AD FS SAML configuration for Dynatrace
- Latest Dynatrace
- How-to guide
- 3-min read
- Published Jul 22, 2019
Follow the examples below to configure Active Directory Federation Services (AD FS) as the SAML identity provider (IdP) for Dynatrace SSO.
This page describes the IdP (AD FS) end of your SAML SSO configuration, not the Dynatrace end. Use it as part of the entire SAML configuration procedure for Dynatrace SaaS if you're using AD FS.
While we do our best to provide you with current information, Dynatrace has no control over changes that may be made by third-party providers. Always refer to official third-party documentation from your IdP as your primary source of information for third-party products.
Specify the metadata
-
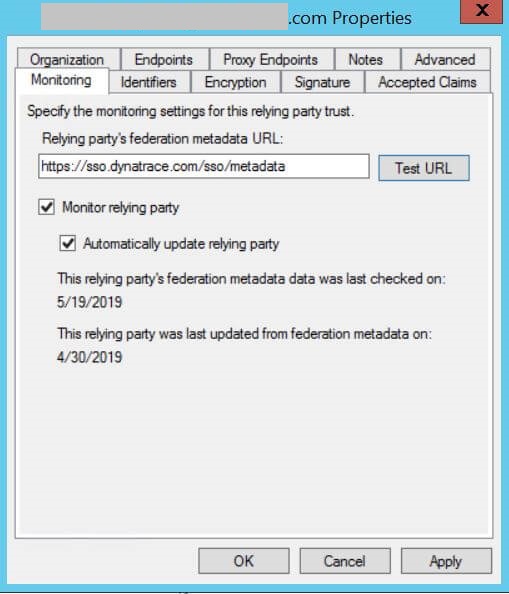
On the Monitoring tab, specify the monitoring settings for the relying party trust.
- Relying party's federation metadata URL - We recommend that you specify the SSO Dynatrace federation metadata URL:
https://sso.dynatrace.com/sso/metadata - Monitor relying party - Selected.
- Automatically update relying party - Selected.
Monitoring tab example
 Alternative
AlternativeIf you can't do the above (perhaps due to corporate policy), you need to download the metadata manually:
- Run the following command in PowerShell:
wget -Outfile dynatrace_sso_metadata.xml https://sso.dynatrace.com/sso/metadata - Update it for Dynatrace SSO RelyingPartyTrust:
Update-AdfsRelyingPartyTrust -TargetIdentifier "<DYNATRACE_SSO_IDENTIFIER>" -MetadataFile 'dynatrace_sso_metadata.xml'
- Relying party's federation metadata URL - We recommend that you specify the SSO Dynatrace federation metadata URL:
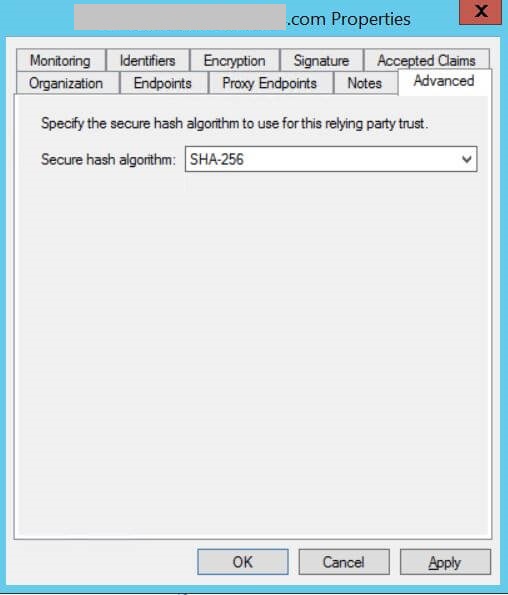
-
On the Advanced tab, make sure the Secure hash algorithm is
SHA-256.Advanced tab example
Configure claims mapping
To configure claims mapping
- Right-click
Sso Dynatrace Relying Party TrustunderTrust Relationship. - Select
Edit Claims Rules.
