Google Workspaces SAML configuration for Dynatrace
- Latest Dynatrace
- How-to guide
- 5-min read
- Published Jul 22, 2019
Follow the examples below to configure Google Workspace as the SAML identity provider (IdP) for Dynatrace SSO.
This page describes the IdP (Google Workspaces) end of your SAML SSO configuration, not the Dynatrace end. Use it as part of the entire SAML configuration procedure for Dynatrace SaaS if you're using Google Workspace.
While we do our best to provide you with current information, Dynatrace has no control over changes that may be made by third-party providers. Always refer to official third-party documentation from your IdP as your primary source of information for third-party products.
Configuring Google Workspace SAML application
-
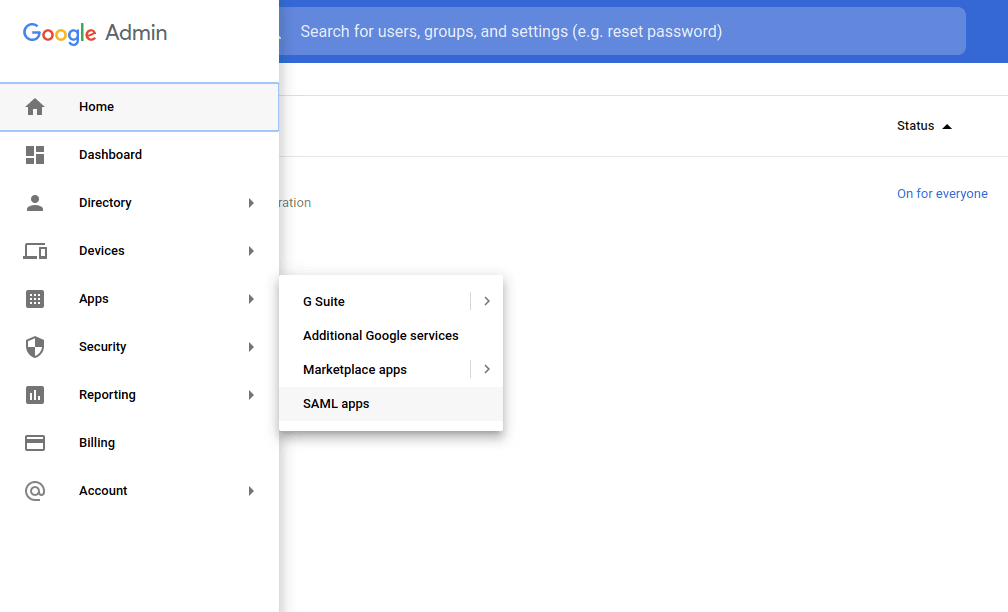
Navigate to the Google Workspace Admin panel and choose Apps > SAML apps from the menu.
Choose SAML Apps - example
-
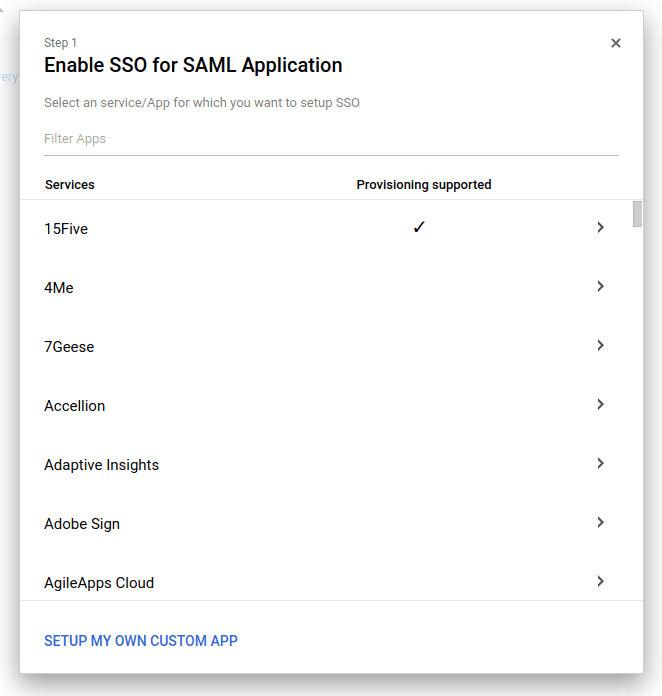
Choose to add a new SAML application to open a pop-up configuration wizard.
