Network availability monitors
Preview
Network availability monitoring enables you create synthetic network availability monitors of type ICMP, TCP, or DNS.
The Synthetic - Network availability monitors API is part of the Environment API v2. Check the API Explorer (section-api#api-explorer) for more information.
Limitations
Number of requests
The maximum number of requests executed per network availability monitor is 1000.
If a monitor uses target filter, it might not be possible to precisely predict the number of requests in advance of execution (for example, when monitoring an entire host group or a subnet with a wide IP range). In such cases, the limit is applied when target filter is resolved before the monitor's execution into the actual list of addresses.
Operating system
Network availability monitors are not supported on Synthetic-enabled ActiveGate on Windows hosts.
Deployment type
Network availability monitors are supported only on private Synthetic locations.
Containerized locations
Network availability monitors are supported on containerized Synthetic-enabled ActiveGate deployments, but additional permissions are required.
ICMP monitors use the ping executable, which requires the CAP_NET_RAW capability set for the container executing the requests (synthetic-vuc). Additionally, the allowPrivilegeEscalation property of securityContext for this container has to be set to true, because the process that launches the ping executable does not have the required privileges set by default.
The entire securityContext for the synthetic-vuc container with enabled network availability monitors should look as follows.
securityContext:readOnlyRootFilesystem: trueprivileged: falseallowPrivilegeEscalation: truerunAsNonRoot: truecapabilities:drop: ["all"]add: ["NET_RAW"]
POST create a multi-protocol monitor
Monitor schema SyntheticMultiProtocolMonitorUpdateDto
required
This endpoint supports only multi-protocol monitors.
The element can hold the value
MULTI_PROTOCOL.true. If false, the monitor is disabled.See
syntheticMonitorOutageHandlingSettings schema.You can specify only the key (required) and value (optional) of the tag here.
steps schema SyntheticMultiProtocolMonitorStepDto
The element can hold the values
ICMP, TCP, or DNSSee
constraints schema.requestConfigurations schema SyntheticMultiProtocolRequestConfigurationDto
See
constraints schema.constraints schema SyntheticMultiProtocolMonitorConstraintDto
See script configuration constraints for examples.
syntheticMonitorOutageHandlingSettings schema SyntheticMonitorOutageHandlingSettingsDto
globalConsecutiveOutageCountThreshold or more consecutive executions at all configured locations.localConsecutiveOutageCountThreshold or more consecutive executions at localLocationOutageCountThreshold or more locations.Examples
{"name": "Sample NAM monitor with ICMP step","type": "MULTI_PROTOCOL","frequencyMin": "1","locations": ["SYNTHETIC_LOCATION-8A91FE7982E24C06"],"active": "true","steps": [{"name": "ICMP step 1","requestType": "ICMP","targetFilter": null,"targetList": ["127.0.0.1","127.0.0.2","127.0.0.3","127.0.0.4"],"name": "ICMP step 1","requestType": "ICMP","targetFilter": null,"targetList": ["127.0.0.1","127.0.0.2","127.0.0.3","127.0.0.4"],"constraints": [{"type": "SUCCESS_RATE_PERCENT","properties": {"value": "49","operator": ">"}}],"properties": {"ICMP_NUMBER_OF_PACKETS": "3","ICMP_TIMEOUT_FOR_REPLY": "PT1S","ICMP_TIMEOUT_FOR_REPLY": "PT1S"},"requestConfigurations": [{"constraints": [{"type": "ICMP_SUCCESS_RATE_PERCENT","properties": {"value": "100"}}]}]}],"syntheticMonitorOutageHandlingSettings": {"globalOutages": true,"localOutages": false,"globalConsecutiveOutageCountThreshold": 1,"localLocationOutageCountThreshold": null,"localConsecutiveOutageCountThreshold": null},"tags": [{"key": "my-icmp-monitor"},{"key": "env","value": "UAT"}]}
{"name": "Sample NAM monitor with TCP step","type": "MULTI_PROTOCOL","frequencyMin": "1","locations": ["SYNTHETIC_LOCATION-8A91FE7982E24C06"],"active": "true","steps": [{"name": "TCP step 1","requestType": "TCP","targetFilter": "hostGroup == my-host-group0 and ipRange == 45-55.*.*.*","targetList": [],"name": "TCP step 1","requestType": "TCP","targetFilter": "hostGroup == my-host-group0 and ipRange == 45-55.*.*.*","targetList": [],"constraints": [{"type": "SUCCESS_RATE_PERCENT","properties": {"value": "66","operator": ">="}}],"properties": {"TCP_PORT_RANGES": "22,443,5501-5509"},"requestConfigurations": [{"constraints": []}]}],"syntheticMonitorOutageHandlingSettings": {"globalOutages": true,"localOutages": false,"globalConsecutiveOutageCountThreshold": 1,"localLocationOutageCountThreshold": null,"localConsecutiveOutageCountThreshold": null},"tags": [{"key": "my-tcp-monitor"},{"key": "env","value": "UAT"}]}
{"name": "Sample NAM monitor with DNS step","type": "MULTI_PROTOCOL","frequencyMin": 1,"locations": ["SYNTHETIC_LOCATION-6F3084B1ECD81DE1"],"active": true,"steps": [{"name": "DNS step 1","requestType": "DNS","targetFilter": null,"targetList": ["dynatrace.com"],"name": "DNS step 1","requestType": "DNS","targetFilter": null,"targetList": ["dynatrace.com"],"constraints": [{"type": "SUCCESS_RATE_PERCENT","properties": {"value": "90","operator": ">="}}],"properties": {"DNS_RECORD_TYPES": "A,AAAA","DNS_SERVER": "10.102.40.11"},"requestConfigurations": [{"constraints": [{"type": "DNS_STATUS_CODE","properties": {"status": "NOERROR","operator": "="}}]}]}],"syntheticMonitorOutageHandlingSettings": {"globalOutages": true,"localOutages": false,"globalConsecutiveOutageCountThreshold": 1,"localLocationOutageCountThreshold": null,"localConsecutiveOutageCountThreshold": null},"tags": [{"key": "my-dns-monitor"},{"key": "env","value": "UAT"}]}
