Ingest Sonatype Lifecycle security events and audit logs
- Latest Dynatrace
- Extension
This page has been updated to align with the new Grail security events table. For the complete list of updates and actions needed to accomplish the migration, follow the steps in the Grail security table migration guide.
Ingest Sonatype Lifecycle security events and audit logs into Dynatrace as security events.
Get started
Overview
Dynatrace integration with Sonatype Lifecycle allows users to unify and contextualize vulnerability findings across DevSecOps tools and products, enabling central prioritization, visualization, and automation of security findings.
Sonatype offers a range of products to help developers improve their productivity. The Sonatype Lifecycle product identifies vulnerabilities in development artifacts, such as code and containers. The Dynatrace platform observes the corresponding runtime entities associated with those artifacts. Ingesting and enriching vulnerability findings helps users to better focus on the top risks that affect their production applications.
Use cases
With the ingested data, you can accomplish various use cases, such as
Requirements
See below for the Sonatype Lifecycle and Dynatrace requirements.
Sonatype Lifecycle requirements
To enable the extension to collect security data from Sonatype Lifecycle, authentication credentials with appropriate permissions are required. There are two options to provide credentials:
-
Option 1: User token Recommended
-
Recommended for service users.
-
Consists of a user code and a passcode.
-
These are disposable credentials that can be revoked at any time without impacting the associated user account.
-
-
Option 2: Username and password
- Uses your account’s standard login credentials.
Required permissions:
To ensure successful data collection, the authenticated user must have the following permissions in Sonatype Lifecycle:
-
View IQ Elements -
Access Audit Log(required only if audit log ingestion is configured)
Dynatrace requirements
-
ActiveGate version 1.313+ that needs to be able to
- Run Extensions 2.0 framework
- Reach the Sonatype API endpoints
-
Permissions: For a list of permissions required, go to Hub, select
 Extensions, and display Technical information.
Extensions, and display Technical information. -
Generate an access token with the
openpipeline.events_securityscope and save it for later. For details, see Dynatrace API - Tokens and authentication.
Activation and setup
-
In Dynatrace, search for Sonatype Lifecycle and select Install.
-
Follow the on-screen instructions to configure the extension.
-
Verify configuration by running the following queries in
 Notebooks:
Notebooks:-
For audit logs:
fetch logs| filter log.source=="Sonatype Lifecycle" -
For finding events:
fetch security.events| filter dt.system.bucket == "default_securityevents"| filter event.provider=="Sonatype Lifecycle"AND event.type=="VULNERABILITY_FINDING" -
For scan events:
fetch security.events| filter dt.system.bucket == "default_securityevents"| filter event.provider=="Sonatype Lifecycle"AND event.type=="VULNERABILITY_SCAN"
-
-
Once the extension is installed and working, you can access and manage it in Dynatrace via
 Extensions. For details, see About Extensions.
Extensions. For details, see About Extensions.
Details
How it works
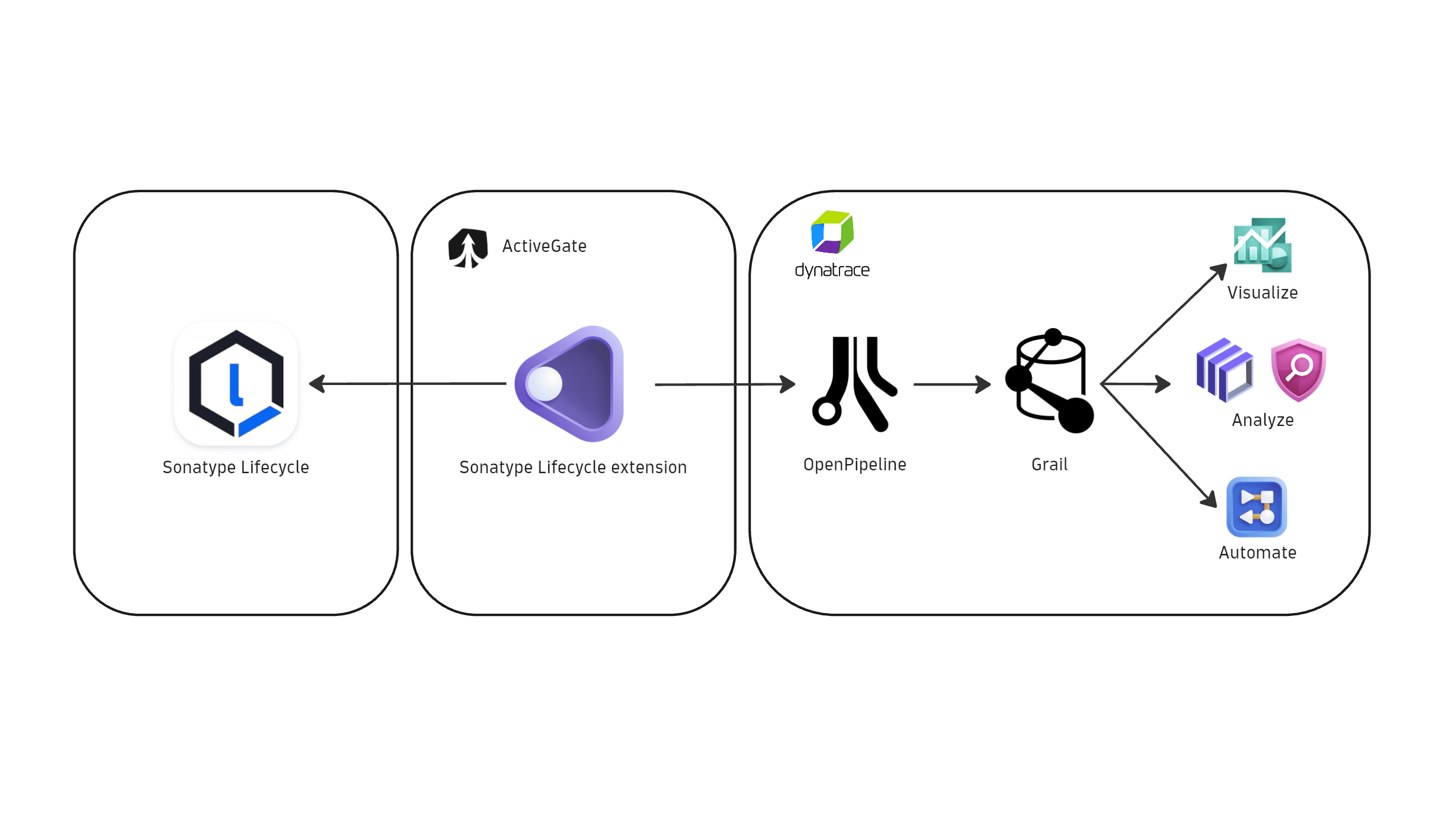
Dynatrace integration with Sonatype Lifecycle is an extension running on Dynatrace ActiveGate. Once you enable and configure the Dynatrace Sonatype Lifecycle extension