-
On the Enable SSO for SAML Application page, select Setup my own custom App.
Enable SSO for SAML Application - example
-
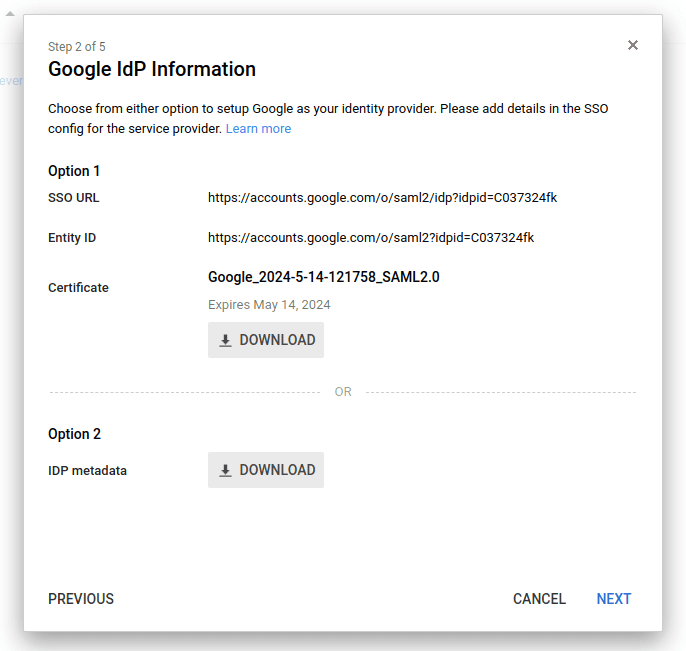
On the Google IdP Information page, in the IDP metadata section (Option 2), click Download to download the IdP metadata as an XML file. This will be needed when configuring single sign-on in Dynatrace.
Google IdP Information - example
-
On the Basic information for your Custom App page, provide an intuitive Application Name.
Basic information for your Custom App - example
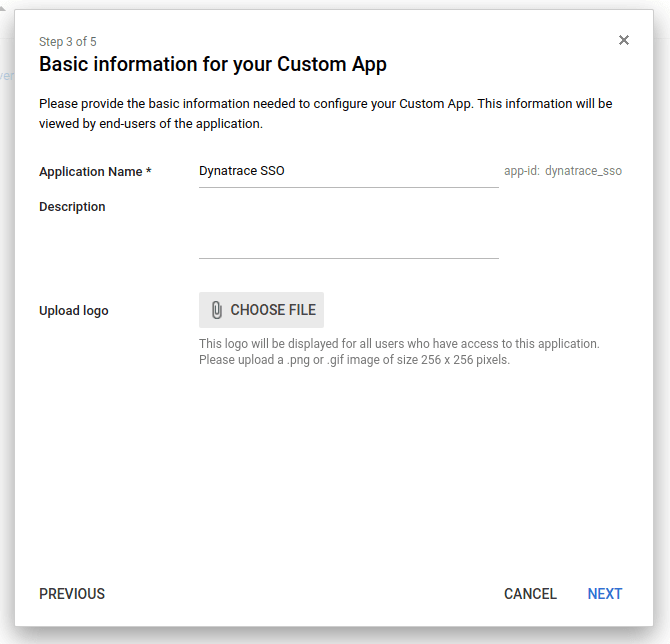
-
On the Service Provider Details page, enter Service Provider (SP) details as follows:
This information can also be found in Dynatrace SSO metadata at https://sso.dynatrace.com/sso/metadata.
Service Provider Details - example
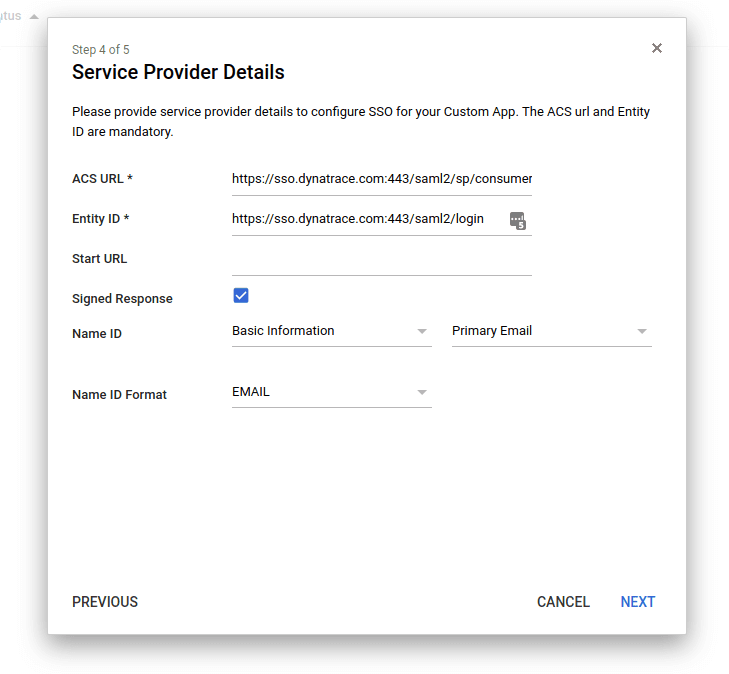
-
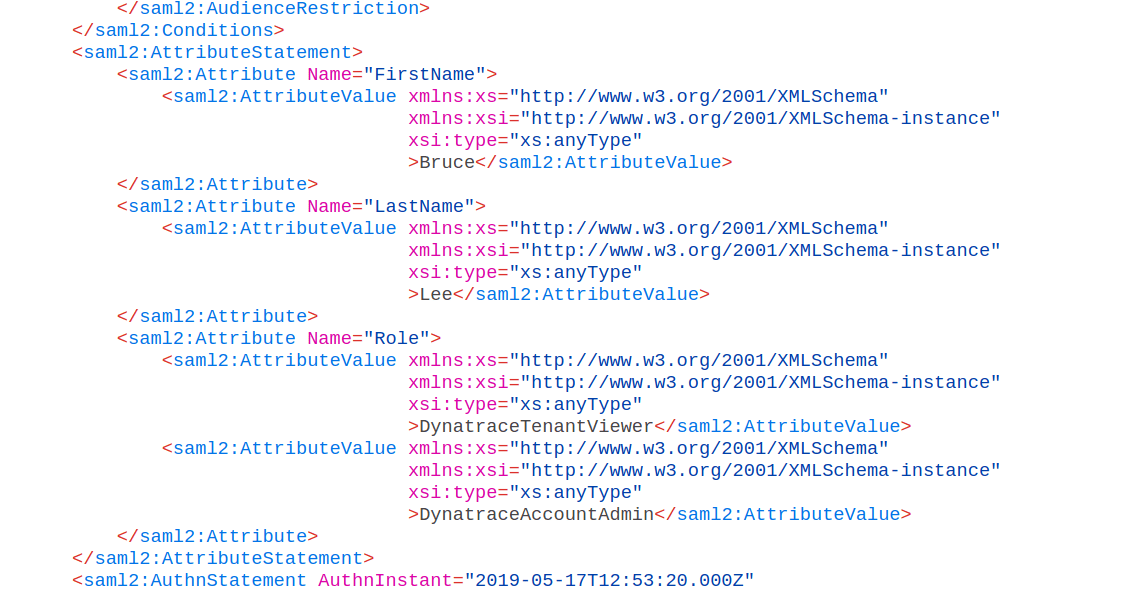
On the Attribute Mapping page, add mappings for
FirstNameandLastNameas shown in the example. (You'll need to add a third mapping later forGroups, which is described in the Preparing group mapping section that follows.)Attribute Mapping,
FirstNameandLastName- example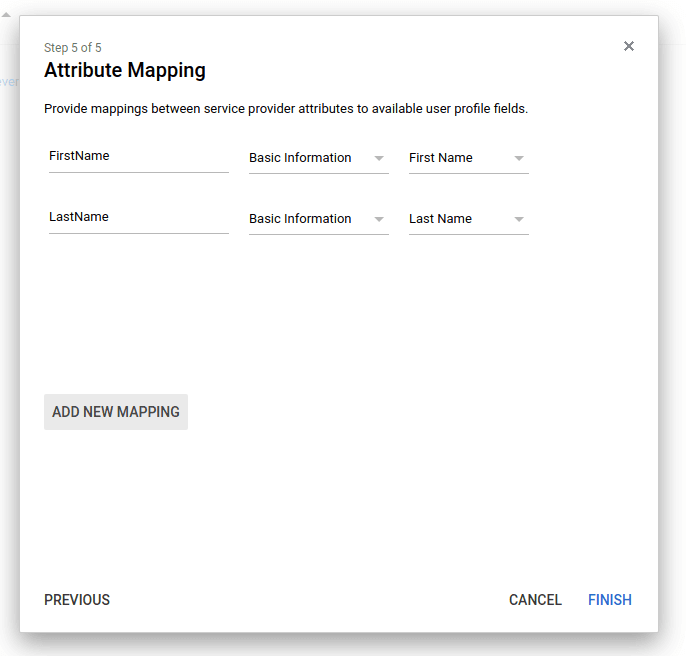
Preparing group mapping
By default, Google Workspace doesn't offer a way to send user groups through SAML. This is required for mapping to certain groups/permissions in Dynatrace. The only fields that can be delivered by SAML are as in this example:
Attribute Mapping - example
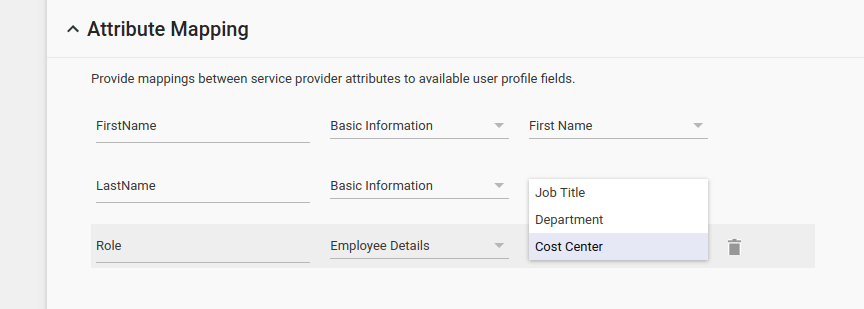
This doesn't allow the Google Workspace administrator to provide a list of groups or permissions that the user should have in Dynatrace.