Create Active Directory transformations
To create Active Directory transformations
- Click
Add Rule.... - Select
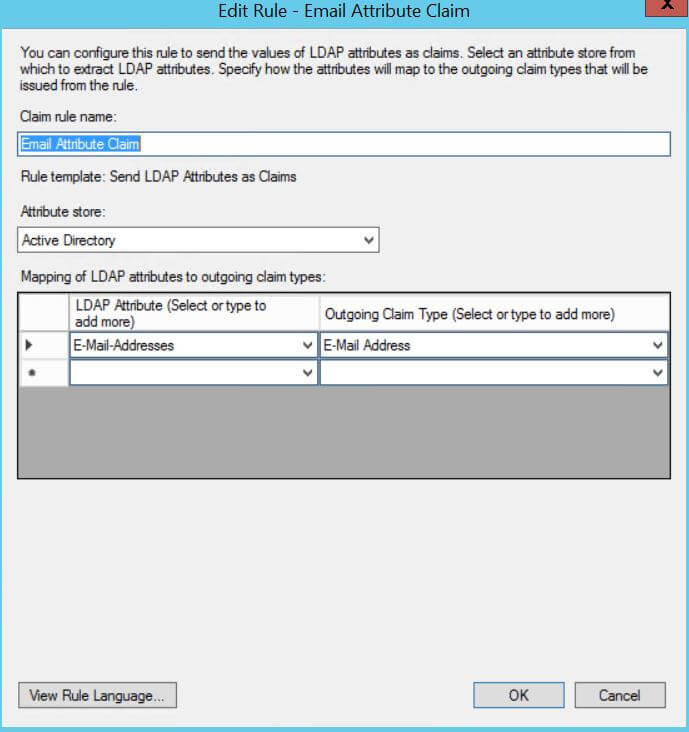
Send LDAP Attributes as Claims(the default option) and set values according to the following example values. - Edit Rule - Email Attribute Claim:
- Claim rule name:
Email Attribute Claim - Attribute store:
Active Directory - Mapping of LDAP attributes to outgoing claim types:
- LDAP Attribute =
E-Mail-Addresses, Outgoing Claim Type =E-Mail Address
- LDAP Attribute =
Email Attribute Claim example
- Claim rule name:
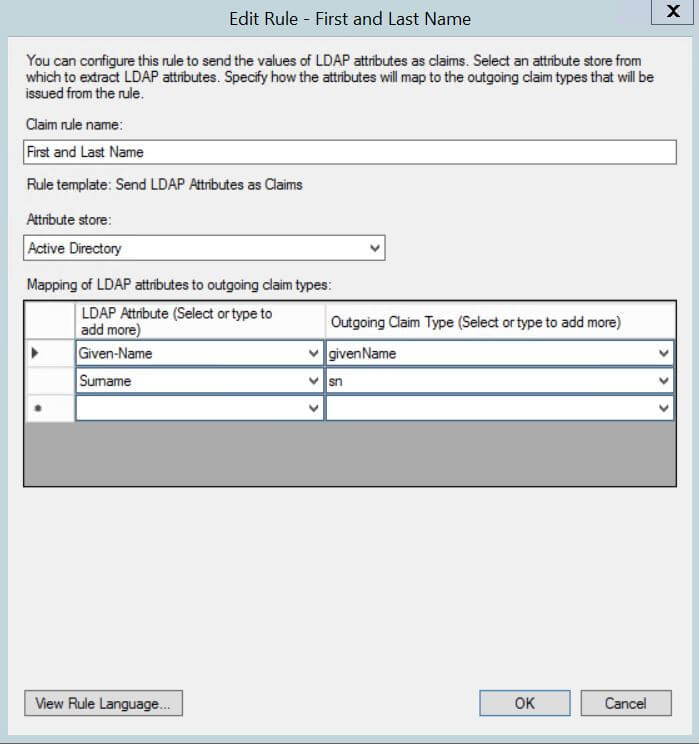
- Edit Rule - First and Last Name:
- Claim rule name:
First and Last Name - Attribute store:
Active Directory - Mapping of LDAP attributes to outgoing claim types:
- LDAP Attribute =
Given-Name, Outgoing Claim Type =givenName - LDAP Attribute =
Surname, Outgoing Claim Type =sn
- LDAP Attribute =
First and Last Name example
- Claim rule name:
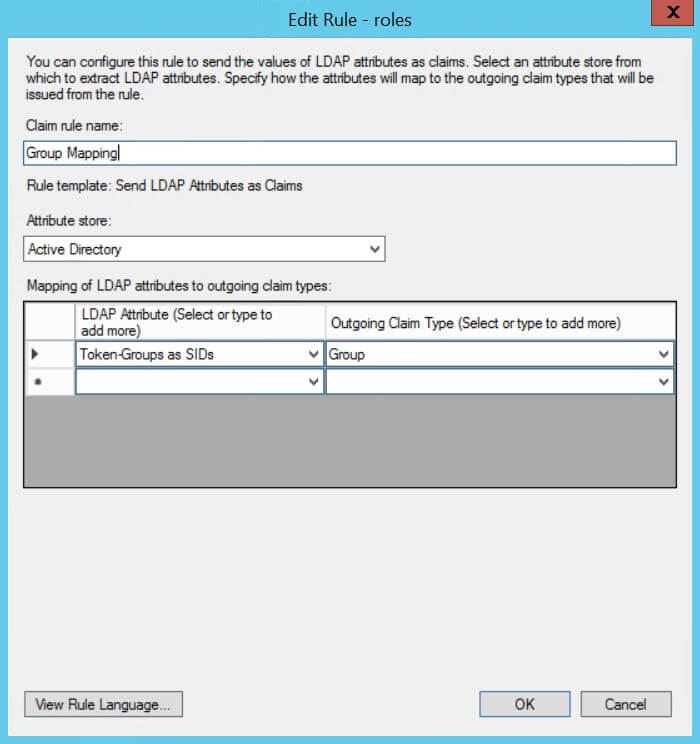
- Edit Rule - roles:
Token-Groups as SIDsis an example LDAP attribute that can be used for group mapping. Depending on your corporate LDAP, select the one that contains the LDAP user groups.- Claim rule name:
Group Mapping - Attribute store:
Active Directory - Mapping of LDAP attributes to outgoing claim types:
- LDAP Attribute =
