rule
- After each step in Enable code-level vulnerability detection:
-
Attacks: An application process restart is required in the following cases:
- After each step in Get started with Runtima Application Protection:
- Enable Runtime Application Protection
- Define the global attack control per technology
- Enable OneAgent monitoring
- After you enable a monitoring rule
- After each step in Get started with Runtima Application Protection:
Why is there a "Restart required" notification on some Application Security pages?
Content below refers to the classic Third-Party Vulnerabilities (previous Dynatrace) or  Third-Party Vulnerabilities app, which is deprecated.
Third-Party Vulnerabilities app, which is deprecated.
OneAgent version 1.279+
See How can I know if information about vulnerable functions is outdated and what can I do about it?.
Notifications
How can I get notifications for vulnerabilities open for a long time?
To configure Dynatrace to send notifications on your desired channels, you can:
Latest Dynatrace
Set up a workflow to create and automate notifications, allowing you to control this aspect more granularly.
- For examples of how to set up a workflow, see Workflows use cases.
deprecated
- Vulnerability (re)opened (alerts when vulnerability is reopened)
- New Management zone affected (alerts whenever a new process group in a management zone is affected by the vulnerability)
How can I stop receiving notifications for an irrelevant vulnerability or entity?
If you think a vulnerability or an entity isn't relevant or is a false positive, you can:
Latest Dynatrace
Mute (silence) all its affected entities. This sets the vulnerability status to Muted. For instructions, see Change the affected entity status.
deprecated
- Mute (silence) the vulnerability. For details, see Change the third-party vulnerability status and Change the code-level vulnerability status
- Mute (silence) the entity. For details, see Change vulnerability status of process groups and Change vulnerability status of nodes.
Why do we keep receiving notifications for the same vulnerability?
Every day we receive notifications for the same vulnerability ID, with the same process group, entity name, and entity link. We have other vulnerabilities detected, but no extra notifications are sent. Why do we keep receiving notifications for the same vulnerability?
A process that does not run all the time might be using a vulnerable library. For details, see Why do some vulnerabilities keep being resolved and reopened?. To stop receiving notifications for this vulnerability, you can:
- Exclude the respective process from Application Security monitoring by setting up a third-party monitoring rule/code-level monitoring rule.
- Latest Dynatrace Mute (silence) all the vulnerability's affected entities. This sets the vulnerability status to
Muted. For instructions, see Change the affected entity status. - deprecated Mute (silence) the vulnerability. For details, see Change the third-party vulnerability status and Change the code-level vulnerability status
Reporting
How can I export and share a vulnerability report?
Can I export a report with the vulnerability information so I can share it with developers?
Create reports
Latest Dynatrace
- In
 Vulnerabilities, you can download data in the vulnerabilities table as a CSV file. For instructions, see Download vulnerability data as CSV.
Vulnerabilities, you can download data in the vulnerabilities table as a CSV file. For instructions, see Download vulnerability data as CSV. - You can query state reports with Dynatrace Query Language (DQL), then create dashboards. For reference, see Example query.
deprecated
-
With the Dynatrace API, you can chart Application Security metrics and pin them to your dashboard. For example, you can retrieve all security problems detected in your applications or the vulnerable functions of a security problem.
-
With Data Explorer, you can share your metric results and export them to a CSV file.
Set up notifications
-
Latest Dynatrace You can create and automate notifications for vulnerabilities on your desired channels by setting up workflows. For examples of how to set up a workflow, see Workflows use cases.
-
deprecated With notification alerts, you can keep track of all the vulnerabilities in your environment.
Host coverage
How can I see which hosts are covered by Application Security?
Content below refers to the classic Security Overview (previous Dynatrace) or  Security Overview app, which is deprecated. A ready-made dashboard will soon be available in the latest Dynatrace experience to help you stay ahead of your vulnerability posture, including process and host coverage, scan activity, and the evolution of vulnerability findings. Stay tuned!
Security Overview app, which is deprecated. A ready-made dashboard will soon be available in the latest Dynatrace experience to help you stay ahead of your vulnerability posture, including process and host coverage, scan activity, and the evolution of vulnerability findings. Stay tuned!
Go to Security Overview (previous Dynatrace) or  Security Overview. In the Host coverage section, select Monitored hosts to go to the Hosts page filtered by monitored hosts. For details, see Application Security overview: Host coverage.
Security Overview. In the Host coverage section, select Monitored hosts to go to the Hosts page filtered by monitored hosts. For details, see Application Security overview: Host coverage.
Limit monitoring
How can I limit Application Security monitoring to a specific management zone?
Content below refers to the classic Security Overview (previous Dynatrace) or  Security Overview app, which is deprecated.
Security Overview app, which is deprecated.
Create a monitoring rule that says Do not monitor if the management zone does not equal <your-management-zone>. After you add, edit, or remove a rule, allow up to 15 minutes for your changes to take effect.
How can I exclude hosts, management zones, process groups, or processes from monitoring with Application Security?
Content below refers to the classic Security Overview (previous Dynatrace) or  Security Overview app, which is deprecated.
Security Overview app, which is deprecated.
-
For third-party vulnerabilities, you can create monitoring rules to exclude specific hosts, management zones, or processes from monitoring.
-
For code-level vulnerabilities, you can create monitoring rules to exclude specific process groups from monitoring.
Change status
If a vulnerability is muted, are the affected entities muted as well?
No. The MUTE state does not automatically transfer to its affected entities; there is no interdependence between the two when assessing this state.
Latest Dynatrace In  Vulnerabilities, a vulnerability is only muted if all its affected entities are muted. For details, see Change the mute status of affected entities.
Vulnerabilities, a vulnerability is only muted if all its affected entities are muted. For details, see Change the mute status of affected entities.
