Discover coverage gaps in security findings
- Latest Dynatrace
- Tutorial
During the Software Development Lifecycle (SDLC), multiple tools scan various artifacts as they progress through the development stages. An artifact like a container image reaches the deployment stage and eventually represents your running applications. At this point, you want to be sure the artifacts went through the proper security scanning procedures and didn't skip any essential validation.
Gaining complete visibility of the validation cycle isn't easy, as the scanning products used by different teams silo.
In this context, you can
-
Aggregate the security scans for the deployed and running artifacts.
-
Gain complete visibility into the security validations those artifacts went through before reaching your production environment.
-
Discover gaps in your security procedures and remediate them before they become a real risk.
-
Visualize security findings across the products and tools with our dashboard samples, which can also be a good foundation for tailoring further visual customization to meet your organization's posture analysis and reporting requirements.
Target audience
Security architects and managers responsible for keeping the security scan procedures aligned with the security standards.
Key use cases include:
- Gaining an overview of the performed security assessments
- Identifying coverage gaps
- Identifying top contributing products and their ROI
Prerequisites
Ingest security findings from your third-party product.
Get started
1. Visualize
- Open
 Dashboards and go to Ready-made.
Dashboards and go to Ready-made. - Search for and select Security product coverage for the desired integration.
Example result:
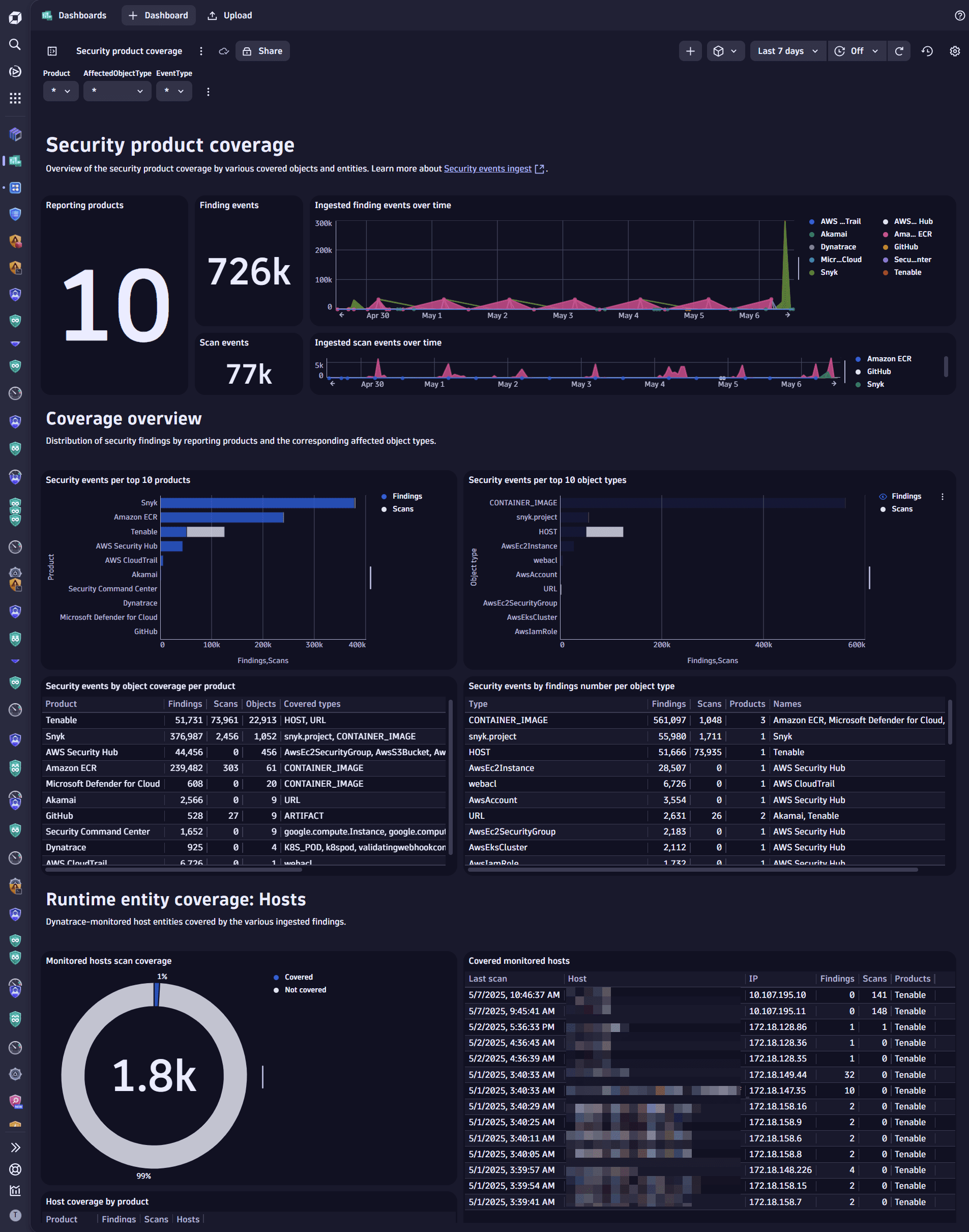
2. Analyze
Open  Notebooks to query security findings, using the data format in Semantic Dictionary.
Notebooks to query security findings, using the data format in Semantic Dictionary.
For a better understanding of how to build your queries, see DQL query examples for ingested events.