Google suggests that you add a custom schema to user accounts. This enables you to add multiple group entries that, upon being sent via SAML, are mapped correctly to groups and permissions in Dynatrace.
- Navigate to the Google Directory API:
https://developers.google.com/admin-sdk/directory/v1/reference/schemas/insert?authuser=1Example
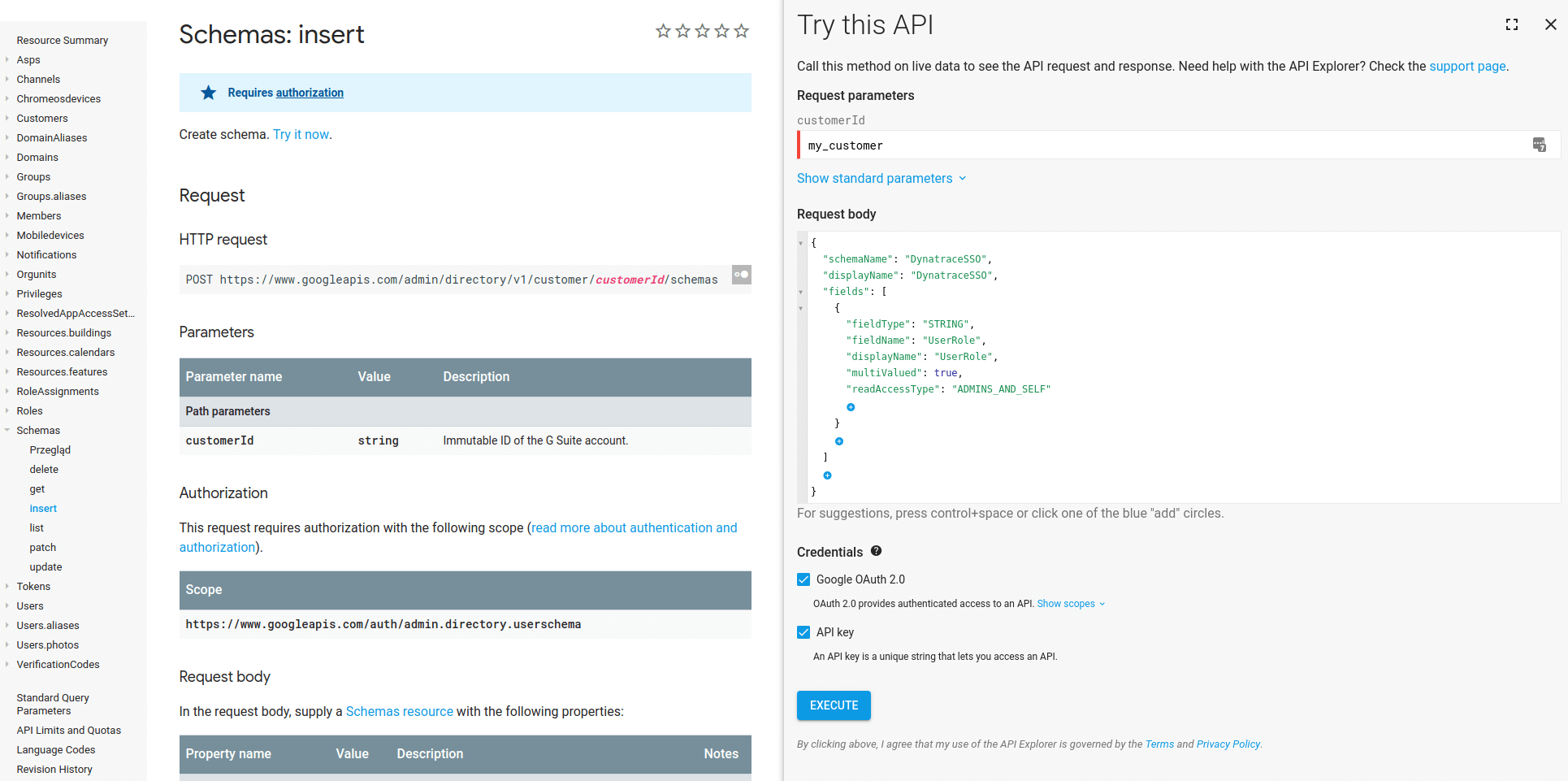
- Make the following schema edits.
- Set customerId to
my_customer, which automatically uses this Google account's ID. - We suggest the following schema (in JSON) for Dynatrace:
{"schemaName": "DynatraceSSO","displayName": "DynatraceSSO","fields": [{"fieldType": "STRING","fieldName": "UserRole","displayName": "UserRole","multiValued": true,"readAccessType": "ADMINS_AND_SELF"}]}
- Set customerId to
- Click Execute to add the new schema for all users.
The new configuration will now be selectable as a SAML attribute for users. - In the Google Workspace Admin panel, navigate back to Apps > SAML apps as before.
Choose SAML Apps - example

- Click through to Attribute Mapping, where the mappings for
FirstNameandLastNamewere added previously. - Set the
Roleattribute toDynatraceSSOandUserRole.Adding the Role attribute - example

This will make Google send all of the entries in DynatraceSSO/UserRole for a certain user as an attribute in SAML, which Dynatrace SSO will use to assign permissions upon a federated login. The user roles can be applied to each user separately using the user configuration screen in Google Workspace.
Assigning user roles
User roles can be applied to every user separately using the User information screen in Google Workspace.