Status updates
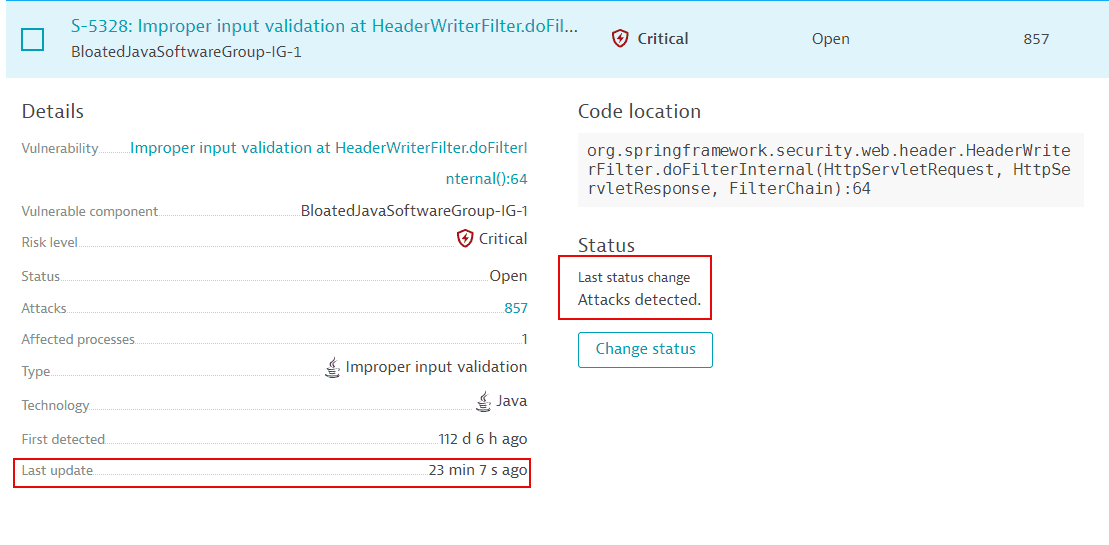
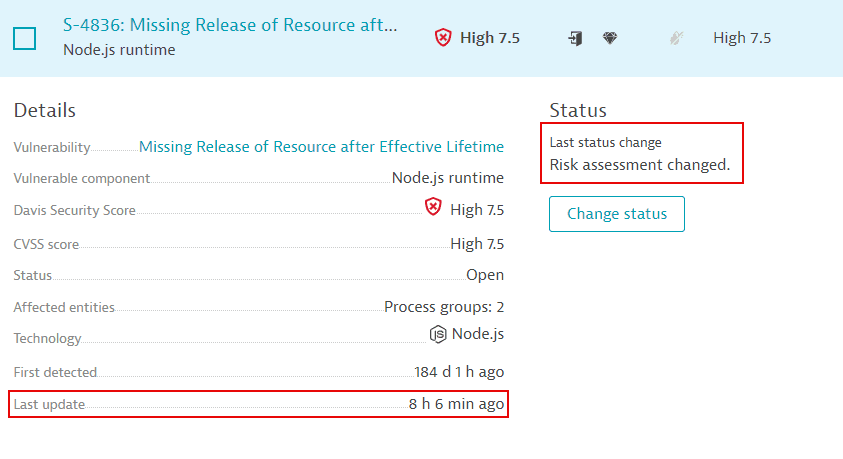
What does "last update" on vulnerabilities list pages refer to?
Content below refers to the classic Third-Party Vulnerabilities (previous Dynatrace) or  Third-Party Vulnerabilities and Code-Level Vulnerabilities (previous Dynatrace) or
Third-Party Vulnerabilities and Code-Level Vulnerabilities (previous Dynatrace) or  Code-Level Vulnerabilities apps, which are deprecated.
Code-Level Vulnerabilities apps, which are deprecated.
On the third-party and code-level vulnerabilities list pages, does "Last update" refer to the last time when Dynatrace provided an update? How can I request an update for a vulnerability which was last updated two days ago?
Last update refers to the last time when a vulnerability had a status change. It does not refer to the last time when Dynatrace provided an update. For details, see FAQ: Can I manually start a security scan?.
What are status changes
A status change can be when:
- The vulnerability is resolved or reopened
- The vulnerability is muted or unmuted
- The number of affected process groups has decreased or increased
- The risk assessment has changed
- The Davis Security Score has changed
- A new software component is detected
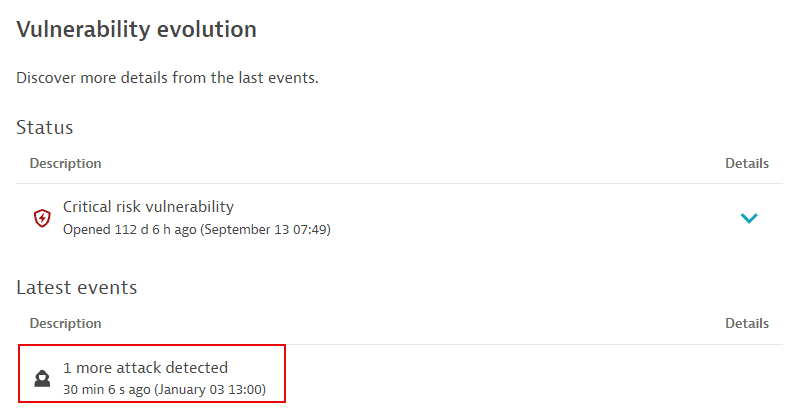
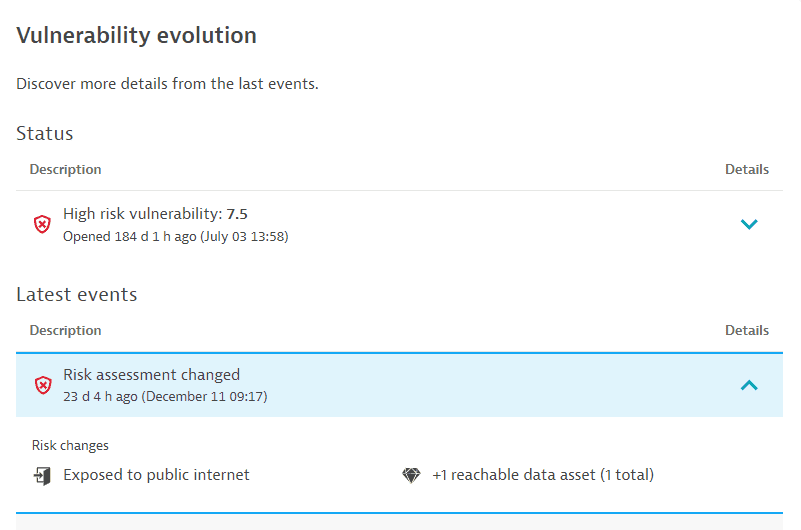
In the example below, it's been eight hours and six minutes since the risk assessment changed.
