Levels of data protection
- Latest Dynatrace
- 2-min read
Depending on your environment setup and settings, you might capture data for which you have legal obligations due to protection laws, standards, and regulations, such as GDPR, CCPA, HIPAA, LGPD, PCI-DSS and more. To address such cases, Dynatrace offers multiple layers of protection to help you fine-tune the data flows in Dynatrace.
Check a flowchart below to see on what levels and entities your end users' data is masked in Dynatrace.
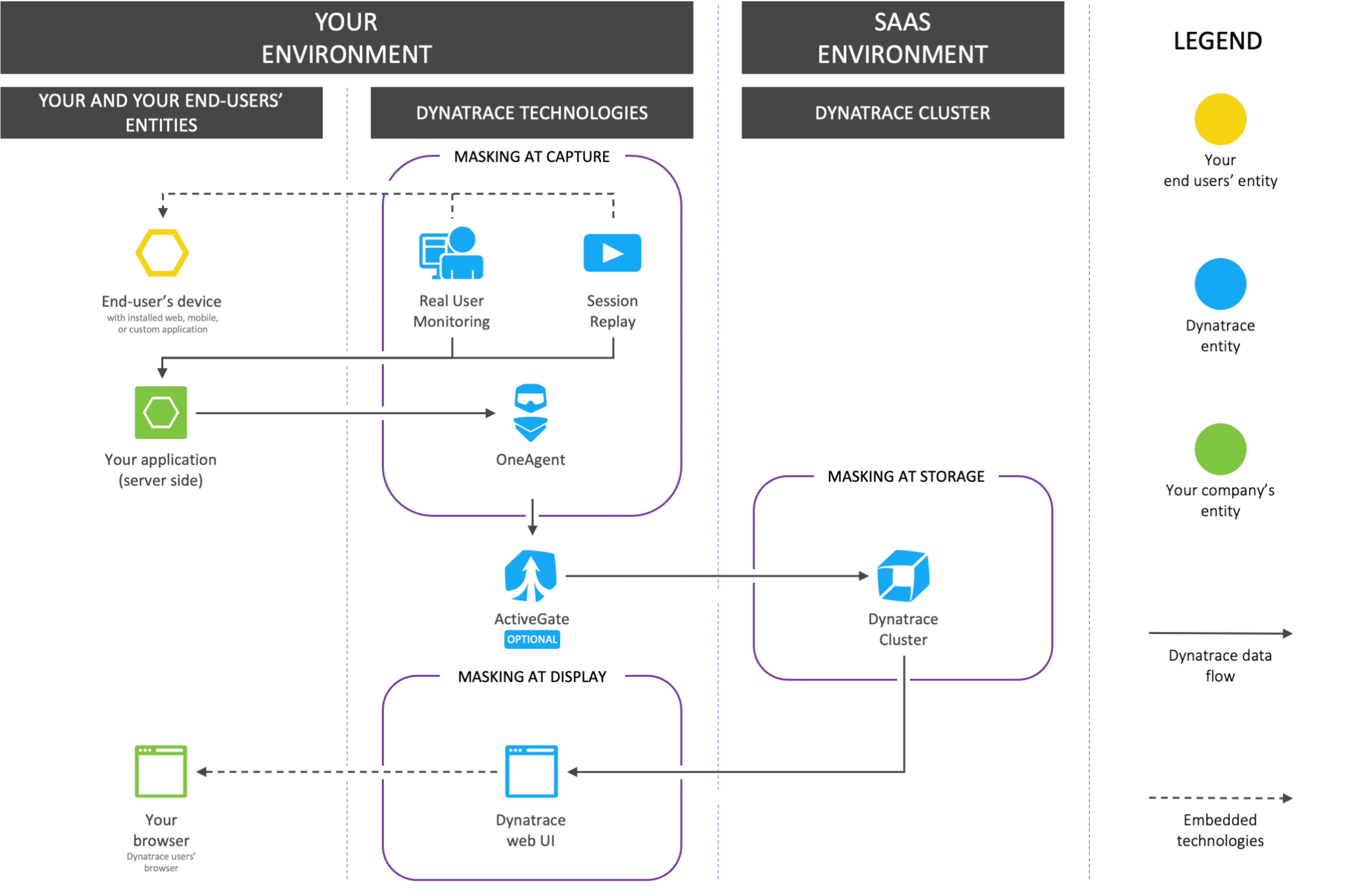
For masking at capture and masking at storage, any related masking capability in Dynatrace is applied only after you enable it; such masking is not applied retroactively.
Protect personal data by not capturing it (masking at capture)
With masking at capture, data is masked at first contact with Dynatrace. The original data does not leave the monitored environment.
Dynatrace can automatically mask sensitive data points at first contact with a Dynatrace technology. This happens within the application, monitored process, or browser so that the data points are replaced with a placeholder before sending them to the Dynatrace Cluster. Asterisks (*) are used for such placeholders. For example, the john.smith@domain.com email address is transformed into ********* and is never sent or stored in its original form.
Use the following settings to control masking at capture.
Protect personal data by not storing it (masking at storage)
When masking at storage is implemented, data is sent to the Dynatrace server for optimal analysis and is masked before it's stored.
Leverage the following settings to control masking at storage.
Protect personal data by not displaying it (masking at display)
When data is masked at display, it's stored in its original form but is accessible only to the users of your choice.
Check the following information to learn how to configure masking at display.