Data security controls
- 10-min read
Data storage
Your monitoring data remains in your own on-premise data center.
Also see Data retention periods.
Dynatrace components
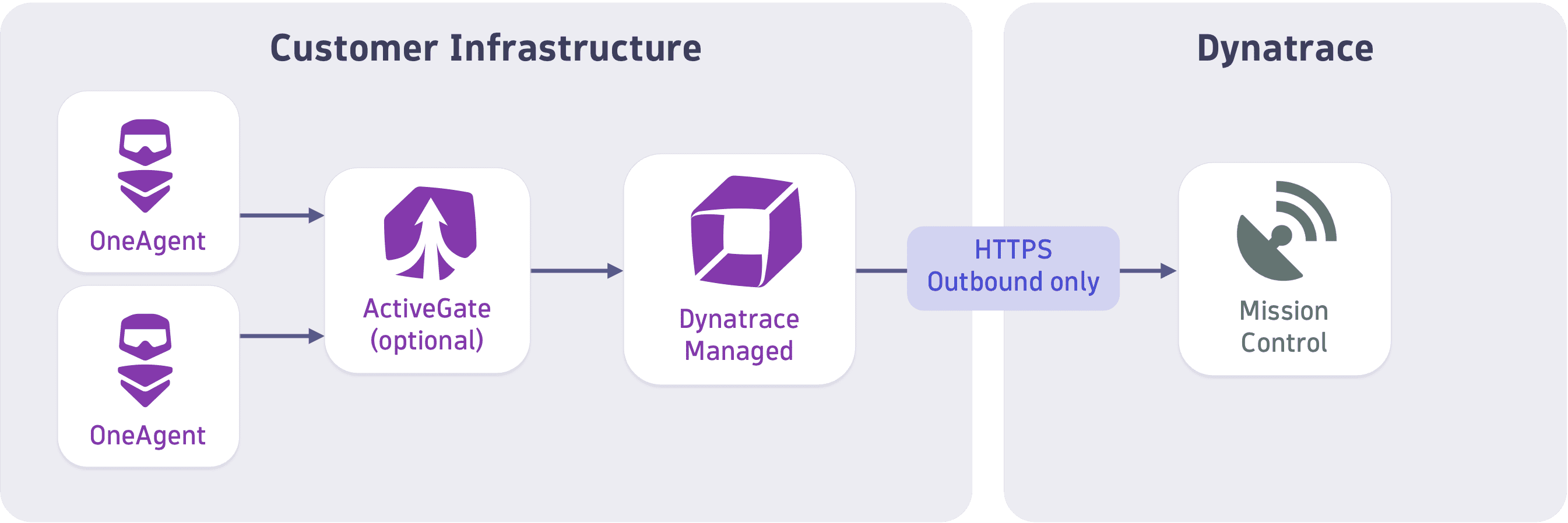
Dynatrace OneAgent collects all monitoring data within your monitored environment. Optionally, all data collected by OneAgent can be routed through a Dynatrace ActiveGate, which works as a proxy between Dynatrace OneAgent and the Dynatrace Cluster. In the absence of an ActiveGate, data collected by OneAgent is sent directly to the Dynatrace Cluster.
Dynatrace Managed clusters periodically exchange information, such as license and consumption data, with Dynatrace Mission Control.
Data segregation between customer environments
Dynatrace Managed allocates one cluster per customer account.
Data encryption at rest
You should configure your own hard disk encryption and manage encryption keys on your own.
Data encryption in transit
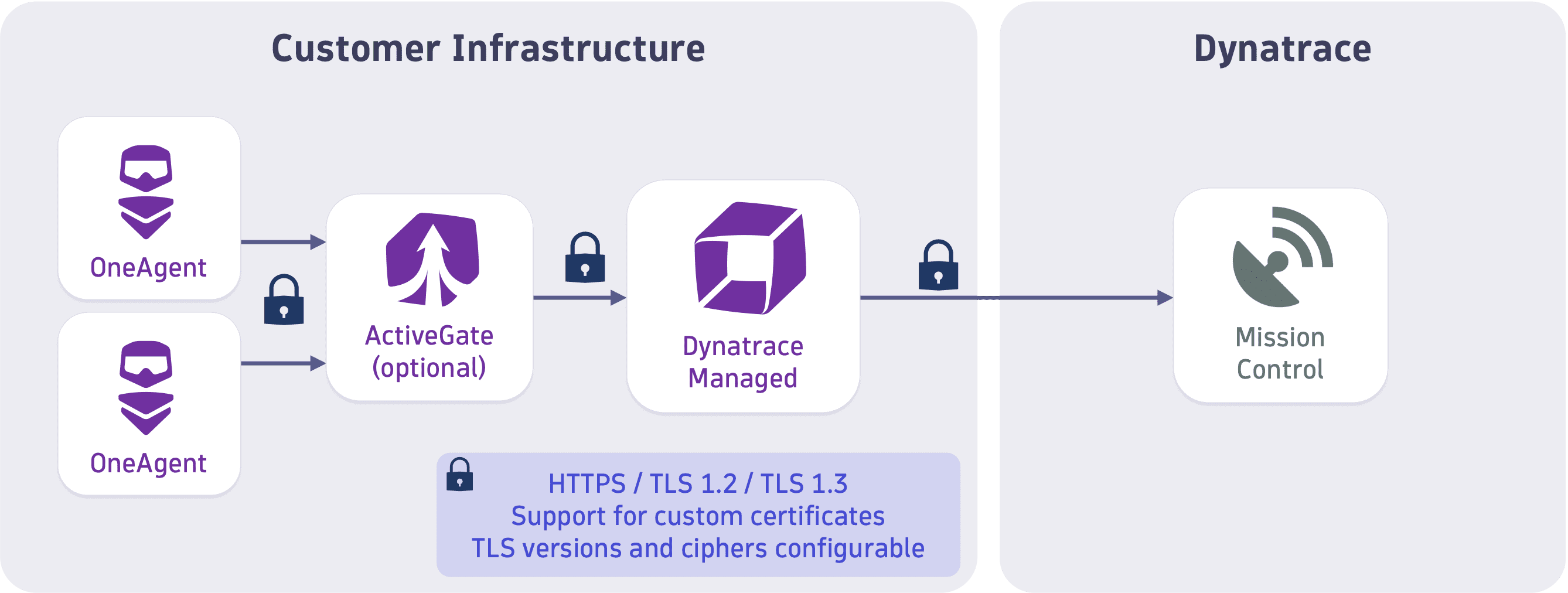
All data exchanged between OneAgent, ActiveGate, and Dynatrace Cluster is encrypted in transit. Data is serialized and deserialized using Google Protocol Buffers.
You can configure TLS versions as well as cipher suites, and you can use your own SSL certificates.