You can find details about the status change on the vulnerability details page, under Vulnerability evolution > Latest events.
Different values
Why are there different values on the vulnerabilities page versus Data Explorer?
Content below refers to the classic Third-Party Vulnerabilities (previous Dynatrace) or  Third-Party Vulnerabilities app, which is deprecated.
Third-Party Vulnerabilities app, which is deprecated.
In Third-Party Vulnerabilities (previous Dynatrace) or  Third-Party Vulnerabilities, on the Third-party vulnerabilities list page, when I filter for resolved vulnerabilities over the last seven days, I get
Third-Party Vulnerabilities, on the Third-party vulnerabilities list page, when I filter for resolved vulnerabilities over the last seven days, I get 3 vulnerabilities. When I use the metric query (builtin:security.securityProblem.resolved.new.global) in Data Explorer, I get 25. Why are there different values on the vulnerabilities page versus Data Explorer?
The vulnerability list shows the current state (the total count of vulnerabilities that are currently resolved), while using the metric query in Data Explorer shows the change over time.
For example, if two vulnerabilities are open and resolved several times over a period of time, the Data Explorer chart shows only one spike (which is the maximum over the given timeframe) while the vulnerabilities page shows two (because there are currently two resolved vulnerabilities).
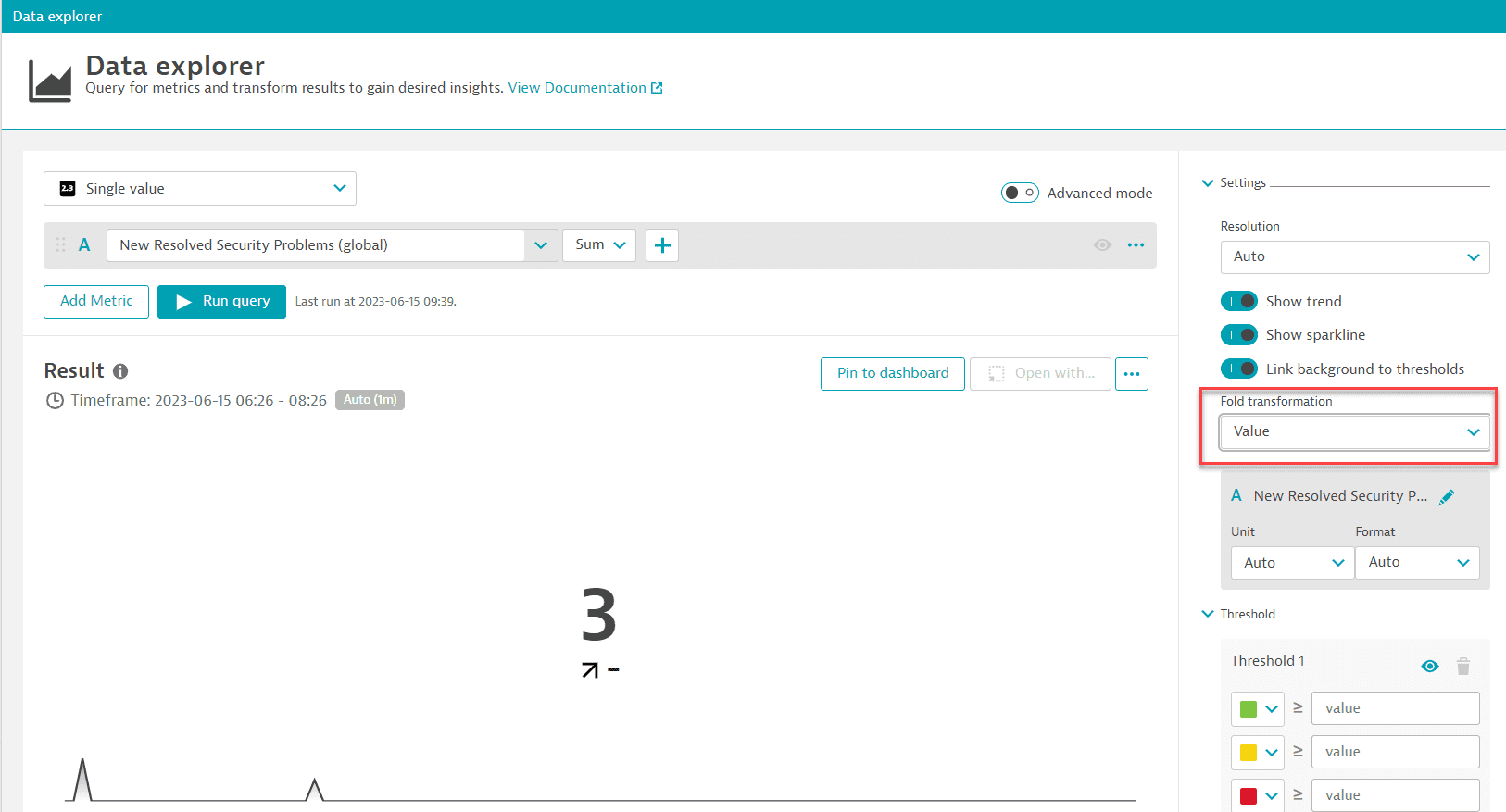
To find out how many vulnerabilities were resolved in the given timeframe using the metric query
-
In Data Explorer, set the visualization type to
Single value. -
Expand Settings and set Fold transformation to
Value.This shows how many times the vulnerabilities were resolved during the selected timeframe.
