Deploy Dynatrace OTel Collector
- Latest Dynatrace
- How-to guide
- 9-min read
Deployment modes
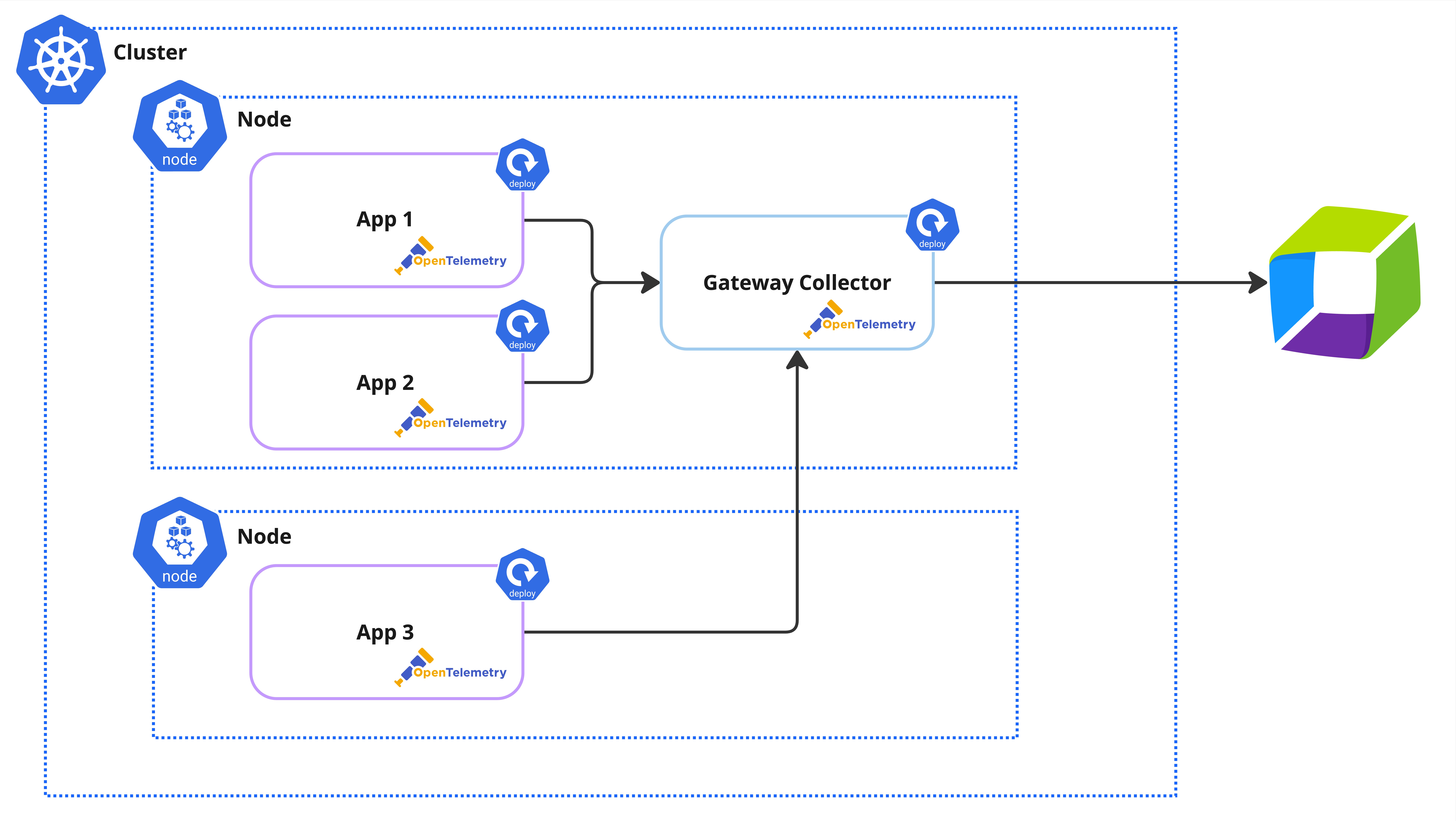
The Collector can be deployed as a standalone agent or gateway.