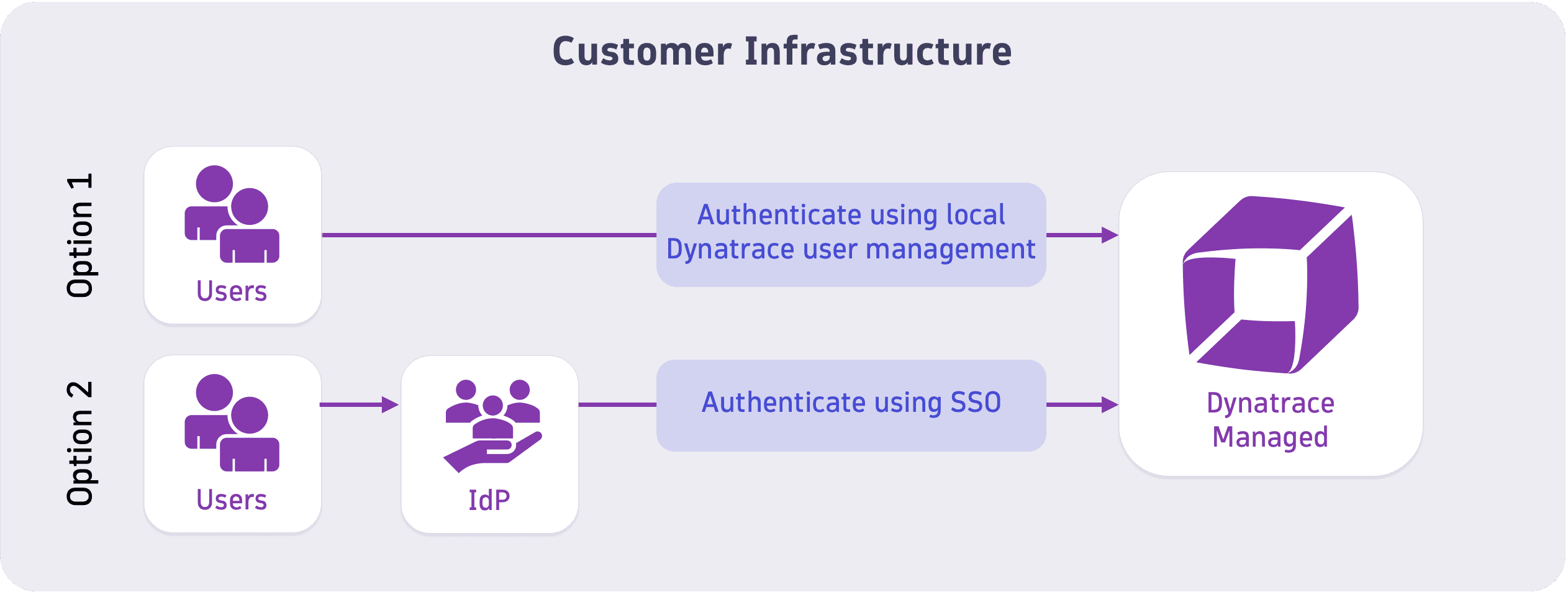
User authentication
Users are managed by configuring user groups, SAML, OpenID, and LDAP.
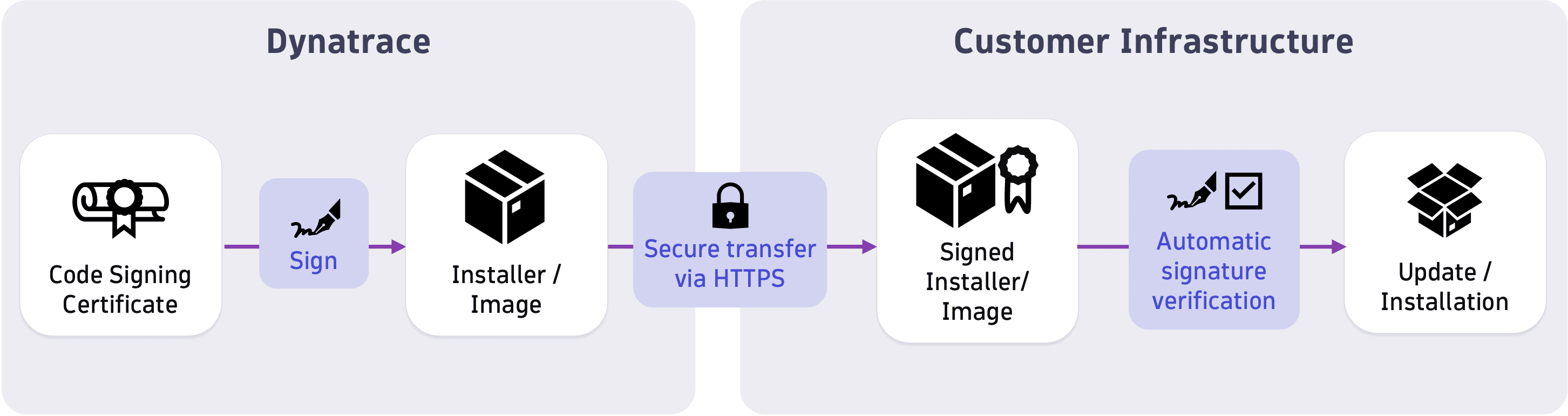
Integrity verification of Dynatrace components
Dynatrace components are signed using code signing certificates within the continuous delivery and integration (CI/CD) pipeline.