Why are there different values on the Third-party vulnerabilities and vulnerability details pages?
Content below refers to the classic Third-Party Vulnerabilities (previous Dynatrace) or  Third-Party Vulnerabilities app, which is deprecated.
Third-Party Vulnerabilities app, which is deprecated.
There can be two reasons why values on these pages don't match:
Different number of affected entities
In Third-Party Vulnerabilities (previous Dynatrace) or  Third-Party Vulnerabilities, the number of affected entities (process groups or hosts) on the Third-party vulnerabilities page (in the Affected entities column for a specific vulnerability) may differ from the number of affected entities on the vulnerability details page for the following reasons:
Third-Party Vulnerabilities, the number of affected entities (process groups or hosts) on the Third-party vulnerabilities page (in the Affected entities column for a specific vulnerability) may differ from the number of affected entities on the vulnerability details page for the following reasons:
-
On the Third-party vulnerabilities page:
-
Affected entities aren't filtered by management zone.
-
Calculations take place every 15 minutes.
-
-
On the vulnerability details page:
-
Affected entities are filtered by management zone.
-
Current data is considered.
-
Different risk factors
In Third-Party Vulnerabilities (previous Dynatrace) or  Third-Party Vulnerabilities, the assessment of risk factors (
Third-Party Vulnerabilities, the assessment of risk factors (Public exploit, Public internet exposure, Reachable data assets, Vulnerable functions in use) in the infographic on the vulnerability details page and the Davis Security Score column on the Third-party vulnerabilities page may be different from the assessment of risk factors on the vulnerability details page (in the Vulnerability details section) for the following reason:
For the infographic on the vulnerability details page and the Davis Security Score column on the Third-party vulnerabilities page, calculations take place every 15 minutes For the Vulnerability details section on the vulnerability details page, current data is considered.
Why does my vulnerability have a different risk assessment and DSS than its affected entities?
A vulnerability is an aggregation of all its affected entities in your environment; therefore, it can have different values (risk assessment and DSS) than its affected entities. For example, the risk score of an affected entity might be 8.0, while the score of the aggregated vulnerability is 9.0. At the same time, if at least one affected entity is exposed to the internet, the aggregated vulnerability is also exposed to the internet.
Latest Dynatrace In  Vulnerabilities, the DSS score is the maximum DSS score of the affected entities. For details, see Calculation differences.
Vulnerabilities, the DSS score is the maximum DSS score of the affected entities. For details, see Calculation differences.
Why am I seeing different vulnerabilities in production vs non-production environment?
You have the same vulnerabilities in two environments only if all of the following are the same in both environments:
- Deployment (including the OneAgent version)
- Settings
- Application usage
- Traffic
Why does the number of vulnerabilities differ between the classic apps and the Vulnerabilities app?
The total number of vulnerabilities shown in  Vulnerabilities may differ slightly from the counts in the classic apps (Third-party vulnerabilities and Code-level vulnerabilities). This difference stems from several backend-related factors:
Vulnerabilities may differ slightly from the counts in the classic apps (Third-party vulnerabilities and Code-level vulnerabilities). This difference stems from several backend-related factors:
-
Timing: State report exports can take up to 15 minutes. As a result, vulnerabilities may appear or disappear with a delay in
 Vulnerabilities.
Vulnerabilities. -
Muting: Muted vulnerabilities are excluded from the reported vulnerabilities detected count in the classic apps. To view them, you need to apply a filter for muted vulnerabilities or refer to the summary panel.
-
Timeframe: The default timeframe for
 Vulnerabilities is 30 minutes, whereas the classic apps use a 2-hour default timeframe.
Vulnerabilities is 30 minutes, whereas the classic apps use a 2-hour default timeframe.
We recommend using the  Vulnerabilities as your primary interface for managing vulnerabilities. It reflects the latest detection logic, is actively maintained, and continues to evolve. The classic views are planned to be phased out for SaaS customers in the coming years.
Vulnerabilities as your primary interface for managing vulnerabilities. It reflects the latest detection logic, is actively maintained, and continues to evolve. The classic views are planned to be phased out for SaaS customers in the coming years.
Public internet exposure
How is public internet exposure determined?
On Linux hosts, if there's no information, which can happen in different monitoring modes or because something went wrong, public internet exposure is detected via eBPF. Potential states are Public network and Not detected.
To determine public internet exposure, Dynatrace:
- Evaluates all the IP addresses detected in the last hour.
- Discards the private IP ranges.
- Groups the remaining IPs by subnet.
As soon as the respective subnets reach a certain (low) threshold, public internet exposure is triggered.
Vulnerable libraries
Does Dynatrace detect vulnerable libraries that aren't in use?
Runtime Vulnerability Analytics focuses on the runtime aspect, aiming to provide a prioritized list of vulnerabilities that are relevant to your running environments. For this purpose, Dynatrace only reports libraries that are actively used.