For illustrative purposes, the graphics below show the modes in a Kubernetes setup, but the same modes can also be used outside of Kubernetes.
As an agent, the Collector is deployed either with the application or on the same host as the application. This Collector can receive telemetry data and enhance it with, for example, tags or infrastructure information.
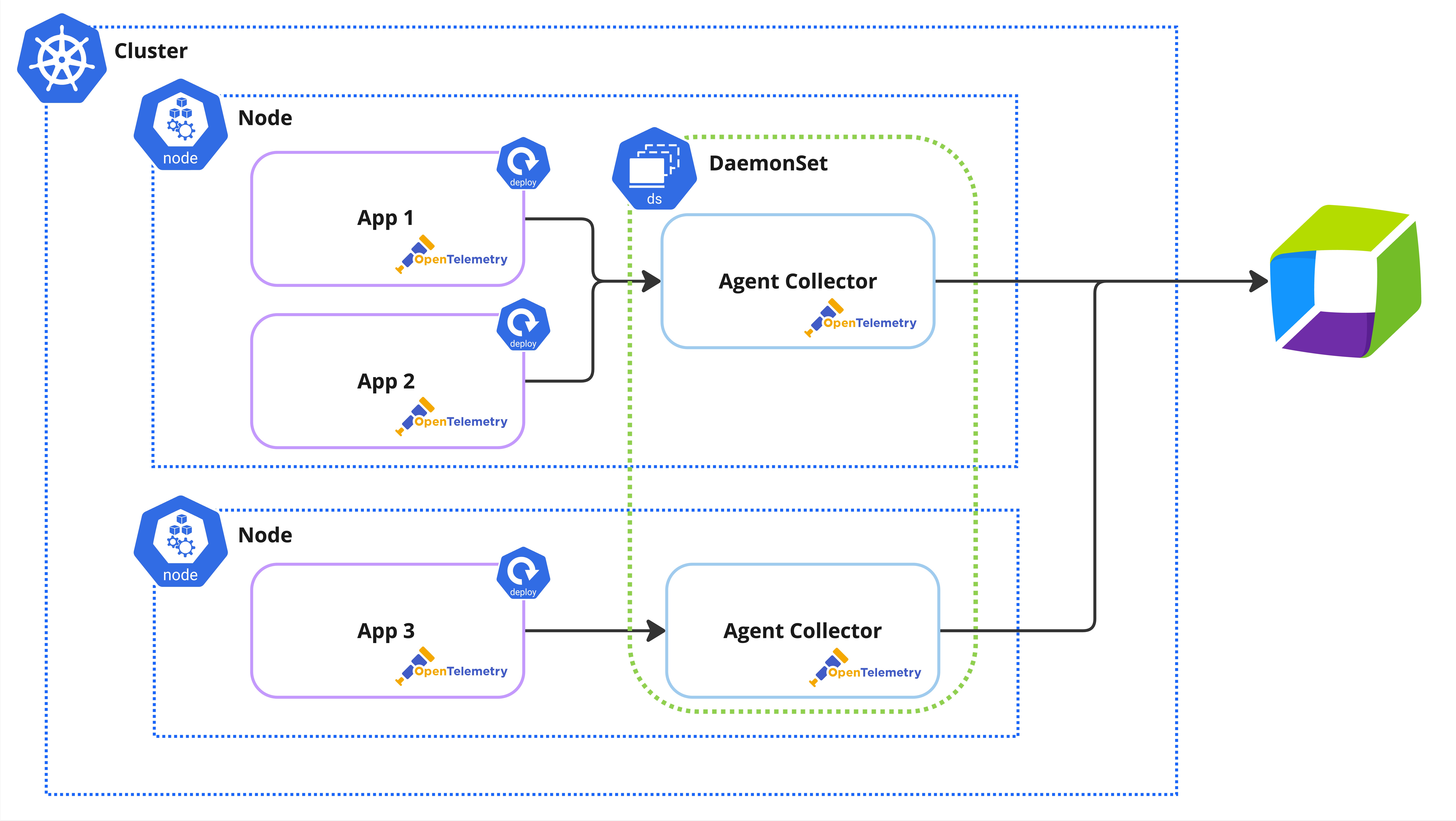
It's also possible to combine these deployment modes and chain Collector instances. Consider this if you're deploying the Collector in large environments.