Token-Groups as SIDs, Outgoing Claim Type =Group
- LDAP Attribute =
Roles example
- Claim rule name:
Create Email to NameID transformation
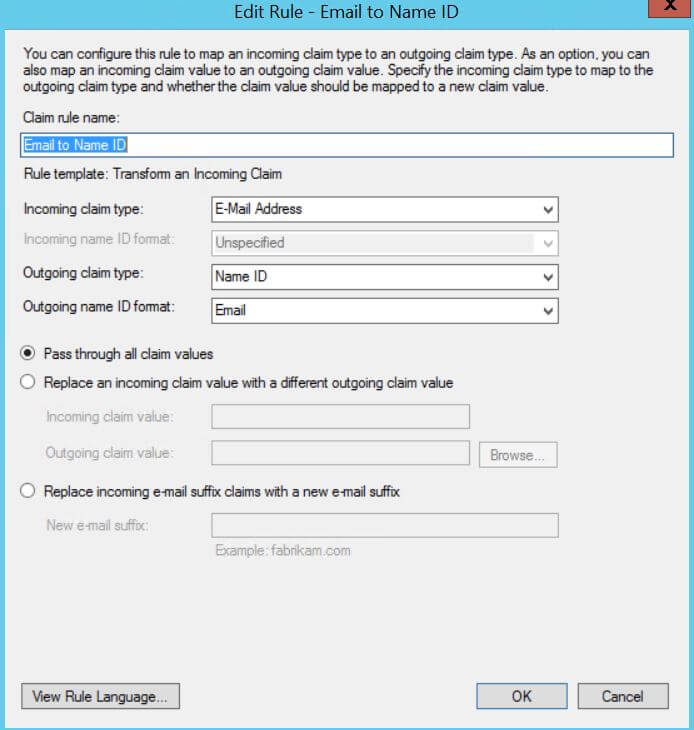
To create an Email Address to NameID transformation
- Click
Add Rule. - Select
Transform an Incoming Claim. - Set the values according to this example.
- Claim rule name:
Email to Name ID - Incoming claim type:
E-Mail Address - Outgoing claim type:
Name ID - Outgoing name ID format:
Email - Pass through all claim values:
selected
Email to Name ID example
- Claim rule name:
Final steps
-
Ensure that the SAML message will be signed:
Set-ADFSRelyingPartyTrust -TargetIdentifier "<DYNATRACE_SSO_IDENTIFIER>" -SamlResponseSignature "MessageAndAssertion" -
Ensure that the system clock's skew won't affect SAML request validation:
Set-ADFSRelyingPartyTrust -TargetIdentifier "<DYNATRACE_SSO_IDENTIFIER>" -NotBeforeSkew 2 -
Establish SAML authorization in Dynatrace SSO.
You need to specify
First name attribute,Last name attribute, and theGroup attribute.
Usually these attributes for AD FS will be as follows, but this may vary depending on the AD FS version and settings.First name attributehttp://schemas.xmlsoap.org/ws/2005/05/identity/claims/givennameLast name attributehttp://schemas.xmlsoap.org/ws/2005/05/identity/claims/surnameGroup attributehttp://schemas.xmlsoap.org/claims/Group