Automate and orchestrate security findings
- Latest Dynatrace
- Tutorial
- Published Aug 30, 2024
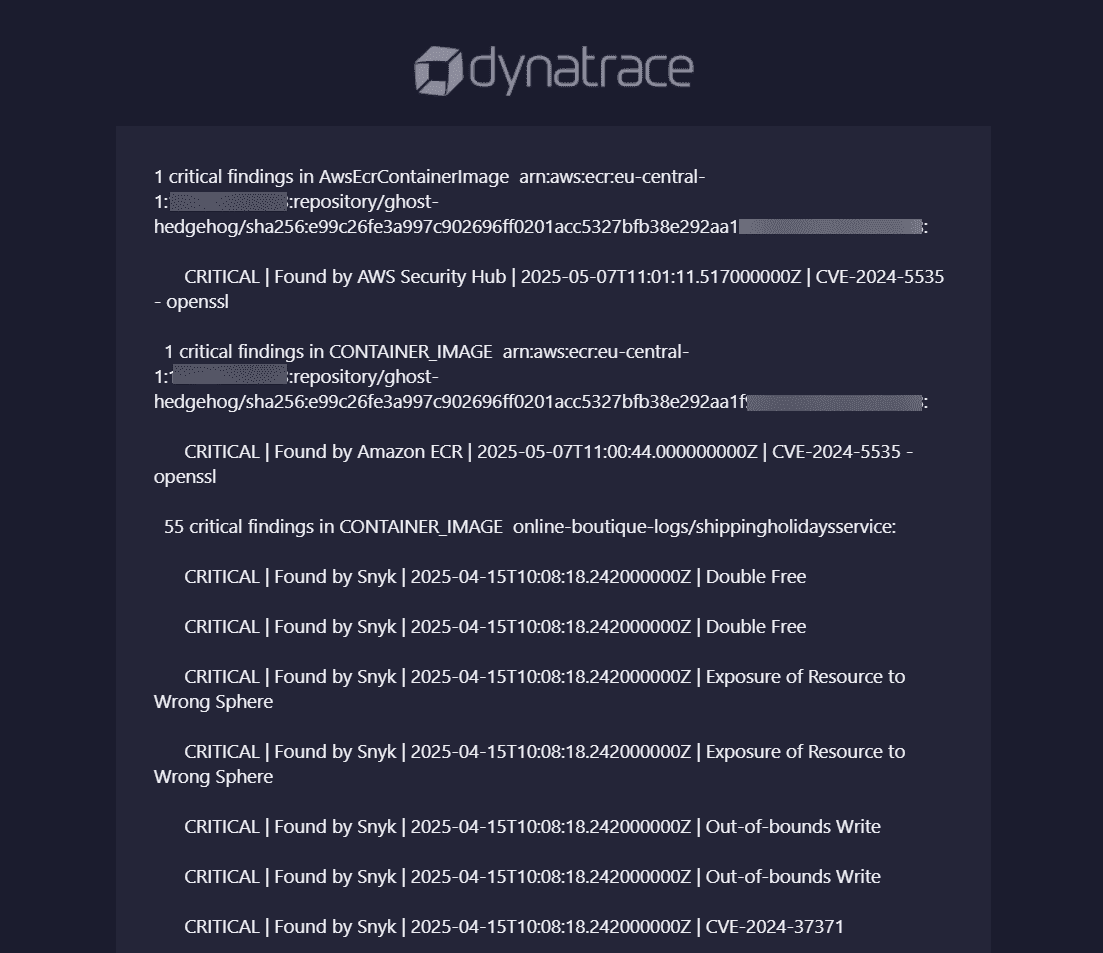
Prioritization and remediation of security findings require a lot of manual effort. With so many different security tools, efficiently orchestrating the findings and focusing on the critical ones becomes impossible.
While siloed products can provide localized automation, they often generate excessive noise. This means dev teams ultimately ignore alerts and tickets, and the security posture degrades.
In this context, you can
-
Ingest security findings from various tools and map them to the Dynatrace Semantic Dictionary.
-
Automate and orchestrate security findings across products and tools with our workflow automation samples, which you can further customize with the robust Workflows capabilities for your organization's orchestration processes.
Target audience
Security architects and managers who aim to streamline remediation processes and direct the development teams’ efforts towards effective remediation.
Key use cases include:
- Ticket creation for remediation of the discovered critical issues
- Notification of the relevant stakeholders on the critical findings
- Email reporting on the top findings
Prerequisites
Ingest security findings from your third-party product.
Get started
-
Download our sample workflow from GitHub.
- For vulnerability findings, download these sample workflows instead:
- For container vulnerability findings, download these sample workflows instead:
For some integrations, such as Amazon ECR or AWS Security Hub, workflow samples are available in the app in the Try our templates section (in Settings, search for and select the app).
-
Open
 Workflows, select
Workflows, select Upload, then select the downloaded file.
Example result: