Install your own SSL certificate for a cluster node
- How-to guide
- 3-min read
The Dynatrace UI is only accessible over encrypted HTTPS connections. To ensure secure access and avoid browser warnings, you must configure a valid SSL certificate. Dynatrace can manage this for you automatically—each cluster gets a dedicated web domain (subdomain of dynatrace-managed.com) and a trusted SSL certificate. You can use this domain to access the Dynatrace UI without receiving browser warnings.
If you don't want Dynatrace to create the domain and SSL certificate for you, go to Settings > Preferences in the Cluster Management Console and disable the Manage domain name and SSL certificates option. Dynatrace will then use a self-signed SSL certificate. Self-signed certificates aren't trusted by default—the first time you attempt to connect to Dynatrace Managed, you'll receive a security warning. Confirm this exception within your browser security settings.
To use your own trusted SSL certificate, disable automatic management and then follow the instructions below.
As of April 17, 2025, Chinese regulations require an ICP (Internet Content Provider) certification for all publicly accessible services using the dynatrace-managed.com domain. Since Dynatrace does not hold an ICP certificate due to the lack of a legal entity in China, our domains have been blocked by the local network providers.
To maintain monitoring capabilities, we recommend the following:
- Use internal DNS or IP addresses for Cluster ActiveGate endpoints.
- Avoid exposing the Dynatrace UI or endpoints to public Chinese networks.
Before you begin
You need your SSL certificate and the key files you received from Certificate Authority (CA):
-
Server certificate (
.ceror.cert) -
Root and Intermediate certificates (
.ceror.cert) -
Private key for certificates (
.pem)Encrypted private keysWe don't support encrypted private keys. To decrypt an SSL private key, run the following command:
openssl rsa -in encrypted.ssl.key -out decrypted.ssl.keywhere
encrypted.ssl.keyis the filename of your encrypted SSL private key.decrypted.ssl.keyis the output file for your decrypted SSL private key.
The command will prompt you for the password and save the decrypted key in the
decrypted.ssl.keyfile.
Install your trusted certificate on a Dynatrace Cluster node
If you want to use your own certificate or a CA-issued certificate, upload or paste the certificate to the Dynatrace Cluster node. You can also set the host name associated with the certificate to be part of the Dynatrace Cluster node configuration.
-
Sign in to Dynatrace Managed as an administrator.
-
On the Dynatrace Managed deployment status page, select the cluster node that needs the new certificate.
-
On the Node Details page, select Edit SSL certificate.
Sample SSL certificates edit page
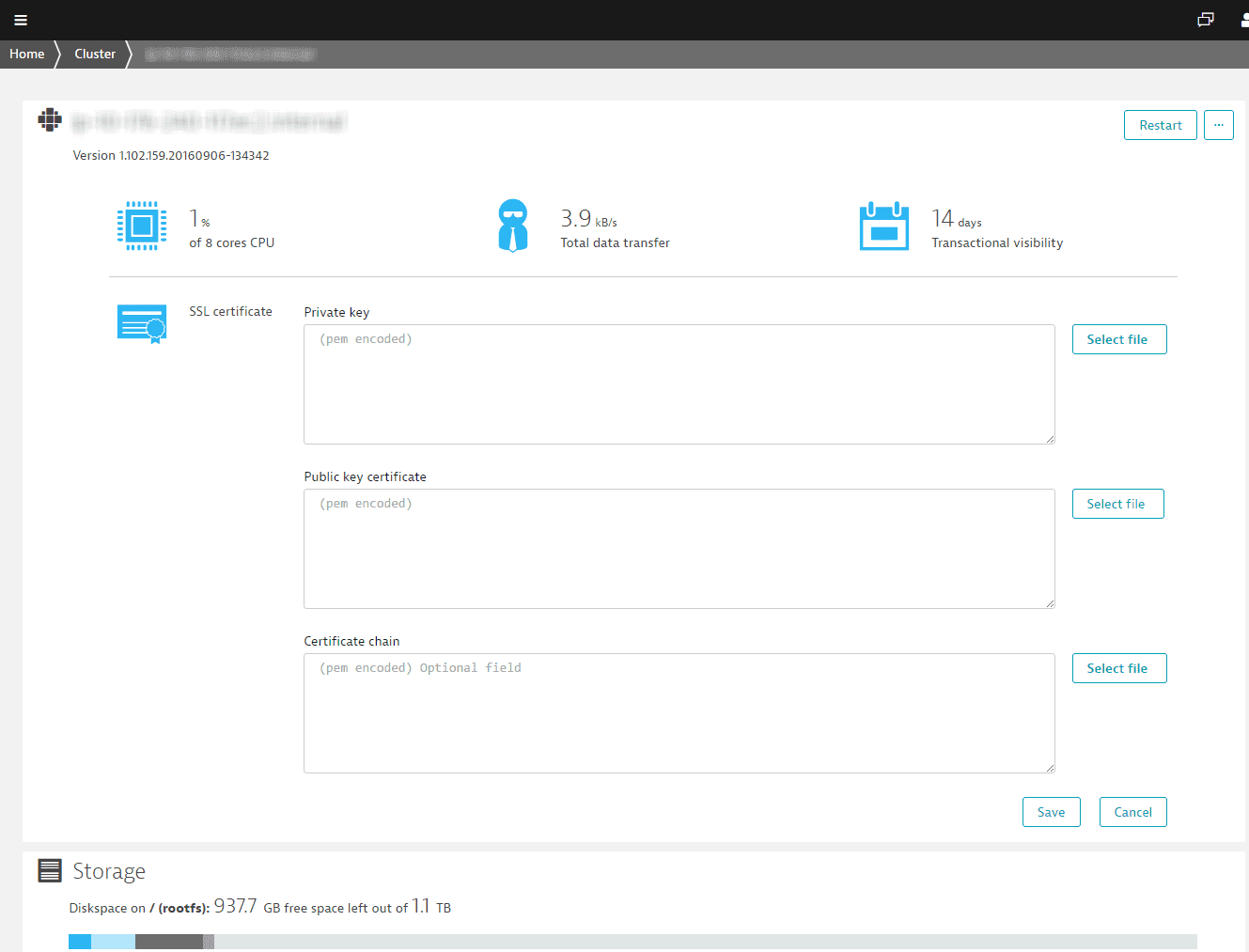
-
You can paste or upload the key files you received from the CA authority.
- Private key: your private key.
- Public key certificate: your server certificate.
- Certificate chain: your root and intermediate certificates.
The key and certificates need to be in PEM format with the full
BEGINheaders andENDfooters.Key header and footer format:
-----BEGIN PRIVATE KEY-----(Private Key)-----END PRIVATE KEY-----Certificate header and footer format:
-----BEGIN CERTIFICATE-----(SSL Certificate)-----END CERTIFICATE----- -
Select Save to upload the certificates.
Your certificate is associated with a specific host name. To avoid a name-mismatch error, make sure that the common name (domain name) in the SSL certificate matches the address displayed in the address bar of the browser.