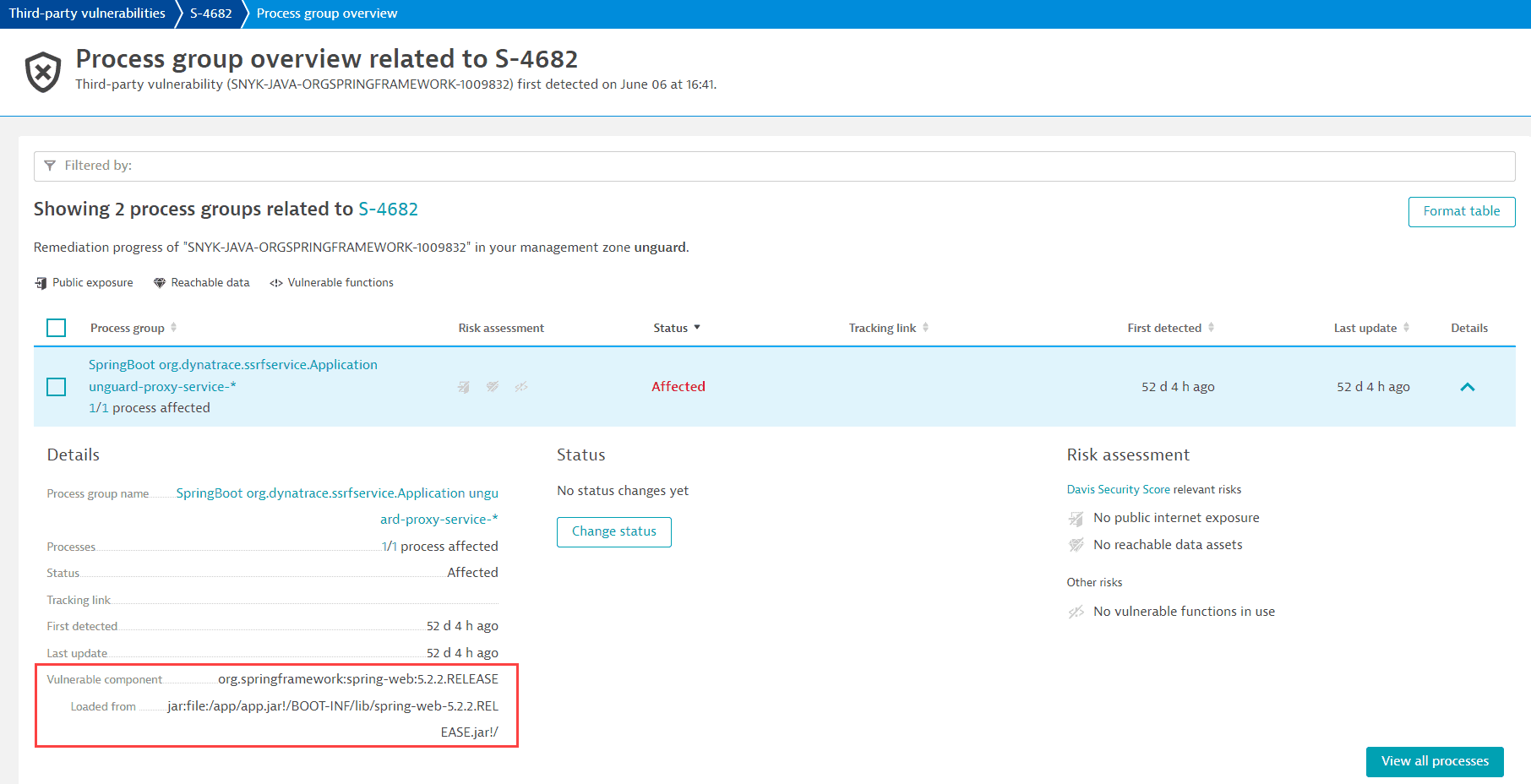
Where can I see the origin of a vulnerable library?
Content below refers to the classic Third-Party Vulnerabilities (previous Dynatrace) or  Third-Party Vulnerabilities app, which is deprecated.
Third-Party Vulnerabilities app, which is deprecated.
On the remediation tracking pages for process groups and processes affected by a vulnerability, you can see where the software component has been loaded from.
This feature is displayed for vulnerable Java, .NET, Node.js, Python, and Go software components.
Note that to display the origin of .NET software components, the minimum OneAgent version required is OneAgent version 1.301+.
Example:
For information on how to navigate there, see Remediation tracking.
Vulnerable functions
How are vulnerable functions determined?
-
If the Snyk feed provides information about the vulnerable function, and OneAgent monitoring for Java vulnerable functions is enabled, OneAgent determines whether the vulnerable function is in use.
-
If the Snyk feed provides information about the vulnerable function, but the OneAgent feature is disabled, the number of vulnerable functions is displayed as Not available.
Why is there no information on vulnerable functions?
There are two cases when information about vulnerable functions is not available:
- If no vulnerable function information is provided by Snyk or the Dynatrace security research team.
- For runtime vulnerabilities, which are based on the NVD feed.
Why is there no data available for vulnerable functions?
-
Once you enable Third-party Vulnerability Analytics, it will take some time (one hour at the most) until data about vulnerable functions is displayed.
-
OneAgent monitoring for Java vulnerable functions is disabled. To enable it, see Enable OneAgent monitoring for Java vulnerable functions.
The OneAgent feature must be enabled for all processes affected by the vulnerability. For instructions on how to enable OneAgent monitoring, see Enable OneAgent monitoring for Java vulnerable functions.
-
No vulnerable functions of the vulnerability are contained in the release version of the third-party libraries (software components) in use.
-
No vulnerable functions are provided by the Snyk feed.
-
deprecated You need to restart the processes affected by the vulnerability for updated information. For details, see FAQ: How can I know if information about vulnerable functions is outdated and what can I do about it?.
How do I know which processes to restart?
Content below refers to the classic Third-Party Vulnerabilities (previous Dynatrace) or  Third-Party Vulnerabilities app, which is deprecated.
