Okta SAML configuration for Dynatrace
- Latest Dynatrace
- How-to guide
- 7-min read
- Published Jul 22, 2019
Depending on your federation scope, follow one of the two procedures below to configure Okta as the SAML identity provider (IdP) for Dynatrace SSO.
This page describes the IdP (Okta) end of your SAML SSO configuration, not the Dynatrace end. Use it as part of the entire SAML configuration procedure for Dynatrace SaaS if you're using Okta.
While we do our best to provide you with current information, Dynatrace has no control over changes that may be made by third-party providers. Always refer to official third-party documentation from your IdP as your primary source of information for third-party products.
Choose a configuration procedure
Choose a configuration procedure based on your federation scope.
My federation scope
Procedure to follow for Okta IdP configuration
global
Both procedures work for global federations. Choose one.
account
- Okta manual configuration Required
environment
- Okta manual configuration Required
I'm not sure
- Okta manual configuration Recommended
Okta Network Integration configuration
Through the Okta Integration Network, you can use an Okta-verified, pre-built configuration to integrate Dynatrace with your Okta IdP for SSO.
This procedure works only for configuring Dynatrace global federation with Okta as your IdP.
-
In the Okta interface, select Application from the main menu and select Add Application.
-
Search for Dynatrace and select Add.
-
Select Next.
-
In Sign On Methods, select SAML 2.0.
-
Optional Set Default Relay State to your default tenant URL or to other Dynatrace services from the
*.dynatrace.comrealm. If this is not defined, users after signing in will be redirected to the last accessed tenant or account/user profile. -
Optional Set role as a Security group claim attribute. If configured, Okta will send assigned groups within the SAML Request.
To manage group membership in Okta with SAML Authorization in Dynatrace, this must be configured.
- For more about SAML metadata configuration, see Configure metadata.
- You can configure Security Group Claim attribute filtering using Okta's proprietary expression language. For example, set role to
Matches regexand enter.*as the value to have all groups assigned to the user sent with the SAML request.
-
Optional Select Enable Single Logout and upload a certificate (Browse and Upload) to enable global single logout. The certificate is provided in Okta's Dynatrace configuration. You need to be signed into the Okta Admin Dashboard.
Okta manual configuration
This section describes how to manually configure Okta as your IdP for all Dynatrace federation scopes (global, account, and environment).
This procedure works for all Dynatrace federation scopes (global, account, and environment) when using Okta as your IdP.
-
Download your Dynatrace federation Service Provider metadata XML file.
- This file contains configuration properties that you'll have to set in the Okta configuration in the following steps.
- This file is common for global-scoped federations, but it's unique for account-scoped and environment-scoped federations.
-
In the General settings, you define the basic properties for your configuration. They describe the connection between your Okta Identity Provider (IdP) and Dynatrace.
It's important to use values from the Dynatrace Service Provider metadata XML file you downloaded in the first step. Set properties as described below.
'General' - values
Property
Value
Notes
Single sign on URL
Locationattribute value ofAssertionConsumerServiceXML node in your Dynatrace Service Provider metadata- Use this for Recipient URL and Destination URL is
selected. - Allow this app to request other SSO URLs is
not selected.
Audience URI (SP Entity ID)
entityIDattribute value ofEntityDescriptorXML node in your Dynatrace Service Provider metadataName ID format
EmailAddressApplication username
EmailUpdate application username on
Create and update - Use this for Recipient URL and Destination URL is
-
Select
Show Advanced Settings. Set properties as described below:'Advanced settings' - values
Property
Value
Notes
Response
Signed(required)The entire SAML message must be signed (signing only SAML assertions is insufficient and generates a 400 Bad Request response).
Assertion Signature
Signed(optional)Dynatrace ignore assertions signatures
Signature Algorithm
RSA-SHA256Digest Algorithm
SHA256Assertion Encryption
Unencrypted(required)Enable Single Logout and Single Logout URL
If you want to enable single logout service with Dynatrace SSO:
- Select Enable Single Logout
- Enter a Single Logout URL:
Locationattribute value ofSingleLogoutServiceXML node in your Dynatrace Service Provider metadata
There are two
SingleLogoutServiceXML nodes in your Dynatrace Service Provider metadata (forHTTP-POSTandHTTP-Redirectbindings). They have the sameLocationattribute value set, so it doesn't matter which one you use.SP Issuer
entityIDattribute value ofEntityDescriptorXML node in your Dynatrace Service Provider metadataThe value is the same as for
Audience URI (SP Entity ID)from theGeneralconfiguration stepSignature Certificate
Certificate from
X509CertificateXML node value in your Dynatrace Service Provider metadata XML file. It must be an X509Certificate file wrapped with a header.If your Dynatrace Service Provider metadata XML file contains two certificates, choose the certificate having
KeyNameequalsDynatrace Certificate 2023.The certificate file required by Okta for SSO application configuration can be converted from an X509Certificate using, for instance, this online tool. The result should be just an X509Certificate wrapped with a header.
-
Configure attribute statements to enable SAML authorization in Dynatrace SSO.
- In the Attribute Statements section, add entries for first name and last name.
- In the Group Attribute Statements section, add an entry to enable mapping of groups between the Okta IdP and Dynatrace SSO.
Values displayed here are only examples.
Okta: Attribute Statements and Group Attribute Statements - example screen
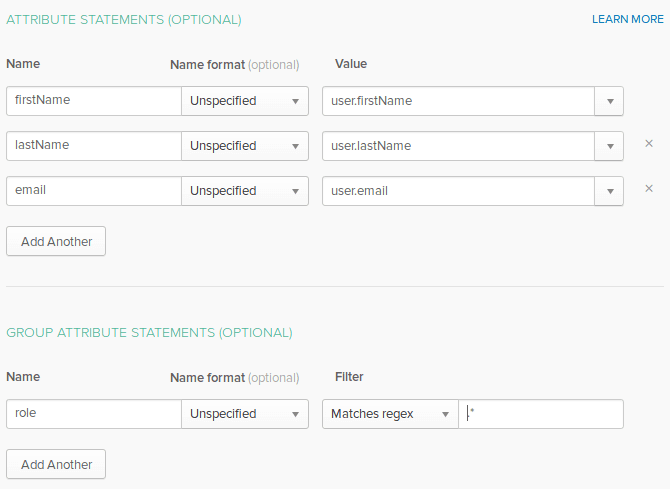
Attribute names need to match the Dynatrace federated attribute values on the Dynatrace Single sign-on page:
First name attributeLast name attributeSAML Group attribute
You can configure Group Attribute Statements filtering using Okta's proprietary expression language. For example,
.*means that all groups assigned to the user will be sent with the SAML request.