Ingest Microsoft Entra ID sign-in logs
- Latest Dynatrace
- How-to guide
Ingest Microsoft Entra ID sign-in logs and analyze them in Dynatrace.
Get started
Overview
In the following, you'll learn how to ingest sign-in logs from your Microsoft Entra ID instance into Grail and monitor them on the Dynatrace platform.
Use cases
With the ingested data, you can leverage Dynatrace platform to monitor your Microsoft Entra ID sign-in activity and access to business-critical organization applications, spotting anomalies and staying ahead of potential threats. For details, see Monitor suspicious sign-in activity with Dynatrace.
Requirements
-
Enable Entra ID sign-in logs forwarding to Dynatrace via either of these options:
- Option 1: Azure log forwarding
- Option 2: Azure Native Dynatrace Service
-
Permissions:
- To query ingested logs:
storage:logs:read.
- To query ingested logs:
Activation and setup
To set up Microsoft Entra ID sign-in log monitoring, follow the steps below.
1. Configure the OpenPipeline built-in processor
-
In Dynatrace, go to
 Settings > Process and contextualize > OpenPipeline and select Logs.
Settings > Process and contextualize > OpenPipeline and select Logs. -
Go to Pipelines and select Pipeline.
-
Under Processing, select Processor > Technology bundle > Azure Entra ID Audit Logs.
-
Select Choose.
-
Enter a name for your Azure pipeline and select Save.
-
Under Dynamic routing, select Dynamic route.
-
Enter the following matching condition:
matchesValue(cloud.provider, "azure") ANDmatchesPhrase(content, "\"SignInLogs\"") -
Select the newly created pipeline, enter a name for the Dynamic route, and select Add.
2. Verify configuration
Verify the configuration by running the following query in  Notebooks:
Notebooks:
fetch logs| filter cloud.provide == "azure"AND isNotNull(audit.action)AND isNotNull(authentication.is_multifactor)
3. Visualize results with our sample dashboard
-
Download our sample dashboard from GitHub.
-
Open
 Dashboards, select
Dashboards, select Upload, then select the downloaded file.
Details
How it works
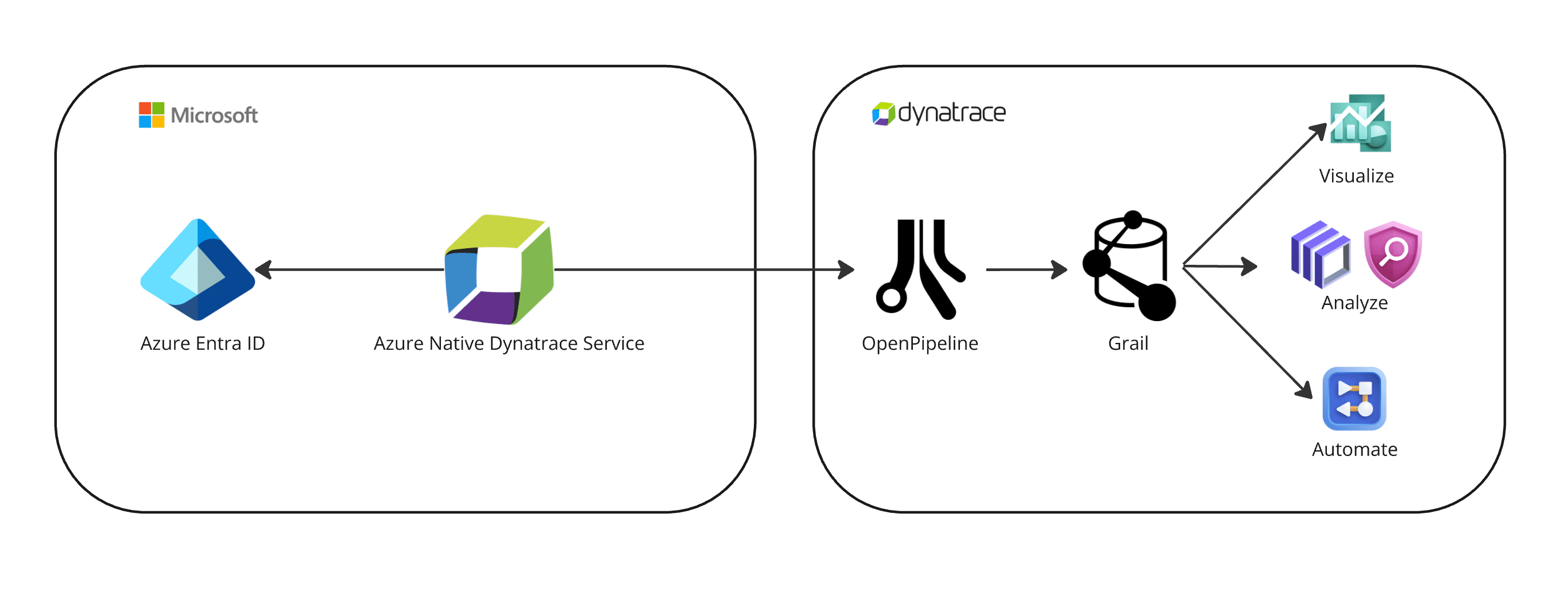
There are two ways to enable Entra ID sign-in logs forwarding to Dynatrace:
- Option 1: Via Azure log forwarding
- Option 2: Via Azure Native Dynatrace Service
See below for details.