Code signing certificates are stored on hardware tokens with Extended Validation (EV) code signing certificates for Windows. Signature verification is performed automatically before an update or installation. When installing a component for the first time, signature verification must be conducted manually.
Business continuity and high-availability
A high-availability setup can be achieved by setting up multiple cluster nodes. The Dynatrace Mission Control team monitors the service quality and hardware utilization of Dynatrace Managed clusters. It uses high-availability multi-node setup and sends alerts when additional hardware is required for monitoring the environment. For more details, download the Managed SLA.
Data backups and disaster recovery
Dynatrace Managed offers a built-in backup mechanism that you must configure.
Infrastructure monitoring
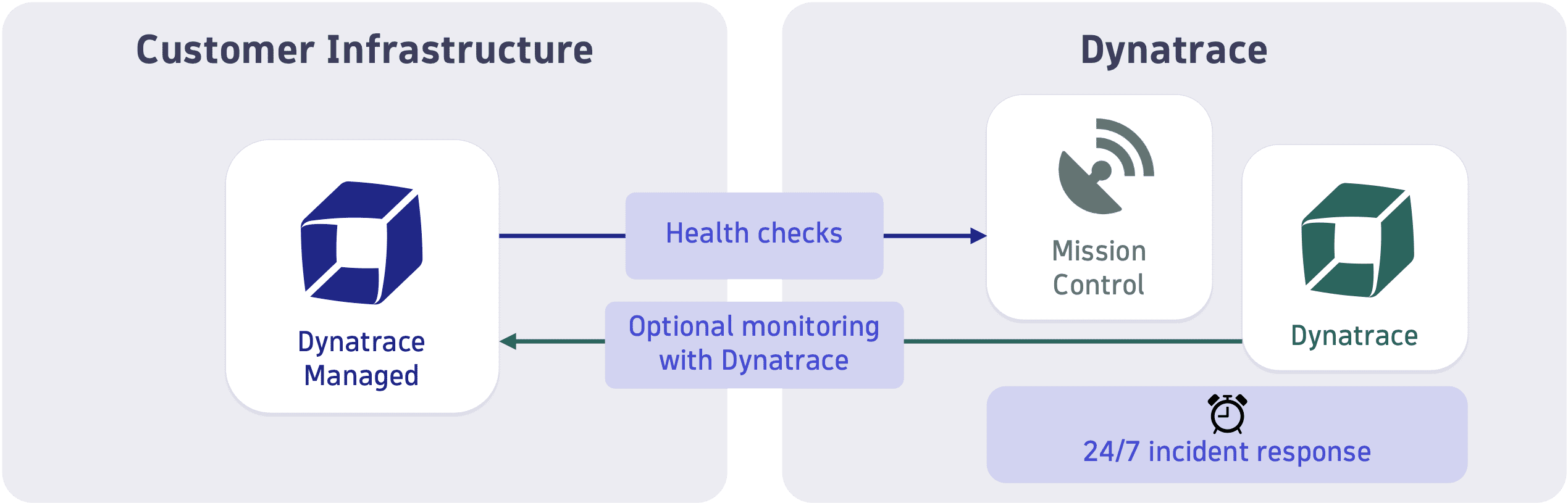
Dynatrace Managed clusters send regular health checks to Dynatrace Mission Control. Optionally, Managed clusters can be monitored by the Dynatrace self-monitoring cluster.
