Webhook integration for security notifications
- How-to guide
This page refers to the classic  Third-Party Vulnerabilities and
Third-Party Vulnerabilities and  Code-Level Vulnerabilities apps, which are deprecated. If you're currently using these apps, we recommend transitioning to the unified
Code-Level Vulnerabilities apps, which are deprecated. If you're currently using these apps, we recommend transitioning to the unified  Vulnerabilities in the latest Dynatrace experience, which offers enhanced functionality and ongoing support. For details, see Upgrade to the latest Dynatrace.
Vulnerabilities in the latest Dynatrace experience, which offers enhanced functionality and ongoing support. For details, see Upgrade to the latest Dynatrace.
Integrate security notifications with Dynatrace to pass security issues and/or attacks to your teams for alerting and remediation purposes.
To integrate security notifications using webhooks, follow the instructions below.
Set up notifications for vulnerabilities
To set up notifications for vulnerabilities
 Create an alerting profile
Create an alerting profile
Create an alerting profile, which allows you to set up alert-filtering rules that are based on the risk level of detected vulnerabilities.
-
Go to Settings and select Alerting > Vulnerability alerting profiles.
-
Select Add alerting profile.
-
Enter a Name for the profile on which you want to receive security notifications.
-
Under Alert for the following events, select at least one event type for which you want to receive notifications.
- If Vulnerability (re)opened is turned on and New management zone affected is turned off, you are notified when a vulnerability is opened or reopened.
- If New management zone affected is turned on and Vulnerability (re)opened is turned off, you are notified when an already open vulnerability starts affecting a management zone in your environment that wasn't previously affected.
- If both Vulnerability (re)opened and New management zone affected are turned on, you are notified when a vulnerability is opened or reopened, or when an open vulnerability starts affecting a new management zone.
-
Optional To restrict alerts to one management zone, under Alert only if the following management zone is affected (optional), select the desired management zone from the dropdown list. This way, you are alerted only when the selected management zone is affected by the selected event types. For example, for the New management zone affected event type, you are notified when an open vulnerability that hasn't previously affected your selected management zone starts affecting it.
Only one management zone can be selected per alerting profile.
-
Turn on each risk level for which you want to receive notifications. You can select more than one.
-
Select Save changes to save your configuration.
 Link the alerting profile to a webhook security notifications integration
Link the alerting profile to a webhook security notifications integration
Link the alerting profile to a security notifications integration using webhooks. You can define the webhook integration and configure the payload (in the form of a message template) that you want to receive with your security notifications.
-
Go to Settings and select Integration > Security notifications.
-
Select Add integration and enter the following information.
- Security alert type: Select Vulnerability alert.
- Notification type: Select Custom integration.
- Display name: Enter a name for the webhook integration. This name will be displayed on Settings > Integration > Security notifications after you save this configuration.
- Webhook endpoint URL: Enter the URL of the webhook API endpoint.
-
Optional Choose whether you want to accept any SSL certificate.
- On = Accept any SSL certificate (including self-signed and invalid certificates)
- Off = Dynatrace verifies the SSL certificate of the URL. (Recommended)
-
Select Add HTTP header to specify additional HTTP header fields, such as
Content-TypeorAuthorization. These custom HTTP header fields can be used if the target endpoint needs an authentication token within the HTTP header or if you would like to send different content types such asapplication/json,application/xml,text/plain.The Content-Type field is required, others are optional.
-
In the Custom payload field, customize your notification format and content. Once a vulnerability is detected or resolved, this customizable payload is pushed through an HTTP POST to the target system. Select the Info icon for a list of Available placeholders that you can use for this integration. Placeholders are automatically replaced with information related to the vulnerability when the notification is generated.
Example message template:
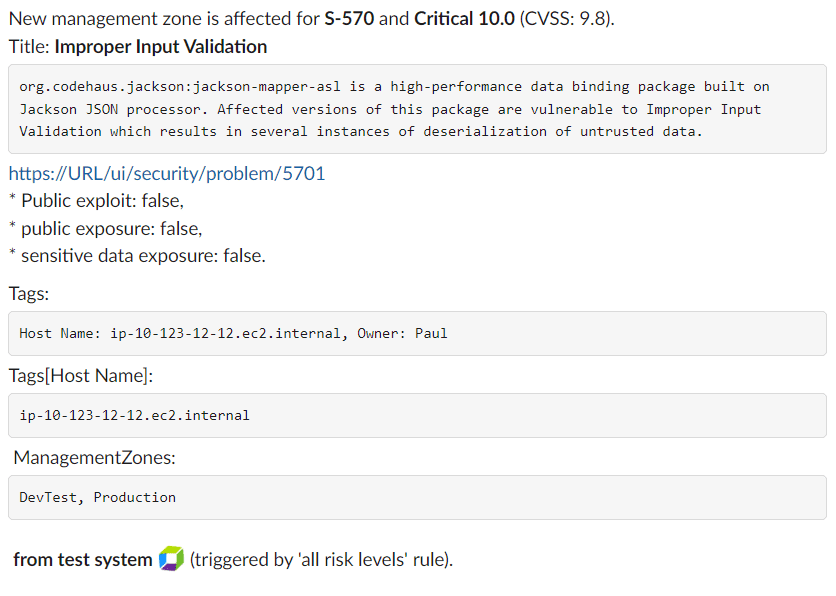
{"text": "New management zone is affected for *{SecurityProblemId}* and *{Severity} {DavisSecurityScore}* (CVSS: {CvssScore}). \nTitle: *{Title}*\n```{Description}```\n{SecurityProblemUrl}\n* Public exploit: {ExploitAvailable}, \n* public exposure: {Exposed}, \n* sensitive data exposure: {SensitiveDataReachable}. \nTags[Host Name]: ```{Tags[Host Name]}``` ManagementZones: ```{ManagementZones} ```\n\n *from test system* :dynatrace: (triggered by 'all risk levels' rule)."}
-
From the Alerting profile list, select the alerting profile on which you want to receive security notifications.
-
Optional To verify your configuration, select Send test notification. If your configuration is correct:
- You should receive a notification on your organization's endpoint.
- The following info message should be displayed on the Dynatrace settings page:
Test notification sent successfully.
-
Save changes.
Example payload:
Verify your configuration
To verify that your integration is set up correctly
- Go to Settings and select Integration > Security notifications.
- Select Details for the integration you want to check.
- Select Send test notification. If your configuration is incorrect and the test notification hasn't been sent to your organization's selected endpoint, you'll receive an error message that will help you identify the problem.
Related topics
 Third-Party Vulnerabilities
Third-Party Vulnerabilities