Google Workspace User information screen
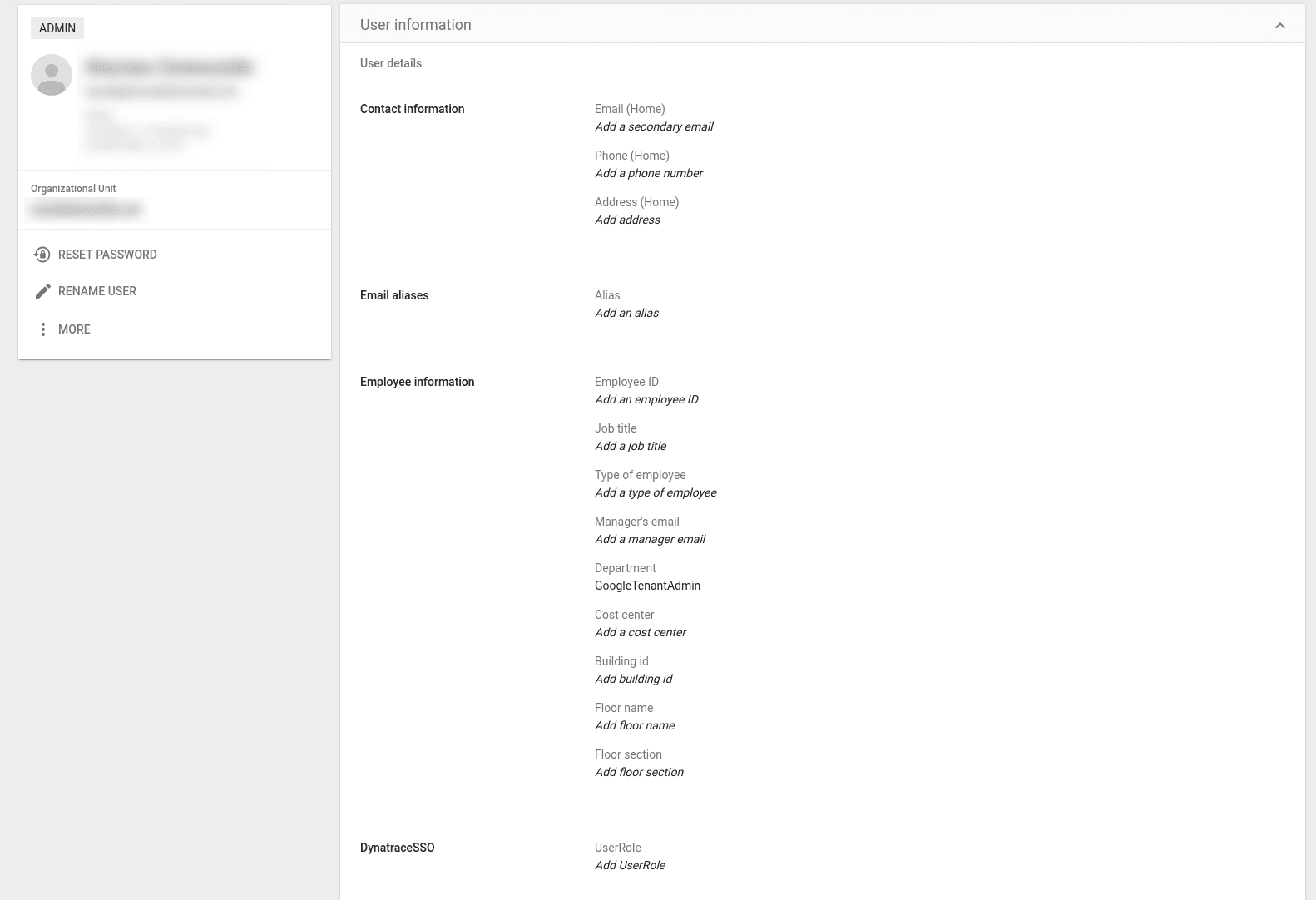
Google Workspace User information screen - multiple roles
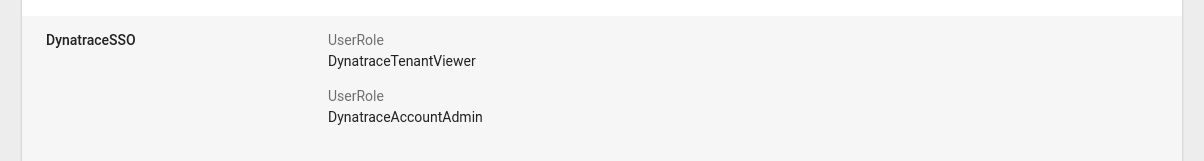
You can map these roles in Dynatrace Account Management to certain permissions as needed.
Note that in Google Workspace, UserRole has to have the same value as the SAML Group Attribute Value in Dynatrace Account Management (for example, DynatraceTenantViewer and DynatraceAccountAdmin).