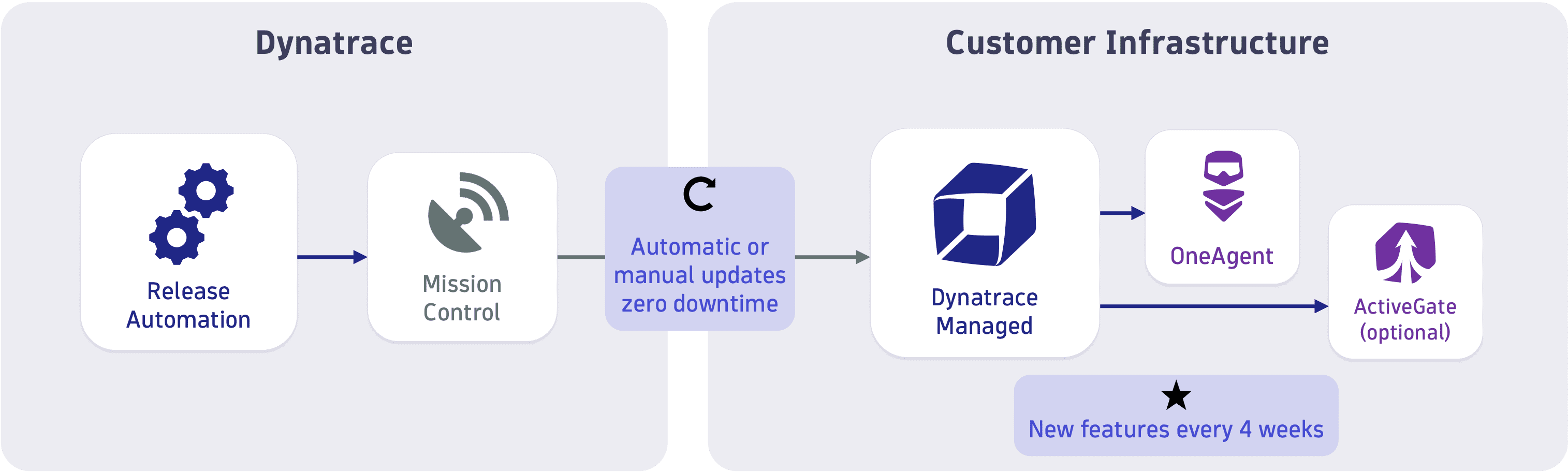
Roll out of updates and hot fixes
Using a fully automated CI/CD pipeline, Dynatrace is able to roll out updates and hot fixes within a few hours. The Dynatrace architecture allows for zero-downtime upgrades of clusters.
Updates are delivered via Dynatrace Mission Control. New features are delivered every 4 weeks. Upgrades of the cluster, OneAgents, and ActiveGates can be performed automatically or manually.
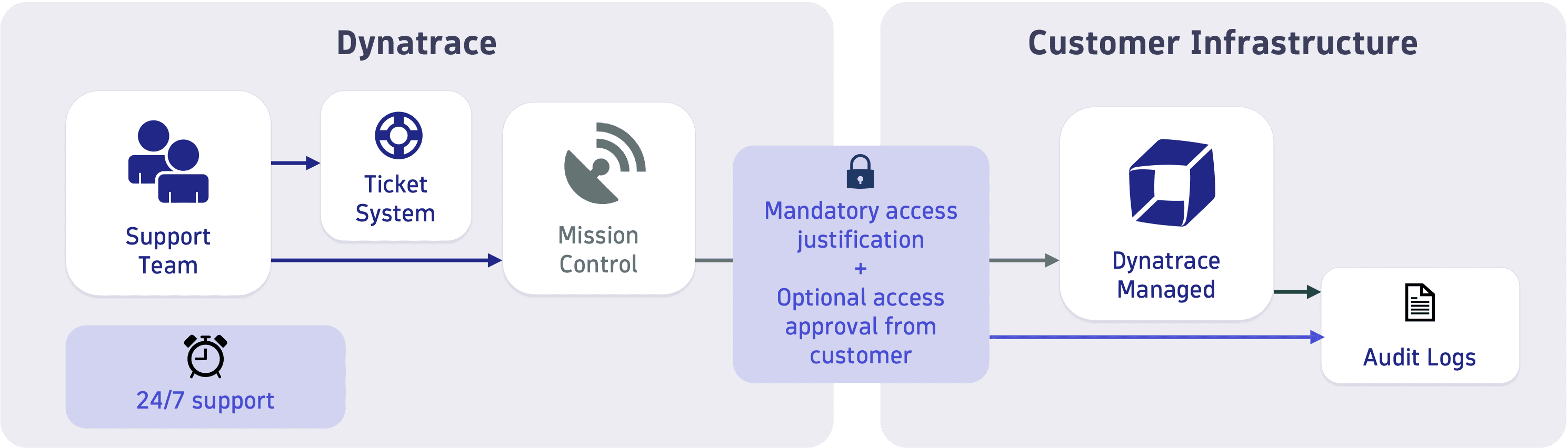
Data access for Dynatrace support
You have complete control over the remote access to your cluster in case support is required. You can turn off remote access or configure it to require approval before access is granted. Dynatrace Support has access to Dynatrace Managed software (application-level) only, not to your underlying infrastructure or the system level.