-
It periodically collects security findings and audit logs using Sonatype REST API.
-
The fetched data is ingested into Dynatrace and mapped to the Dynatrace Semantic Dictionary.
-
Data is stored in a bucket called
default_securityevents(for details, see Built-in Grail buckets).
Licensing and cost
For billing information, see Events powered by Grail.
FAQ
Which data model is used for the security logs and events coming from Sonatype Lifecycle?
-
Vulnerability finding events store the individual vulnerability findings reported by Sonatype Lifecycle per affected artifacts and component.
-
Vulnerability scan events indicate coverage of scans for individual artifacts.
-
Audit logs represent user activity logs in Sonatype Lifecycle.
Which Sonatype Lifecycle security findings are imported into Dynatrace?
-
On the first ingest, we consider findings updated in the last
mhours, wheremis the first ingest interval configured in the monitoring configuration. -
If the extension is configured to ingest data at an interval of
nhours, then whenever the extension runs all vulnerability findings updated in the lastnhours will be ingested. -
If no new or updated findings were detected, no findings will be ingested.
Which extension fields are added to the core fields of the events ingested from Sonatype Lifecycle?
The sonatype namespace is added for extracting several Sonatype-specific attributes for user convenience on top of the original issue JSON, which is stored in the event.original_content field.
Examples:
-
sonatype.application_public_idrepresents the friendly name of the assessed application. -
sonatype.application_internal_idrepresents the ID of the assessed application. -
sonatype.commit_hashrepresents the hash of a code commit that the assessment belongs to. -
sonatype.stagerepresents the application stage at which the assessment was performed.
What Sonatype Lifecycle asset types are supported by Dynatrace for runtime contextualization?
CODE_ARTIFACT: All the findings from Sonatype Lifecycle coming from the assessment of code artifacts are mapped set with CODE_ARTIFACT value in the object.type field, and the software_component namespace is added with the corresponding fields:
-
software_component.purlrepresents the package URL of the vulnerable software component. -
software_component.ecosystemrepresents the ecosystem of the component, such as maven, npm, and others. -
software_component.typerepresents the type of the vulnerable software component. -
software_component.namerepresents the name of the vulnerable library within a code artifact. -
software_component.versionrepresents the version of the vulnerable component.
How is the risk score for Sonatype Lifecycle findings normalized?
Dynatrace normalizes severity and risk scores for all findings ingested through the current integration. This helps you to prioritize findings consistently, regardless of their source.
For details on how normalization works, see Severity and score normalization.
The Dynatrace risk levels and scores are mapped from the original Sonatype Lifecycle scores.
-
dt.security.risk.score- is mapped from the Sonatype Lifecycle provided severity score to static scores. -
dt.security.risk.level- is mapped from the Sonatype Lifecycle severity score and mapped from the original values infinding.score.
dt.security.risk.score (mapped from finding.score) | dt.security.risk.level (mapped from dt.security.risk.score) |
|---|---|
| 9.0-10.0 | CRITICAL |
| 7.0-8.9 | HIGH |
| 4.0-6.9 | MEDIUM |
| 0.1-3.9 | LOW |