Deployment Options
The Dynatrace Collector can be deployed for the following platforms:
Kubernetes
For Kubernetes, the Dynatrace Collector can be deployed in the following ways:
- OpenTelemetry Kubernetes Operator
- Helm
- Raw manifest
Dynatrace access details
Before you deploy the Collector, you need to set up the necessary Kubernetes secrets for the Dynatrace access details.
Use kubectl to create Kuberenetes secrets for the Dynatrace export details. Replace the placeholders (indicated by curly brackets) with the actual values for the export URL and the API token.
kubectl create secret generic dynatrace-otelcol-dt-api-credentials --from-literal=DT_ENDPOINT={ENDPOINT_URL_HERE} --from-literal=DT_API_TOKEN={API_TOKEN_HERE}
Kubernetes deployment variants
The following sample configurations apply a resource limit of 512 megabytes. You may need to adjust this under resources.limits.memory for your particular use case.
Prerequisites
If you haven't installed OpenTelemetry Operator yet, first make sure cert-manager is installed. Afterwards, you can deploy Operator with the following kubectl command:
kubectl apply -f https://github.com/open-telemetry/opentelemetry-operator/releases/download/v0.144.0/opentelemetry-operator.yaml
After the installation, deploy the Dynatrace Collector either in gateway or agent deployment mode, with one of the following configuration samples. Save it as crd-dynatrace-collector.yaml and deploy it with kubectl apply.
The Kubernetes CRD of the Operator can be found on GitHub.
Deploy as a gateway (Deployment)
apiVersion: opentelemetry.io/v1beta1kind: OpenTelemetryCollectormetadata:name: dynatrace-otelspec:envFrom:- secretRef:name: dynatrace-otelcol-dt-api-credentialsenv:- name: MY_POD_IPvalueFrom:fieldRef:fieldPath: status.podIPmode: "deployment"image: "ghcr.io/dynatrace/dynatrace-otel-collector/dynatrace-otel-collector:0.44.0"resources:limits:memory: 512Miconfig:receivers:otlp:protocols:grpc:endpoint: ${env:MY_POD_IP}:4317http:endpoint: ${env:MY_POD_IP}:4318exporters:otlp_http:endpoint: "${env:DT_ENDPOINT}"headers:Authorization: "Api-Token ${env:DT_API_TOKEN}"service:pipelines:traces:receivers: [otlp]processors: []exporters: [otlp_http]metrics:receivers: [otlp]processors: []exporters: [otlp_http]logs:receivers: [otlp]processors: []exporters: [otlp_http]
Deploy as an agent (DaemonSet)
apiVersion: opentelemetry.io/v1beta1kind: OpenTelemetryCollectormetadata:name: dynatrace-otelspec:envFrom:- secretRef:name: dynatrace-otelcol-dt-api-credentialsenv:- name: MY_POD_IPvalueFrom:fieldRef:fieldPath: status.podIPmode: "daemonset"image: "ghcr.io/dynatrace/dynatrace-otel-collector/dynatrace-otel-collector:0.44.0"resources:limits:memory: 512Miconfig:receivers:otlp:protocols:grpc:endpoint: ${env:MY_POD_IP}:4317http:endpoint: ${env:MY_POD_IP}:4318exporters:otlp_http:endpoint: "${env:DT_ENDPOINT}"headers:Authorization: "Api-Token ${env:DT_API_TOKEN}"service:pipelines:traces:receivers: [otlp]processors: []exporters: [otlp_http]metrics:receivers: [otlp]processors: []exporters: [otlp_http]logs:receivers: [otlp]processors: []exporters: [otlp_http]
In Kubernetes, it is common to enrich OpenTelemetry signals using the Kubernetes Attributes processor. This requires a Kubernetes service account, which is automatically configured when using Operator or Helm.