Available script configuration properties
- 100 milliseconds =
PT0.1S - 500 milliseconds =
PT0.5S - 1 second =
PT1S - 10 seconds =
PT10S - 90 seconds =
PT1M30S - 1 minute =
PT1M - 2 minutes =
PT2M - 5 minutes =
PT5M
ICMP
EXECUTION_TIMEOUTPT1SDefault value =
ICMP_NUMBER_OF_PACKETS × ICMP_TIMEOUT_FOR_REPLY + defaultTimeoutdefaultTimeout = 1sRange =
0–PT2MICMP_NUMBER_OF_PACKETSPing process equivalents are the
-c (Linux) and -n (Windows) parameters.1Range =
1–10ICMP_PACKET_SIZEPing process equivalents are the
-s (Linux) and -l (Windows) parameters.32Range =
0–65500ICMP_TIME_TO_LIVEPing process equivalents are the
-t (Linux) and -i (Windows) parameters.1–255ICMP_TYPE_OF_SERVICEPing process equivalents are the
-Q (Linux) and -v (Windows) parameters.0–255ICMP_DO_NOT_FRAGMENT_DATAPing process equivalents are the
-M do (Linux) and -f (Windows) parameters.true or falseICMP_TIMEOUT_FOR_REPLYPing process equivalents are the
-W (Linux) and -w (Windows) parameters.PT1SIn milliseconds on Windows; values like
PT0.1S are accepted.In seconds on Linux; values like
PT1S are required.Default value =
PT1SRange =
PT1S–PT2STCP
Name
Type
Description
Values
TCP_PORT_RANGES
string
Comma-separated list of port ranges
A single range can be either a single port number or a range of ports, defined as two port numbers with a hyphen.
The final list of requests to be executed is the product of all defined ports and target hosts. For example, if a step has two target hosts (1.1.1.1 and 2.2.2.2) and a range of two ports (80-81), four requests are executed within such a step.
- Request to
1.1.1.1on port80 - Request to
1.1.1.1on port81 - Request to
2.2.2.2on port80 - Request to
2.2.2.2on port81
Sample values
80808000-900080,443,90-100
EXECUTION_TIMEOUT
string:duration
Connection timeout
Valid duration, for example, PT1S
Default timeout = 1s
Range = 0–PT2M
DNS
Name
Type
Description
Values
DNS_RECORD_TYPES
string
Comma-separated list of DNS record types
The final list of requests executed is the product of all defined record types and target hosts. For example, if a step has two record types (A,AAAA) and two target hosts (host1.domain.com and host2.domain.com), four requests are executed within such a step.
- Request for
Arecord contents forhost1.domain.com - Request for
AAAArecord contents forhost1.domain.com - Request for
Arecord contents forhost2.domain.com - Request or
AAAArecord contents forhost2.domain.com
Sample values
AA,AAAAA,AAAA,CNAME
EXECUTION_TIMEOUT
string:duration
Connection timeout
Valid duration, for example, PT1S
Default timeout = 2s
Range = 0–PT2M
DNS_SERVER
string
Address of the DNS server to query, with optional port
If a hostname is provided, it's resolved to an IP address using the system default DNS server.
Valid address, such as:
1.1.1.18.4.4.8:53dns.googledns9.quad9.net:53
If only host is provided, the default port 53 is used.
If no value is provided, the system default DNS server and port are used.
DNS_FORCE_TCP
boolean
By default, the DNS server is queried over a UDP connection, unless the message is too large to fit the UDP datagram. This option allows you to specify a TCP connection instead.
true or false
Default value = false
Script configuration constraints
Constraints describe success conditions.
Step-level constraints
SUCCESS_RATE_PERCENT
Percentage of successful requests in a step
Actual success rate = ratio of the number of requests that didn't fail (successful + skipped requests) to all requests
For example, if 1 request has failed, 2 requests are skipped, and 3 requests are successful, the ratio is (2+3)/6 = 83.33%.
operator>=, >, <=, <, =, or !=Default value =
>=value0Range =
0–100{"type": "SUCCESS_RATE_PERCENT","properties": {"value": "83","operator": ">"}}
ICMP request constraints
ICMP_SUCCESS_RATE_PERCENT
Percentage of successful pings (echo requests) in a request
Actual success rate = ratio of number of the packets received to number of packets sent
For example, if 5 packets were sent and 4 packets were received, the ratio is 4/5 = 80.00%.
operator>=, >, <=, <, =, or !=Default value =
>=value0Range =
0–100{"type": "ICMP_SUCCESS_RATE_PERCENT","properties": {"value": "79","operator": ">"}}
TCP request constraints
TCP_PORT_UNREACHABLE
This is a special constraint that inverts the execution status for TCP requests. It should be applied if it's expected that the port being checked is unreachable.
This constraint has no configuration properties.
If this constraint is applied:
- When the
Execution timeout (12033)andTCP socket connection error (22000)statuses are detected after performing a connection attempt, they are interpreted asHEALTHY (0). - The
HEALTHY (0)connection status is interpreted asCONSTRAINT_VIOLATED (1401)because we expected a failure. - The
UNEXPECTED_ERROR (-1)andUNKNOWN_HOST (12013)statuses are preserved and reported as is.