Third-Party Vulnerabilities app, which is deprecated.
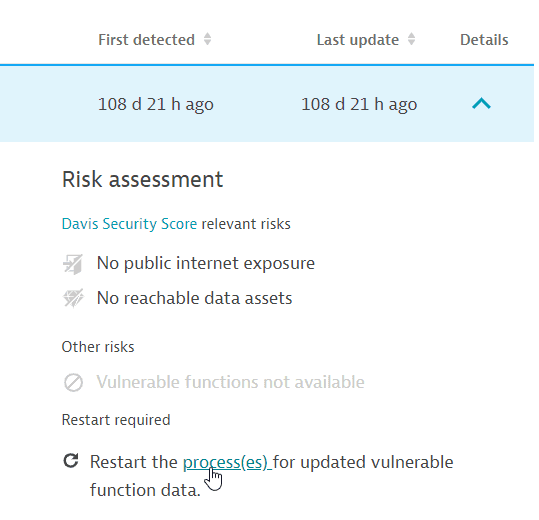
If you see the Restart required notification on the details page of a vulnerability, follow the steps below to determine which processes you need to restart:
- On the Process group overview card, select View all process groups.
- Filter by
Vulnerable functions: Restart required. - For each of the resulting process groups, select Details, then select the link provided in the Restart required notification to navigate to the list of processes that require a restart.
Example result:
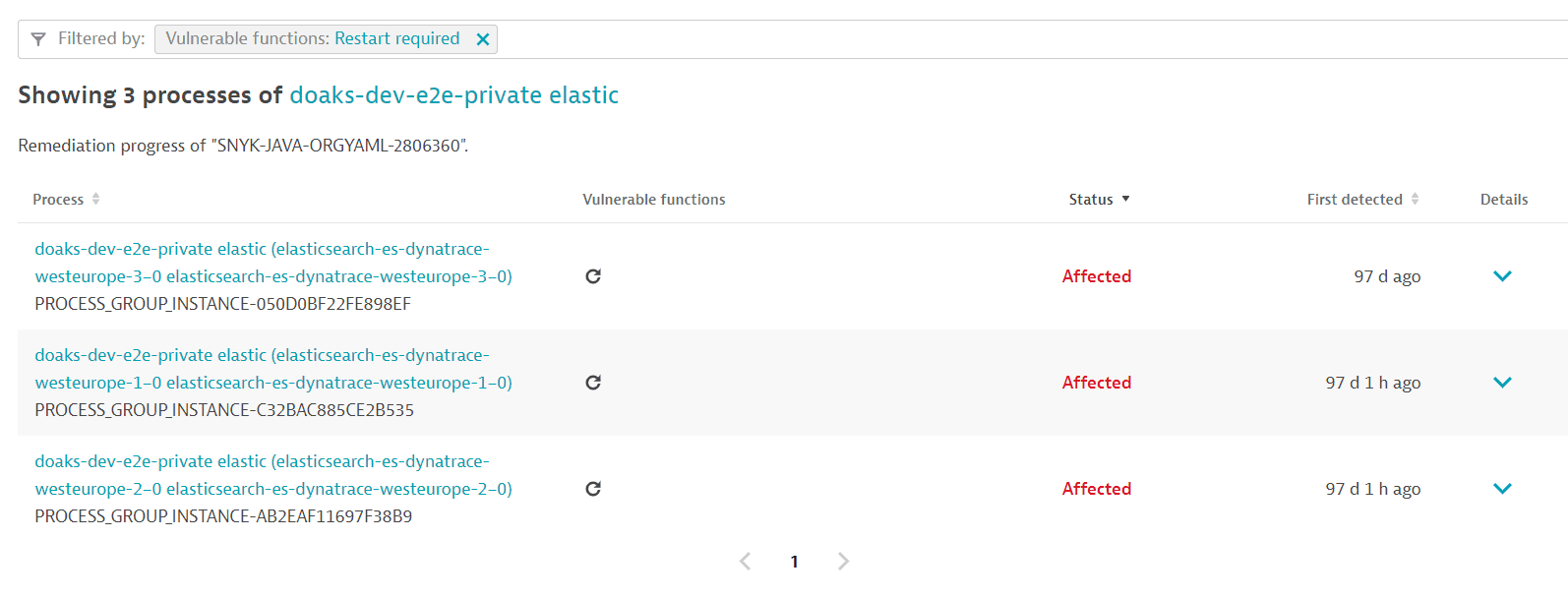
After a process restart, it takes about a minute for the updated information to be displayed.
This feature only works if OneAgent monitoring for Java vulnerable functions is enabled.
Why does my process still need to be restarted after I already restarted it?
Content below refers to the classic Third-Party Vulnerabilities (previous Dynatrace) or  Third-Party Vulnerabilities app, which is deprecated.
Third-Party Vulnerabilities app, which is deprecated.
If you followed the instructions to identify the process and restarted it, and the process still requires a restart (the same Restart required notification shows up, and the information about vulnerable functions is unchanged), this can happen in Kubernetes deployments if there's no persistent storage.
To fix this issue, add persistent storage by mounting file storage that isn't deleted when restarting your pods.