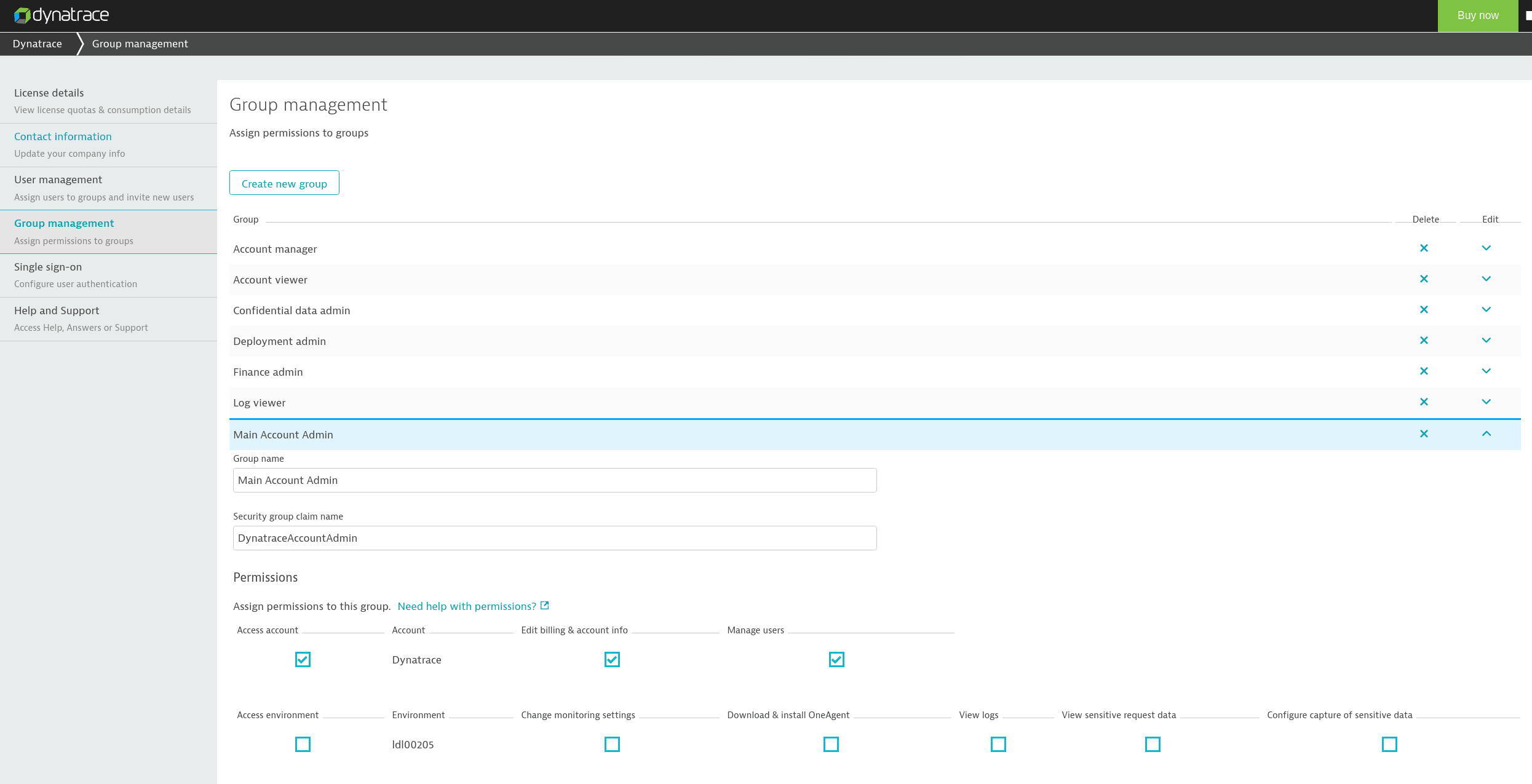
Example
Say you've set up two groups in Dynatrace Account Management and have a group called Main Account Admin, which is assigned a federated user by the SAML Group Attribute Value DynatraceAccountAdmin.
If you now attach the DynatraceAccountAdmin UserRole to any user in Google Workspace, that user will be assigned the permissions of the Main Account Admin group in Dynatrace Account Management.
Dynatrace Group management example
Upon setting up the SAML apps configuration in Google Workspace correctly, the SAML request sent from Google Workspace should contain the configured groups as SAML attributes.
SAML request example