Automated threat-alert triaging
- Latest Dynatrace
- Tutorial
Security teams face the challenge of sifting through massive amounts of security data to identify and respond to potential threats, prioritize alerts, and assess the severity of events. Lacking context in place, analysts spend valuable time sorting through the noise, switching between tools, and risking overlooking important information, which leads to delayed responses and inefficiencies in security operations.
The Dynatrace platform addresses this issue by providing security contextualization capabilities, such as threat intelligence enrichment. Various security findings in the Dynatrace platform contain observables, such as IP addresses. Those observables can now be enriched with reputation and other threat contexts, enabling you to
- Classify and prioritize alerts
- Reduce the noise
- Respond to threat alerts fast
Target audience
This article is intended for incident response teams that want to automate the triage of new detections supported by threat intelligence.
Scenario
-
A new security detection finding from Amazon GuardDuty is ingested into the Dynatrace platform.
-
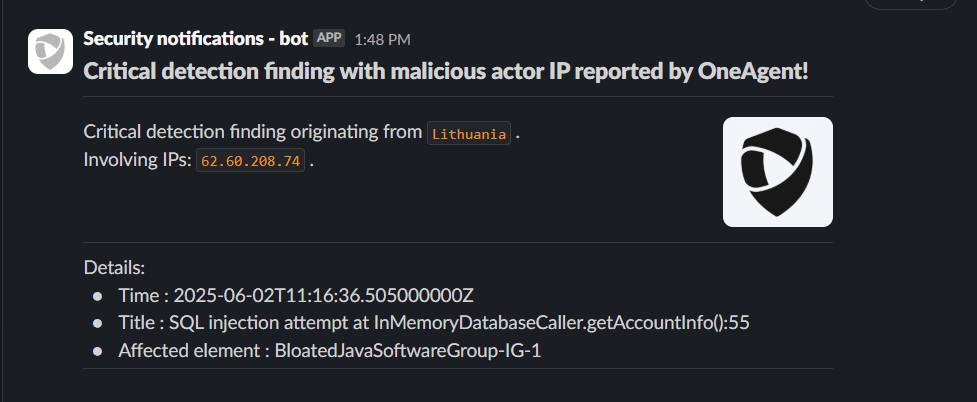
The security team wants to be notified in Slack only about new critical detections from an actor whose IP address is classified as malicious by the AbuseIPDB threat intelligence source.
The same scenario can be applied to other supported integrations for enrichment and security data ingest.
Prerequisites
- Install and configure Amazon GuardDuty integration (or any other supported data ingest integration).
- Install and configure the AbuseIPDB enrichment (or any other supported enrichment integration).
- Users must have the
security-intelligence:enrichments:runpermission to run enrichments.
Get started
1. Import workflow
Import the sample workflow available as a template in the AbuseIPDB app.
- In Dynatrace, open Settings, then search for and select AbuseIPDB.
- In Templates, select and import the sample workflow.
2. Enable enrichment
To run the enrichment workflow action, you need to enable the security-intelligence:enrichments:run permission.
- Go to the settings menu in the upper-right corner of
 Workflows and select Authorization settings.
Workflows and select Authorization settings. - In Secondary permissions, search for and select the
security-intelligence:enrichments:runpermission. - Select Save.
3. Customize workflow
Customize the DQL query action or the Slack notification message to your needs.
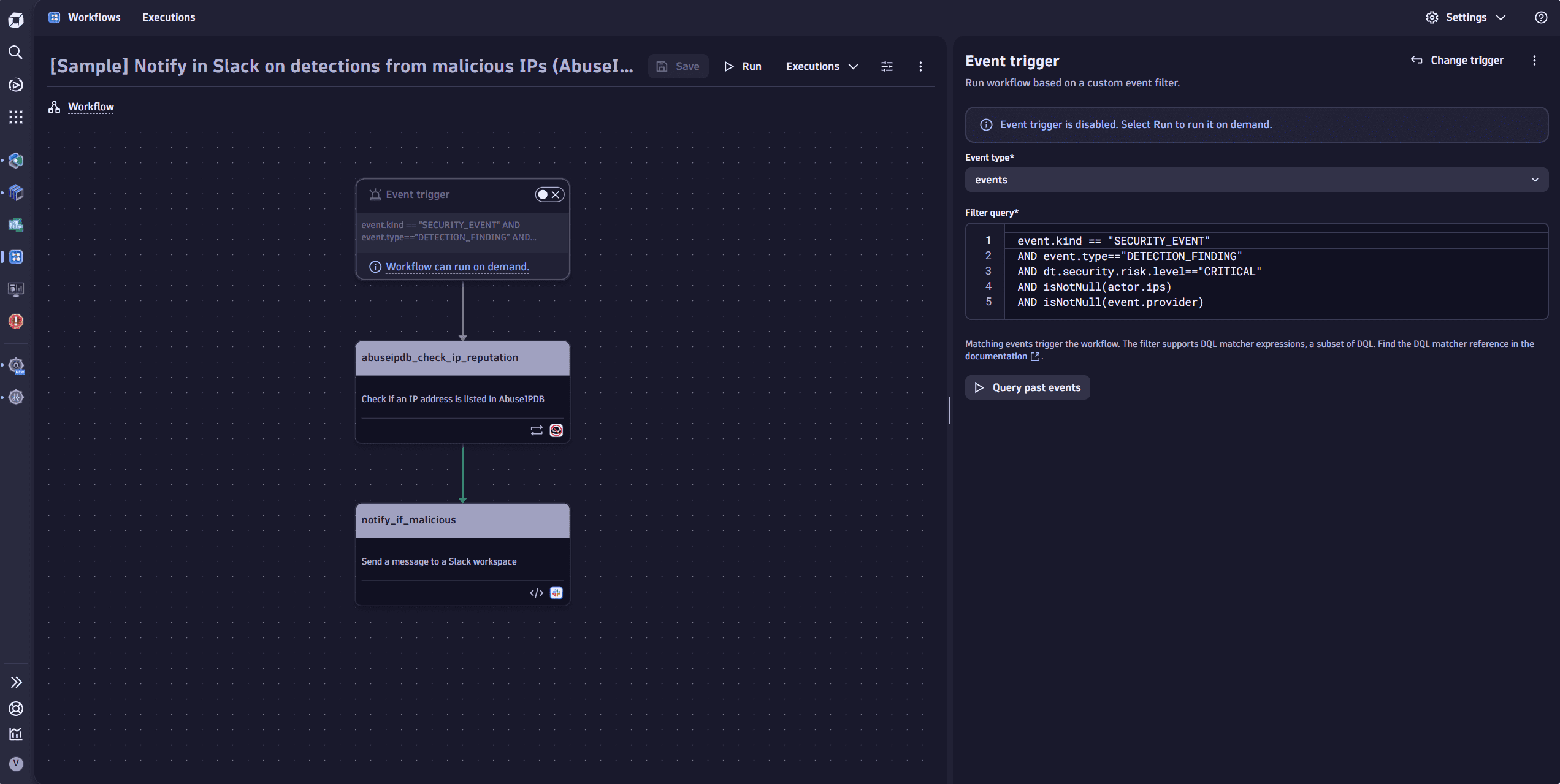
4. Test workflow
Run the workflow to test it.
Example notification:
5. Save workflow
Schedule and save the workflow to be triggered automatically.