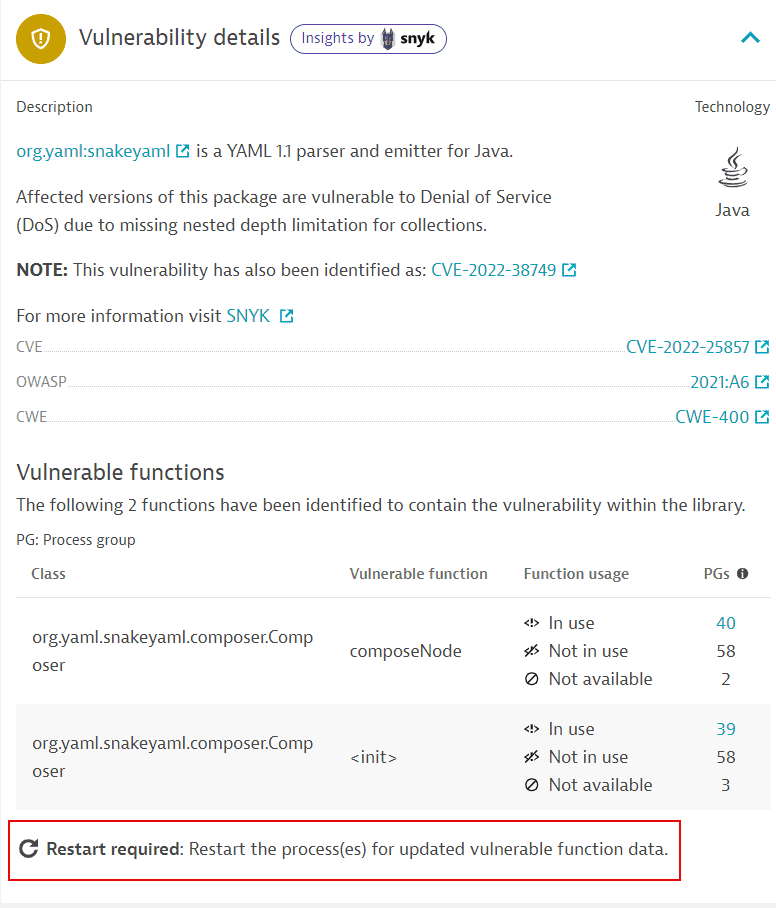
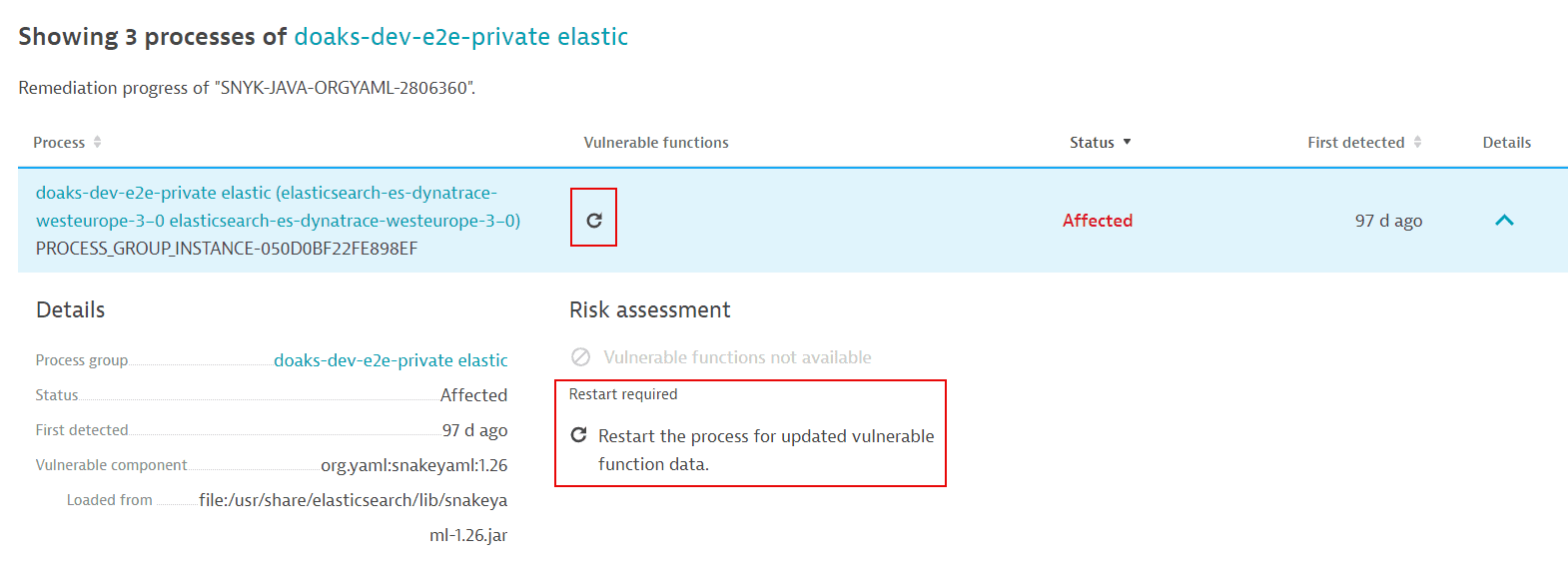
How can I know if information about vulnerable functions is outdated and what can I do about it?
Content below refers to the classic Third-Party Vulnerabilities (previous Dynatrace) or  Third-Party Vulnerabilities app, which is deprecated.
Third-Party Vulnerabilities app, which is deprecated.
