Gain insights
- Latest Dynatrace
- How-to guide
On the Assessment results page, selecting a rule opens a side window that enables you to:
Review key information:
Initiate deeper analysis:
This context can help you fix issues on your system.
Insights about the rule
On the Rule details tab, you can
-
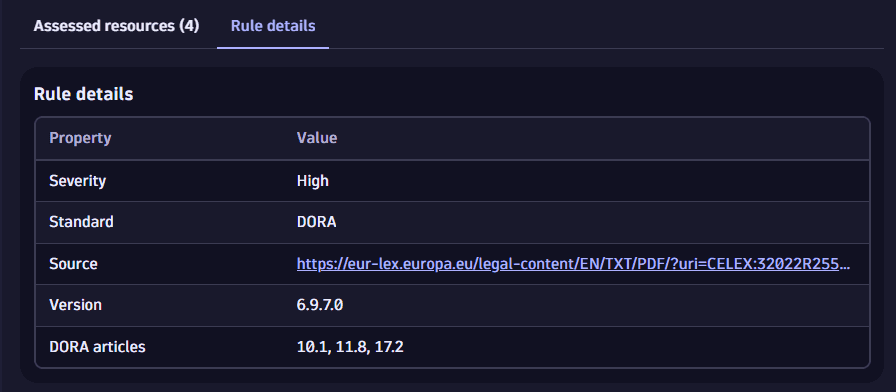
View relevant details about the rule such as
- Rule version used for assessment
- Rule severity
- Compliance standard issuing the rule
-
Navigate to the original documentation resource for the full description of the rule
Insights about resources
On the Assessed resources tab, you can examine the resources that must comply to the rule. This can help you identify the resources affected by a compliance violation or by security relevant misconfiguration.
Assessed resources with Not relevant status are filtered out by default.
You can
-
View the system on which the rule applies together with all the system resources
-
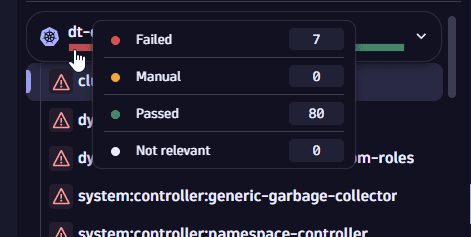
Use the filter bar to filter for resources that
- Require your attention (
Failed) - Are compliant (
Passed) - Can't be automatically assessed (
Manual) - Don't meet a specific criteria for the rule assessment (
Not relevant)
- Require your attention (
-
Use the search bar to search for a specific resource (full or partial match)
-
Hover over the system chart bar to see the compliance status of the system resources
-
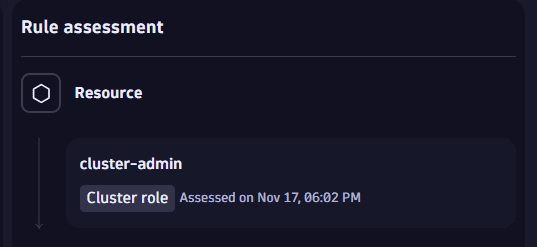
Identify the resource type and last assessment date in Rule assessment > Resource
Insights about configuration
On the Assessed resources tab, go to Rule assessment > Relevant configuration properties for information about resource configuration.
This can help you identify the current misconfiguration for a selected resource that is contributing to a rule violation.
-
Example: A
Failedrule1.2.19 Ensure that the --audit-log-maxsize argument is set to 100 or as appropriatereports that a node on the control plane doesn't have--audit-log-maxsizeconfigured. This means that, in case security investigation would be needed, it's not guaranteed that there will be enough logs to carry out investigation due to this misconfiguration.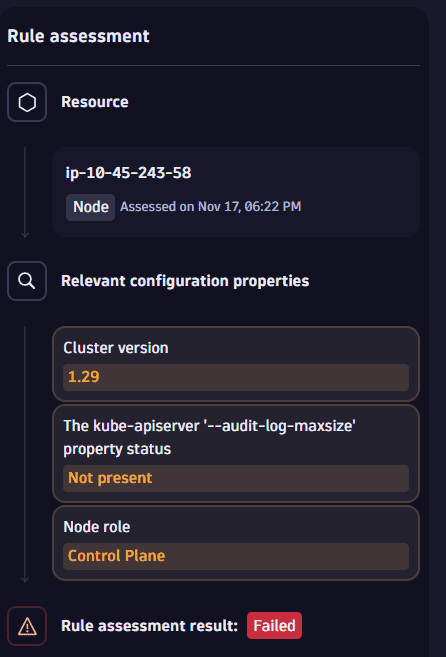
For Manual rules, where automatic assessment isn't possible, hints are provided about what information is needed to complete the assessment.
For details about manual rules, see Results.
-
Example: A
ManualruleThe Kubernetes kubelet staticPodPath must not enable static podsreports that Dynatrace can't check configuration because Kubernetes Node Configuration Collector is missing.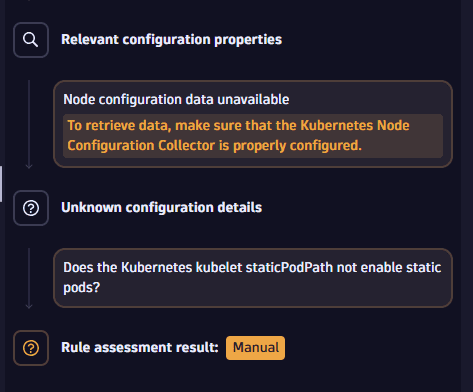
Explain assessment
To use this generative AI feature, make sure:
- Dynatrace Intelligence generative AI is enabled for your environment. See Enable Dynatrace Intelligence generative AI.
- You have permission to use it. See User permissions.
Dynatrace Intelligence generative AI can provide contextual, plain-language explanations of rule assessments to accelerate understanding and remediation.
To access the functionality
- In
 Security Posture Management, on the Assessment results page, select a rule.
Security Posture Management, on the Assessment results page, select a rule. - On the Assessed resources tab, select Explain assessment.
When selected, Dynatrace Intelligence generative AI analyzes the technical details of a rule assessment and generates a structured summary that may include:
- What the assessment means: Explains the compliance rule (for example, CIS Kubernetes Benchmark requirements) and its purpose in securing environments.
- Why it matters: Highlights severity levels and priority, and describes potential implications such as misconfigurations leading to unauthorized access, privilege escalation, or cluster compromise.
- How to remediate: Where applicable, recommends remediation steps such as updating file permissions, applying configuration fixes, restarting services, or enabling continuous monitoring across clusters and cloud accounts.
The structure and depth of generative AI's explanation may vary depending on the rule type and available context. While Dynatrace Intelligence generative AI aims to provide detailed insights, not all assessments will include every element listed above.
Dynatrace Intelligence generative AI explanations are tailored to the nature of each rule assessment, providing relevant, actionable insights that accelerate triage and support informed decision-making, even for users without deep security expertise.