Remote access is established by Dynatrace Mission Control, which is only accessible from within the Dynatrace corporate network. Remote access by Dynatrace Mission Control requires multi-factor authentication. Each access and any changes made are audit-logged and fully accessible.
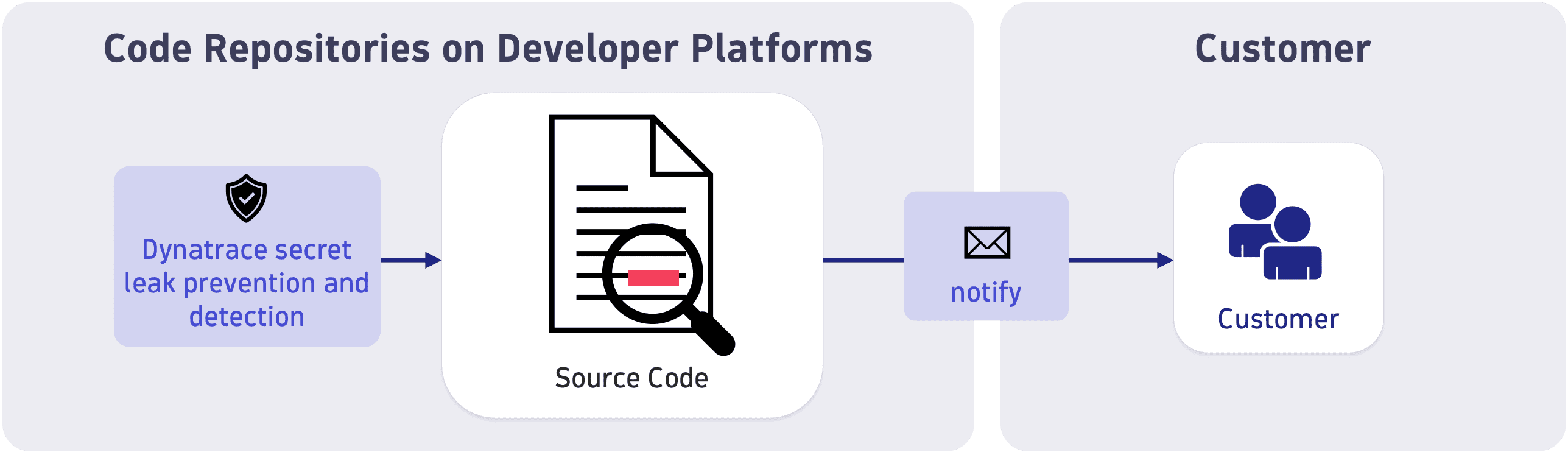
Dynatrace secret leak prevention
Dynatrace can detect and prevent the leakage of Dynatrace secrets in source code repositories on GitHub. These secrets may include platform or API tokens that were inadvertently pushed to a source code repository. If a secret leak is detected, we will reach out to you and aid with remediation measures.
For details on reporting a security issue, see Report a security-related concern.
Compliance, certifications, and audits
Dynatrace undergoes annual, independent third-party audits and conducts penetration tests and red team assessments with independent security firms.
Having achieved several global and local certifications and accreditations demonstrates that we adhere to the most recognized international standards for security management.
Dynatrace also benefits from secure Amazon, Azure, and Google data centers that are certified for ISO 27001, PCI-DSS Level 1, and SOC 1/SSAE-16.
For the full list of certifications, see Trust Center.