{"type": "TCP_PORT_UNREACHABLE","properties": {}}
DNS request constraints
DNS_STATUS_CODE
Verifies the DNS response status code, which indicates whether a query was successful or not.
operator= or !=Default value =
=statusCodeExclusive with
status0Default value =
0Range =
0–65535statusExclusive with
statusCodeNOERRORDefault value =
NOERROR{"type": "DNS_STATUS_CODE","properties": {"operator": "=","statusCode": "0"}}
{"type": "DNS_STATUS_CODE","properties": {"operator": "=","status": "NOERROR"}}
DNS_IP_ADDRESS
Verifies the IP address value returned in A/AAAA records.
quantifierany (at least one) or allDefault value =
anyoperator=, != or inDefault values =
-
= for an address-
in for a subnetrecordTypeA or AAAADefault values =
-
A if address/subnet is IPv4-
AAAA if address/subnet is IPv6addressOnly with the operators
=, !=Exclusive with
subnet192.168.0.1, 2001:db8::2:1subnetOnly with the operator
inExclusive with
address172.22.80.0/20, 2001:db8:85a3::0/48{"constraintType": "DNS_IP_ADDRESS","attributes": {"quantifier": "any","recordType": "A","operator": "=","address": "54.208.9.71"}}
{"constraintType": "DNS_IP_ADDRESS","attributes": {"quantifier": "all","recordType": "A","operator": "in","subnet": "10.102.44.0/24"}}
DNS_RECORD_COUNT
Verifies the count of records of a given type.
operator>=, >, <=, <, =, or !=Default value =
>recordTypeMXvalue2Default value =
0Range =
0–65535{"constraintType": "DNS_RECORD_COUNT","attributes": {"recordType": "A","operator": ">","value": "0"}}
DNS_TIME_TO_LIVE
Verifies the time to live (TTL) of records of a given type.
quantifierany (at least one) or allDefault value =
anyoperator>=, >, <=, <, =, or !=Default value =
>recordTypeNSvalue3600Default value =
0Range =
0–2147483647{"constraintType": "DNS_TIME_TO_LIVE","attributes": {"quantifier": "any","recordType": "A","operator": ">=","value": "30"}}
DNS_RECORD_VALUE
Verifies the raw value of records of a given type, with the value format depending on the record type.
Constraints process all records in a response, regardless of the section to which they belong (answer, authority, or additional).
quantifierany (at least one) or allDefault value =
anyoperator-
contains checks if the record value contains a given sequence.-
matches checks if record value matches a given pattern.contains or matchesDefault value =
containsrecordTypeTXTsequenceOnly with the operator
containsExclusive with
patternms71815323pattern* denoting 0 or more charactersOnly with the operator
matchesExclusive with
sequence"v=spf1 include:*{"constraintType": "DNS_RECORD_VALUE","attributes": {"quantifier": "any","recordType": "TXT","operator": "contains","sequence": "ms71815323"}}
{"constraintType": "DNS_RECORD_VALUE","attributes": {"quantifier": "any","recordType": "TXT","operator": "matches","pattern": "\"v=spf1 include:*"}}
Target filter
With the target filter, you can select hosts monitored by Dynatrace based on tags (tag), host ID (hostId), host ID (hostId), host groups (hostGroup), management zones (managementZone), IP mask (ipMask) and IP range (ipRange).
Syntax
- Logical operators
ANDandOR(case insensitive) - Parentheses
- Expression operators
==and!= - Tag names and values
- The function of "not" is handled by
!=. - Wildcard supported
*—select all hosts monitored by Dynatrace.
Examples
tag == tagname or hostGroup == group1(tag == tagname1 or tag == tagname2) and (hostGroup == group1 or managementZone == zone1)tag != tagname1 and tag != tagname2:tagvaluetag == tagname:tagvalue and (managementZone == zone1 or managementZone == zone2)hostGroup == my-trunk-group and ipRange == 32-55.*.*.*ipMask == 127.0.0.1/24
Metrics and dimensions
Dimensions (all network availability monitors)
multi_protocol.request.typeicmp, tcpmulti_protocol.request.target_address54.171.216.19dt.entity.hostHOST-024C103F7F86A290dt.entity.synthetic_locationSYNTHETIC_LOCATION-A4F834D72840EFC1dt.entity.multiprotocol_monitorMULTIPROTOCOL_MONITOR-3F6C9D500287BBAFmulti_protocol.step.id1multi_protocol.request.id2multi_protocol.result.statusHEALTHY, CONSTRAINT_VIOLATEDmulti_protocol.result.status.code0, 1401Monitor metrics (all network availability monitors)
dt.synthetic.multi_protocol.execution_time(latest Dynatrace)
builtin:synthetic.multiProtocol.executionTime(previous Dynatrace)
dt.entity.synthetic_locationdt.entity.multiprotocol_monitorMetric available only if visit execution took place; both start time and end times must be available.
dt.synthetic.multi_protocol.success_rate(latest Dynatrace)
builtin:synthetic.multiProtocol.successRate(previous Dynatrace)
dt.entity.synthetic_locationdt.entity.multiprotocol_monitorWe take into account steps that were actually executed rather than steps intended to be executed. For example, with 2 successful steps, 1 failed step, and 8 not started, the ratio is 2/3, or 66.67%.