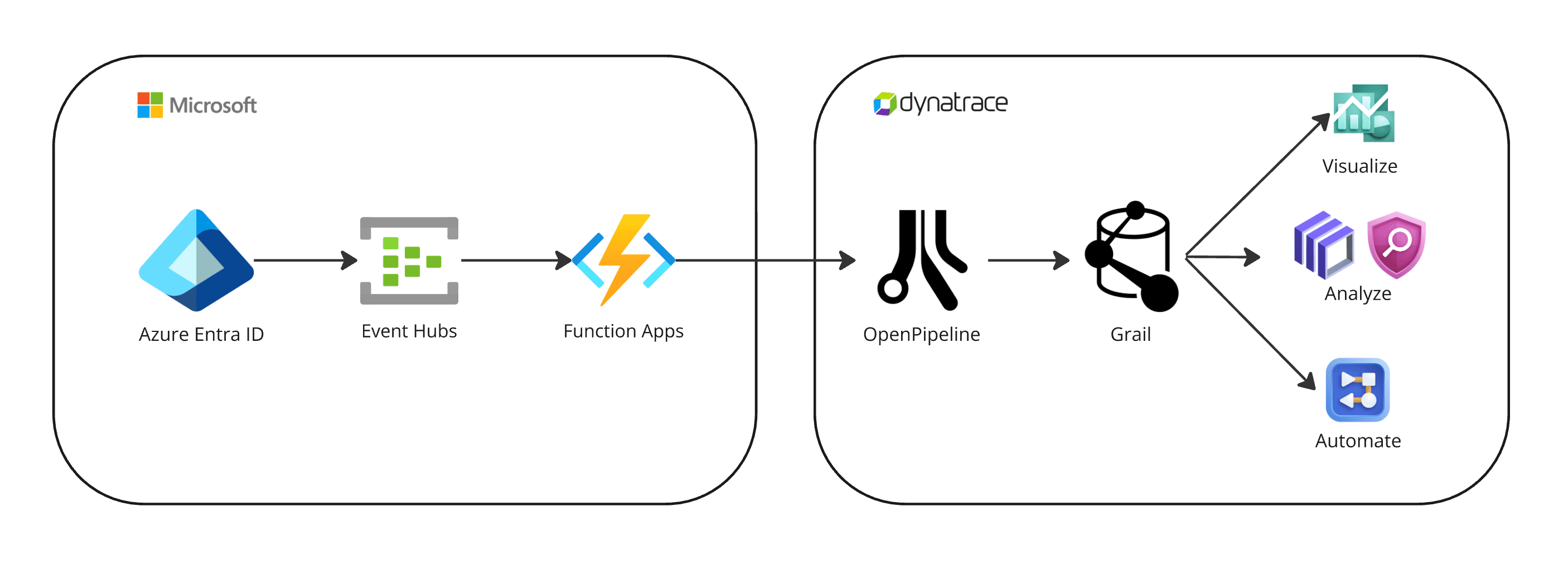
1. Logs are ingested into Dynatrace
-
Microsoft Entra ID continuously exports sign-in logs to Azure Event Hubs.
-
An Azure Function app pre-processes the logs and sends them to Dynatrace, taking advantage of the OpenPipeline dedicated log ingest endpoint.
2. Logs are processed and stored in Grail
-
The fetched data is mapped to the Dynatrace Semantic Dictionary.
-
Data is stored in Grail in a unified format, in a default bucket called
default_logs. For details, see Built-in Grail buckets.
Licensing and cost
For billing information, see Events powered by Grail.