For raw manifests, this needs to be configured manually by adding a spec.serviceAccountName: collector entry to the deployment manifest.
Docker
Run the following command to download the image of the Dynatrace Collector:
docker pull ghcr.io/dynatrace/dynatrace-otel-collector/dynatrace-otel-collector:0.44.0
Next, ensure that the Collector configuration file exists in the current working directory and run the Collector image with the following command:
docker run -v $(pwd)/otel-collector-config.yaml:/etc/otelcol/otel-collector-config.yaml ghcr.io/dynatrace/dynatrace-otel-collector/dynatrace-otel-collector:0.44.0 --config=/etc/otelcol/otel-collector-config.yaml
The -v parameter maps the local configuration file to the given container path, which is subsequently passed to the --config parameter.
Make sure to map all required network ports with the -p parameter. For example, if you accept OTLP gRPC requests on the default port, you need to specify port 4317. For OTLP over HTTP specify port 4318.
Docker Compose
Use the following configuration in your Compose file to deploy and run the Collector image:
version: "3"services:collector:image: ghcr.io/dynatrace/dynatrace-otel-collector/dynatrace-otel-collector:0.44.0command: ["--config=/etc/otelcol/otel-collector-config.yaml"]volumes:- ./otel-collector-config.yaml:/etc/otelcol/otel-collector-config.yamlports:- "4317:4317" # OTLP gRPC- "4318:4318" # OTLP HTTP
In the example above, ports is configured for gRPC and HTTP. Adjust the list of ports according to your specific use case.
Windows, macOS, and Linux
To install the Collector binary manually
-
Download the dynatrace-otel-collector for your operating system from GitHub.
-
Decompress the archive file.
-
Set up the desired configuration and save it to
otel-collector-config.yaml. -
Run the
dynatrace-otel-collectorbinary and pass the path to the configuration file using the--configparameter../dynatrace-otel-collector --config=$(pwd)/otel-collector-config.yaml
Linux installer packages
Dynatrace also provides DEB and RPM installer packages for Linux systems on x86-64 and ARM64 architectures.
The installer packages require Systemd to be the active init system.
To deploy the Collector using an installer package, download the dynatrace-otel-collector for your operating system from GitHub, and install it using root privileges and the following commands.
Replace the following two placeholders in the commands with their actual content:
<VERSION>with the version tag of the download<ARCH>with the system architecture tag (that is,x86_64orarm64) of the download
apt-get updatedpkg -i dynatrace-otel-collector_<VERSION>_Linux_<ARCH>.deb
Service configuration
When first starting the service, it may fail to start if there is no configuration file in place yet. By default, the Collector attempts to find the file at /etc/dynatrace-otel-collector/config.yaml.
If you wish to use a different path, you can override the default path with the --config parameter as part of the OTELCOL_OPTIONS variable in the Systemd environment file at /etc/dynatrace-otel-collector/dynatrace-otel-collector.conf:
OTELCOL_OPTIONS="--config=<HERE-PATH-TO-CONFIG-FILE>"
Subsequent package updates will replace this file, so be sure to back up and restore its content during an update of the Collector package. Alternatively, you can override the configuration with the systemctl edit command.
To see all available configuration options, run the Collector binary with the --help parameter.
After changing the configuration, make sure to restart the service using the following command and root privileges:
systemctl restart dynatrace-otel-collector
Service status
To view the current status of the Collector service, run the following command with root privileges:
systemctl status dynatrace-otel-collector
To check the output of the Collector service, run the following command with root privileges:
journalctl -u dynatrace-otel-collector
Container image registries
Container images for the Dynatrace distribution of the OpenTelemetry Collector are available in
-
GitHub Container Registry (GHCR)
ghcr.io/dynatrace/dynatrace-otel-collector/dynatrace-otel-collector:0.44.0
-
Amazon Elastic Container Registry (Amazon ECR)
public.ecr.aws/dynatrace/dynatrace-otel-collector:0.44.0
-
Docker Hub Container Registry
dynatrace/dynatrace-otel-collector:0.44.0