dt.synthetic.multi_protocol.availability(latest Dynatrace)
builtin:synthetic.multiProtocol.availability(previous Dynatrace)
dt.entity.synthetic_locationdt.entity.multiprotocol_monitor- 100% for code=
0: HEALTHY, SCRIPT_FINISH, SKIPPED- 0% for error status codes such as
1401 - CONSTRAINT_VIOLATEDdt.synthetic.multi_protocol.executions(latest Dynatrace)
builtin:synthetic.multiProtocol.executions(previous Dynatrace)
dt.entity.synthetic_locationdt.entity.multiprotocol_monitormulti_protocol.result.statusmulti_protocol.result.status.codedt.synthetic.multi_protocol.availability.excluding_maintenance_windows(latest Dynatrace)
builtin:synthetic.multiProtocol.availability.excludingMaintenanceWindows(previous Dynatrace)
dt.entity.synthetic_locationdt.entity.multiprotocol_monitor- 100% for code=
0: HEALTHY, SCRIPT_FINISH, SKIPPED- 0% for error status codes such as
1401 - CONSTRAINT_VIOLATEDStep metrics (all network availability monitors)
dt.synthetic.multi_protocol.step.execution_time(latest Dynatrace)
builtin:synthetic.multiProtocol.step.executionTime(previous Dynatrace)
multi_protocol.request.typedt.entity.synthetic_locationdt.entity.multiprotocol_monitormulti_protocol.step.idMetric available only if step execution took place, with a well-defined end time; therefore, it's not available for skipped steps.
dt.synthetic.multi_protocol.step.success_rate(latest Dynatrace)
builtin:synthetic.multiProtocol.step.successRate(previous Dynatrace)
multi_protocol.request.typedt.entity.synthetic_locationdt.entity.multiprotocol_monitormulti_protocol.step.idIf a step was skipped (by any of its preceding steps), it doesn't have a success rate; we treat it as if it wasn't executed.
If a step doesn't have executed requests (because its pre-execution script failed or issued
SCRIPT_FINISH), we return the value 0% (for failures) or 100% (for finished).For example, with 2 successful, 1 failed, and 4 skipped requests, the ratio is 6/7, or 85.71%.
dt.synthetic.multi_protocol.step.availability(latest Dynatrace)
builtin:synthetic.multiProtocol.step.availability(previous Dynatrace)
multi_protocol.request.typedt.entity.synthetic_locationdt.entity.multiprotocol_monitormulti_protocol.step.id- 100% for code=
0: HEALTHY, SCRIPT_FINISH, SKIPPED- 0% for error status codes such as
1401 - CONSTRAINT_VIOLATEDdt.synthetic.multi_protocol.step.executions(latest Dynatrace)
builtin:synthetic.multiProtocol.step.executions(previous Dynatrace)
multi_protocol.request.typedt.entity.synthetic_locationdt.entity.multiprotocol_monitormulti_protocol.step.idmulti_protocol.result.statusmulti_protocol.result.status.codedt.synthetic.multi_protocol.step.availability.excluding_maintenance_windows(latest Dynatrace)
builtin:synthetic.multiProtocol.step.availability.excludingMaintenanceWindows(previous Dynatrace)
multi_protocol.request.typedt.entity.synthetic_locationdt.entity.multiprotocol_monitormulti_protocol.step.id- 100% for code=
0: HEALTHY, SCRIPT_FINISH, SKIPPED- 0% for error status codes such as
1401 - CONSTRAINT_VIOLATEDRequest metrics (all network availability monitors)
dt.synthetic.multi_protocol.request.availability(latest Dynatrace)
builtin:synthetic.multiProtocol.request.availability(previous Dynatrace)
multi_protocol.request.typemulti_protocol.request.target_addressdt.entity.host (only for monitors with filter defined)dt.entity.synthetic_locationdt.entity.multiprotocol_monitormulti_protocol.step.idmulti_protocol.request.id- 100% for code=
0: HEALTHY, SCRIPT_FINISH, SKIPPED- 0% for error status codes such as
1401 - CONSTRAINT_VIOLATEDdt.synthetic.multi_protocol.request.executions(latest Dynatrace)
builtin:synthetic.multiProtocol.request.executions(previous Dynatrace)
multi_protocol.request.typemulti_protocol.request.target_addressdt.entity.host (only for monitors with filter defined)dt.entity.synthetic_locationdt.entity.multiprotocol_monitormulti_protocol.step.idmulti_protocol.request.idmulti_protocol.result.statusmulti_protocol.result.status.codedt.synthetic.multi_protocol.request.availability.excluding_maintenance_windows(latest Dynatrace)
builtin:synthetic.multiProtocol.request.availability.excludingMaintenanceWindows(previous Dynatrace)
multi_protocol.request.typemulti_protocol.request.target_addressdt.entity.host (only for monitors with filter defined)dt.entity.synthetic_locationdt.entity.multiprotocol_monitormulti_protocol.step.idmulti_protocol.request.id- 100% for code=
0: HEALTHY, SCRIPT_FINISH, SKIPPED- 0% for error status codes such as
1401 - CONSTRAINT_VIOLATEDICMP monitor metrics
dt.synthetic.multi_protocol.icmp.success_rate(latest Dynatrace)
builtin:synthetic.multiProtocol.icmp.successRate(previous Dynatrace)
multi_protocol.request.typemulti_protocol.request.target_addressdt.entity.host (only for monitors with filter defined)dt.entity.synthetic_locationdt.entity.multiprotocol_monitormulti_protocol.step.idmulti_protocol.request.idDoesn't take into account the configured number of packets to be sent.