OneAgent version 1.279+
If new information about a vulnerability's vulnerable functions is available, a process restart is required so that OneAgent can pick up and use the new data. In this case, a Restart required notification or symbol is displayed on
-
A vulnerability's details page (in Vulnerability details > Vulnerable functions)
-
The process groups overview related to a vulnerability (in Details > Risk assessment)
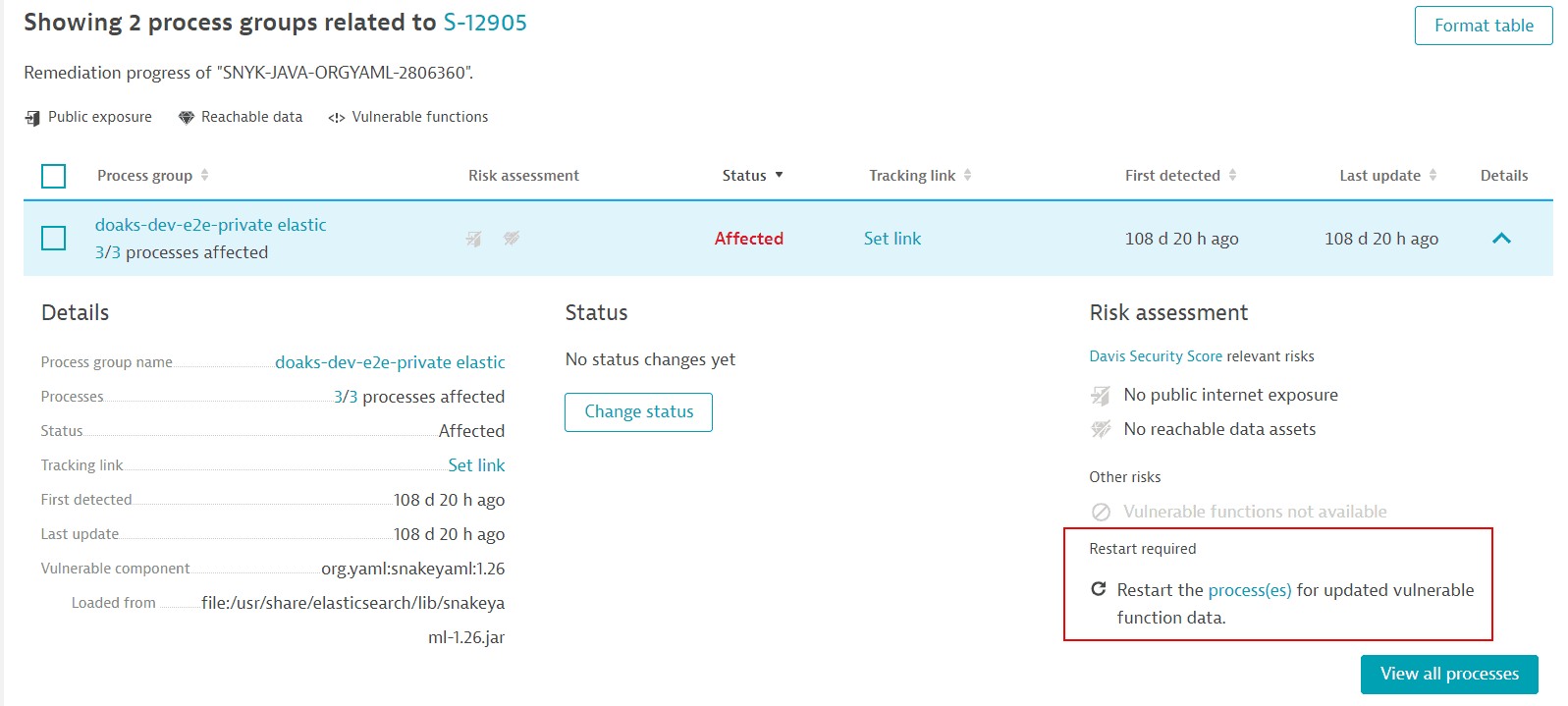
-
The process list related to a vulnerability (in Vulnerable functions and Details).
Snyk feed
Why is the Snyk link missing for some vulnerabilities?
Why don't some vulnerabilities contain a link to Snyk, even though I can find the same CVE in Snyk?
To fetch data about vulnerabilities, Dynatrace Application Security uses either Snyk or NVD, depending on the vulnerable component.
A vulnerability with a CVE that is listed in Snyk but that doesn't have any Snyk-related information in Dynatrace is using the NVD feed. For more information, see Third-party vulnerability feeds.
Attacks
How does Dynatrace actually block attacks?
Selecting Block attack for an attack doesn't automatically block the respective attack; it takes you to the Settings page where you can create a monitoring rule to block that attack in the future. Dynatrace is configured to block future exploit situations, not the current ones.
The request (thread) with the exploit throws an exception in the running code. All other users who aren't attacking are unaffected.
Dynatrace detects when a user-supplied attack payload finds its way to a line of code that uses an insecure way of
- Talking to the database (SQL injection)
- Talking to the operating system (command injection)
- Doing a JNDI lookup (JNDI injection, such as Log4Shell)
- Doing a HTTP request (SSRF)
The vulnerability is identified with or without an attack. If the data sent by the client includes characteristics of an attack that reaches this line of code, it's deemed an exploit, and Dynatrace alerts or blocks it.
To learn more about the Runtime Application Protection mechanism, see How it works.
How is an attacker's IP determined?
In Runtime Application Protection, to determine an attacker's IP, Dynatrace verifies
- Specific HTTP headers, such as
X-Client-IPorX-Forwarded-For.
-
The client IP of the socket connection (if the HTTP headers mentioned above aren't available).
For details, see Client IP address detection.
Data retention
What's the data retention period for vulnerabilities, events, and attacks?
For information about how security-related data is stored in Dynatrace, see Data retention periods.
Consumption
How can I check which hosts consume DPS/ASUs and how much they consume?
Find the hosts consuming DPS/ASUs
In Security Overview (previous Dynatrace) or  Security Overview, go to the Host coverage section for third-party and code-level vulnerabilities and select Monitored hosts. The resulting list of hosts are the hosts in your environment which consume DPS/ASUs.
For more information, see Host coverage.
Security Overview, go to the Host coverage section for third-party and code-level vulnerabilities and select Monitored hosts. The resulting list of hosts are the hosts in your environment which consume DPS/ASUs.
For more information, see Host coverage.
Find out how much your hosts consume
- If you're using Dynatrace Platform Subscription, see Analyze consumption via built-in usage metrics.
- If you're using Dynatrace classic licensing, see How capabilities affect monitoring consumption.