For example, out of 10 packets to be sent, if 5 were sent and 4 were received, the ratio is 4/5, or 80.00%.
dt.synthetic.multi_protocol.icmp.packets_sent(latest Dynatrace)
builtin:synthetic.multiProtocol.icmp.packetsSent(previous Dynatrace)
multi_protocol.request.typemulti_protocol.request.target_addressdt.entity.host (only for monitors with filter defined)dt.entity.synthetic_locationdt.entity.multiprotocol_monitormulti_protocol.step.idmulti_protocol.request.iddt.synthetic.multi_protocol.icmp.packets_received(latest Dynatrace)
builtin:synthetic.multiProtocol.icmp.packetsReceived(previous Dynatrace)
multi_protocol.request.typemulti_protocol.request.target_addressdt.entity.host (only for monitors with filter defined)dt.entity.synthetic_locationdt.entity.multiprotocol_monitormulti_protocol.step.idmulti_protocol.request.iddt.synthetic.multi_protocol.icmp.average_round_trip_time(latest Dynatrace)
builtin:synthetic.multiProtocol.icmp.averageRoundTripTime(previous Dynatrace)
multi_protocol.request.typemulti_protocol.request.target_addressdt.entity.host (only for monitors with filter defined)dt.entity.synthetic_locationdt.entity.multiprotocol_monitormulti_protocol.step.idmulti_protocol.request.iddt.synthetic.multi_protocol.icmp.min_round_trip_time(latest Dynatrace)
builtin:synthetic.multiProtocol.icmp.minRoundTripTime(previous Dynatrace)
multi_protocol.request.typemulti_protocol.request.target_addressdt.entity.host (only for monitors with filter defined)dt.entity.synthetic_locationdt.entity.multiprotocol_monitormulti_protocol.step.idmulti_protocol.request.iddt.synthetic.multi_protocol.icmp.max_round_trip_time(latest Dynatrace)
builtin:synthetic.multiProtocol.icmp.maxRoundTripTime(previous Dynatrace)
multi_protocol.request.typemulti_protocol.request.target_addressdt.entity.host (only for monitors with filter defined)dt.entity.synthetic_locationdt.entity.multiprotocol_monitormulti_protocol.step.idmulti_protocol.request.iddt.synthetic.multi_protocol.icmp.request_execution_time(latest Dynatrace)
builtin:synthetic.multiProtocol.icmp.requestExecutionTime(previous Dynatrace)
multi_protocol.request.typemulti_protocol.request.target_addressdt.entity.host (only for monitors with filter defined)dt.entity.synthetic_locationdt.entity.multiprotocol_monitormulti_protocol.step.idmulti_protocol.request.idThis metric is always provided, even if actual request execution did not take place (for example, because of exceptions or timeouts).
Diagnostic metric—allows for validation of external ping process execution time.
TCP monitor dimensions
multi_protocol.request.tcp_port_number665TCP monitor metrics
dt.synthetic.multi_protocol.tcp.connection_time(latest Dynatrace)
builtin:synthetic.multiProtocol.tcp.connectionTime(previous Dynatrace)
multi_protocol.request.typemulti_protocol.request.target_addressdt.entity.host (only for monitors with filter defined)dt.entity.synthetic_locationdt.entity.multiprotocol_monitormulti_protocol.step.idmulti_protocol.request.idmulti_protocol.request.tcp_port_numberMetric available only if request execution took place (with no exceptions or timeouts), with a well-defined end time
DNS monitor dimensions
multi_protocol.request.dns_record_typeA, AAAA, CNAMEDNS monitor metrics
dt.synthetic.multi_protocol.dns.resolution_time(latest Dynatrace)
builtin:synthetic.multiProtocol.dns.resolutionTime(previous Dynatrace)
multi_protocol.request.typemulti_protocol.request.target_addressdt.entity.host (only for monitors with filter defined)dt.entity.synthetic_locationdt.entity.multiprotocol_monitormulti_protocol.step.idmulti_protocol.request.idMetric available only if request execution took place (with no exceptions or timeouts), with a well-defined end time
Execution statuses
All network availability monitors
0 HEALTHY-1 UNEXPECTED_ERROR1401 CONSTRAINT_VIOLATED1604 VALIDATION_ERROR12013 UNKNOWN_HOST- Invalid hostname
- DNS server unreachable
- DNS cache issues
- Firewall or proxy interference
12033 Execution timeout- Network issues
- Slow or unresponsive server or service
- Connection blocked by firewall rules
- Timeout is too small.
TCP monitor execution statuses
22000 TCP socket connection errorjava.net.SocketException is thrown during the connection attempt. There can be several issues that can cause this error.- Service is not listening on the specified port.
- Service reached resource or connection limit.
- Service became unavailable during the socket connection process.
Sample DQL queries to extract data
Latest Dynatrace
These examples use Notebooks  and demonstrate how to work with the results of network availability monitors. They use result metrics as a starting point to explore possibilities of extracting and interpreting data with DQL.
and demonstrate how to work with the results of network availability monitors. They use result metrics as a starting point to explore possibilities of extracting and interpreting data with DQL.
Host entity status for ICMP requests
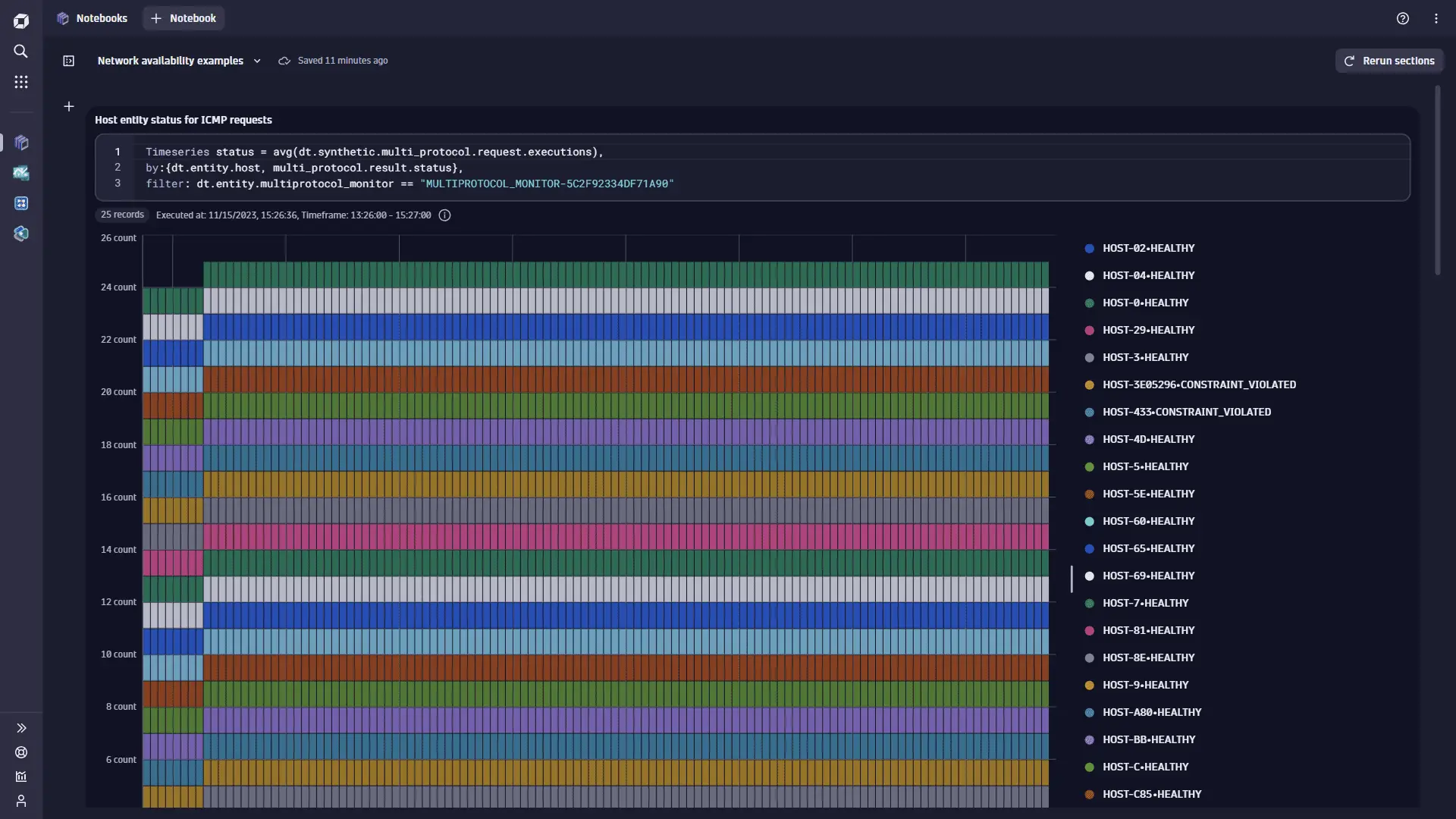
The monitor MULTIPROTOCOL_MONITOR-5C2F92334DF71A90 executes ICMP requests and filters monitored hosts with "targetFilter": "hostGroup == e2e-synthetic-private-location" (which resolves to about 26 hosts). By using the dt.synthetic.multi_protocol.request.executions metric and splitting it by the dt.entity.host and multi_protocol.result.status dimensions, we can display the status of the connection to a particular monitored host entity in this host group. Some hosts do not fulfill expected success rate; instead of being HEALTHY, their requests are marked as CONSTRAINT_VIOLATED.
Timeseries status = avg(dt.synthetic.multi_protocol.request.executions),by:{dt.entity.host, multi_protocol.result.status},filter: dt.entity.multiprotocol_monitor == "MULTIPROTOCOL_MONITOR-5C2F92334DF71A90"
Number of ICMP packets sent and received
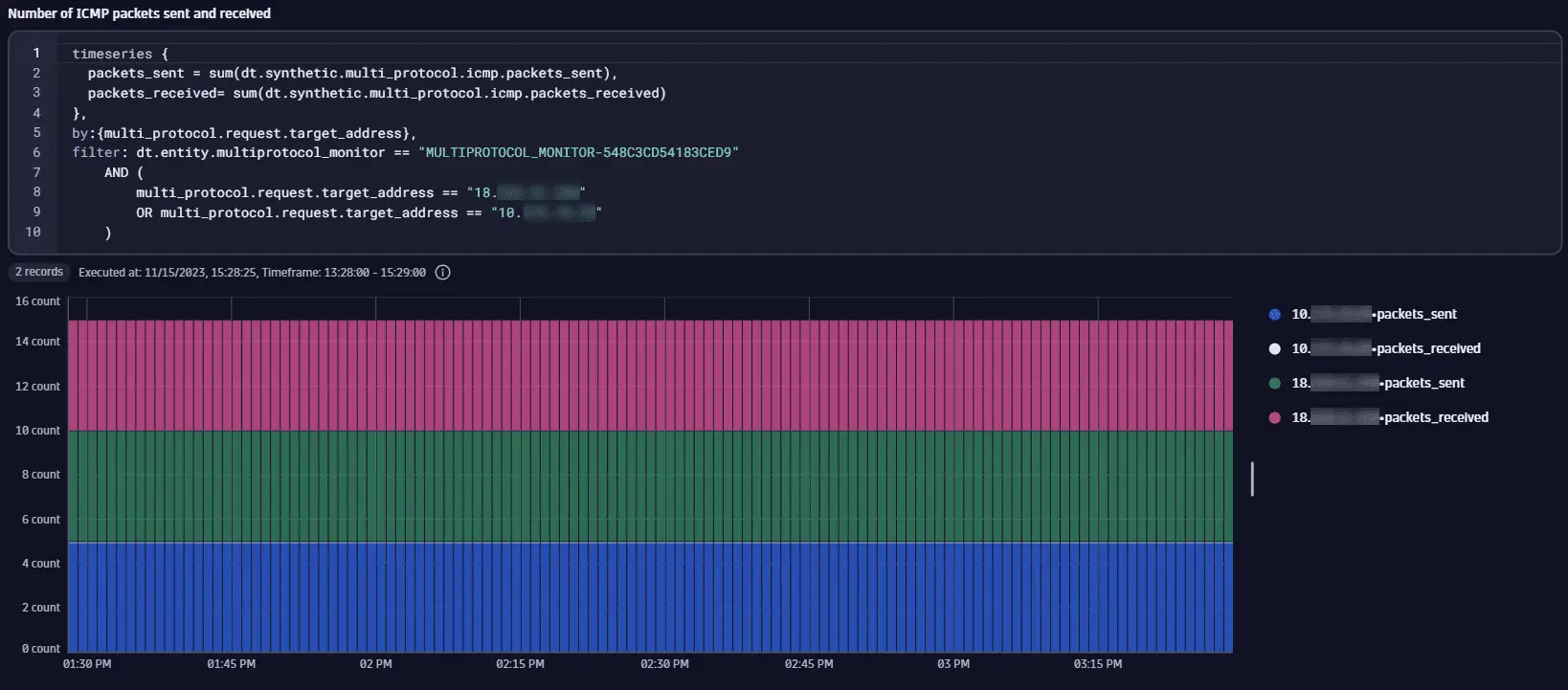
The monitor MULTIPROTOCOL_MONITOR-548C3CD54183CED9 executes ICMP requests to hosts with the explicitly defined IP addresses, 18.x.x.x, 10.x.x.x, and 34.x.x.x. Each of these IP addresses maps to a distinct host. We use the sum of the dt.synthetic.multi_protocol.icmp.packets_sent and the sum of the dt.synthetic.multi_protocol.icmp.packets_received metrics to get insight into how many packets were sent and received. We split results by the multi_protocol.request.target_address dimension and filter data for 18.x.x.x and 10.x.x.x only. For 18.x.x.x, the same number of packets were received as were sent, but for 10.x.x.x, all packets are lost and none were received.
timeseries {packets_sent = sum(dt.synthetic.multi_protocol.icmp.packets_sent),packets_received= sum(dt.synthetic.multi_protocol.icmp.packets_received)},by:{multi_protocol.request.target_address},filter: dt.entity.multiprotocol_monitor == "MULTIPROTOCOL_MONITOR-548C3CD54183CED9"AND (multi_protocol.request.target_address == "18.x.x.x"OR multi_protocol.request.target_address == "10.x.x.x")
Target status for TCP requests
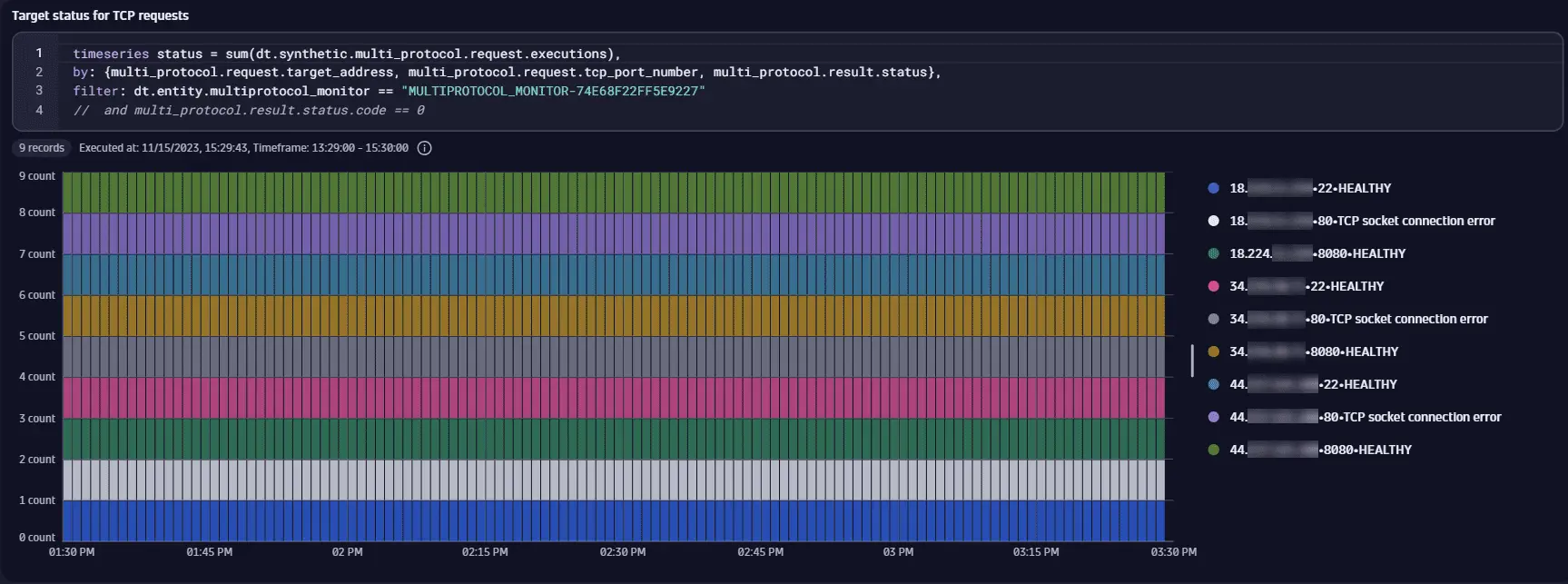
The monitor MULTIPROTOCOL_MONITOR-74E68F22FF5E9227 executes TCP requests to hosts from a host group that resolves to the IP addresses 18.x.x.x, 34.x.x.x, and 44.x.x.x. By using the dt.synthetic.multi_protocol.request.executions metric and splitting it by the multi_protocol.request.target_address, multi_protocol.request.tcp_port_number, and multi_protocol.result.status dimensions, we can display the status of the TCP connection for an IP-port pair. Each host has the ports 22 (SSH) and 8080 (HTTP server) open, and each connection to the hosts on these ports succeeds with the HEALTHY status. No service uses the standard HTTP port 80. Therefore, connections to all hosts on that port fail with the TCP socket connection error status. Note that results of this query can be limited to just successful requests by filtering by the multi_protocol.result.status.code dimension (code == 0).
timeseries status = sum(dt.synthetic.multi_protocol.request.executions),by: {multi_protocol.request.target_address, multi_protocol.request.tcp_port_number, multi_protocol.result.status},filter: dt.entity.multiprotocol_monitor == "MULTIPROTOCOL_MONITOR-74E68F22FF5E9227"// and multi_protocol.result.status.code == 0
TCP connection time to target port
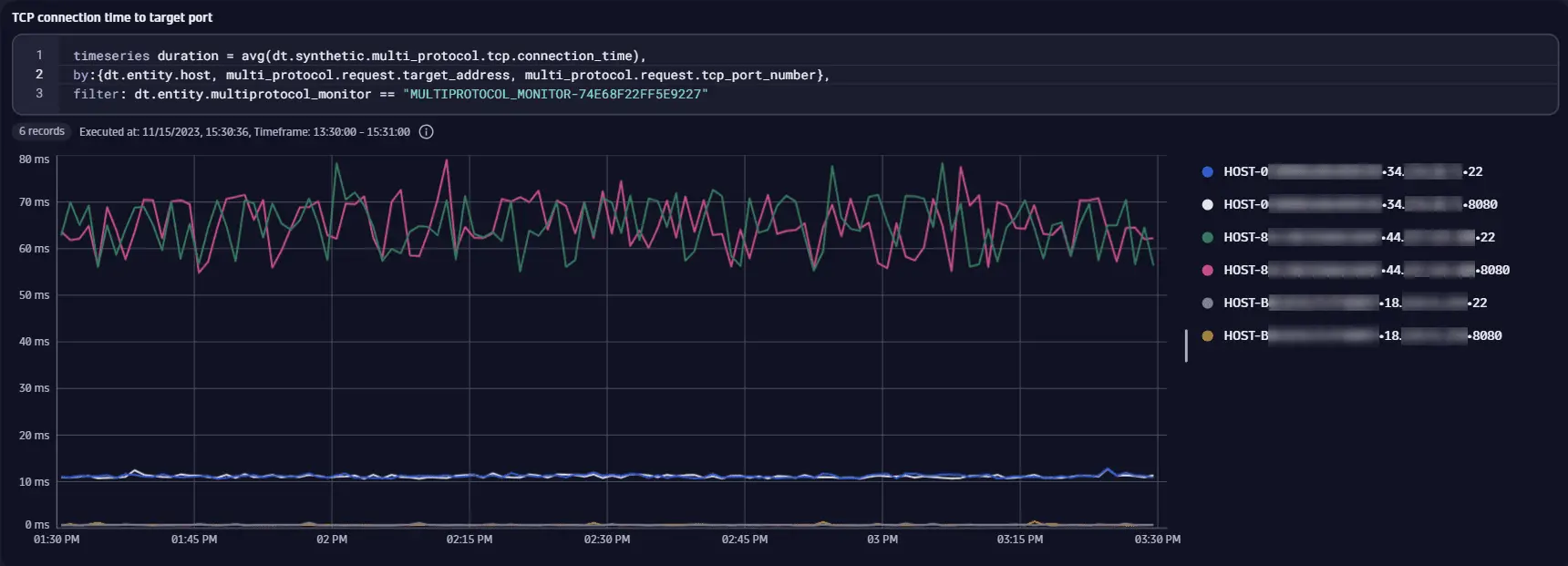
The monitor MULTIPROTOCOL_MONITOR-74E68F22FF5E9227 executes TCP requests to hosts from a host group that resolves to the IP addresses 18.x.x.x, 34.x.x.x, and 44.x.x.x. In this example, instead of IP addresses, we split the results by monitored host entity IDs. We use average of the dt.synthetic.multi_protocol.tcp.connection_time metric split by the dt.entity.host, multi_protocol.request.target_address, and multi_protocol.request.tcp_port_number dimensions to check typical time taken for a successful connection to the target port for a host. Only ports 22 (SSH) and 8080 (HTTP server) are open, and these are the only ports for which dt.synthetic.multi_protocol.tcp.connection_time is available. The hosts are effectively in different geographical locations (Ohio, Oregon, and North Virginia in the United States), a difference in connection times is expected.
timeseries duration = avg(dt.synthetic.multi_protocol.tcp.connection_time),by:{dt.entity.host, multi_protocol.request.target_address, multi_protocol.request.tcp_port_number},filter: dt.entity.multiprotocol_monitor == "MULTIPROTOCOL_MONITOR-74E68F22FF5E9227"