Identity management concepts
- Latest Dynatrace
- Explanation
- 6-min read
There are two types of identities within Dynatrace SaaS IAM: users and service users.
Users
Users in Dynatrace SaaS IAM are global entities uniquely identified through their email addresses. They can be invited into one or more Dynatrace accounts and can be non-federated (local) or federated.
- For non-federated users, Dynatrace’s Identity Provider (IdP) serves as the central user repository and is directly responsible for handling their authentication requests into the platform.
- For federated users, Dynatrace IdP entrusts authentication requests to their SAML-configured IdP. For more information, see User management.
Service users
Service users are non-human identities that are meant to be used by applications, services, or automated processes to interact with other services and resources.
- Service users are created by the account administrator and granted the necessary permissions to be able to access parts of the platform resources and data.
- Account administrators can leverage access policies to optionally grant an existing group the ability to use service users.
- Members of that group can then utilize the assigned service user to configure an automated workflow to trigger a process.
- Service users have the advantage of not being tied to a particular human user and, as such, are not subject to normal user lifecycle events, thus ensuring any processes using them will not be affected. Account administrators can always delete the service user or revoke the group permissions.
- Administrators can grant service users specifically tailored permissions that are limited to their operational needs, thus minimizing security risks. For more information, see Service users.
Identity federation
Identity federation is a process that allows users to access multiple systems or applications using a single set of credentials via a central identity provider(IdP) in your organization. This approach enables single sign-on (SSO) across different domains and organizations, enhancing user convenience and security.
Dynatrace SaaS supports SAML integration to allow you to delegate authentication requests to your enterprise IdP.
- Both service provider (SP) and IdP-initiated logins are supported.
- Admins can also invite non-federated users to their Dynatrace accounts, even if they have enabled federation for their enterprise users. The following flow diagram captures how authentication requests from federated and non-federated users are routed.
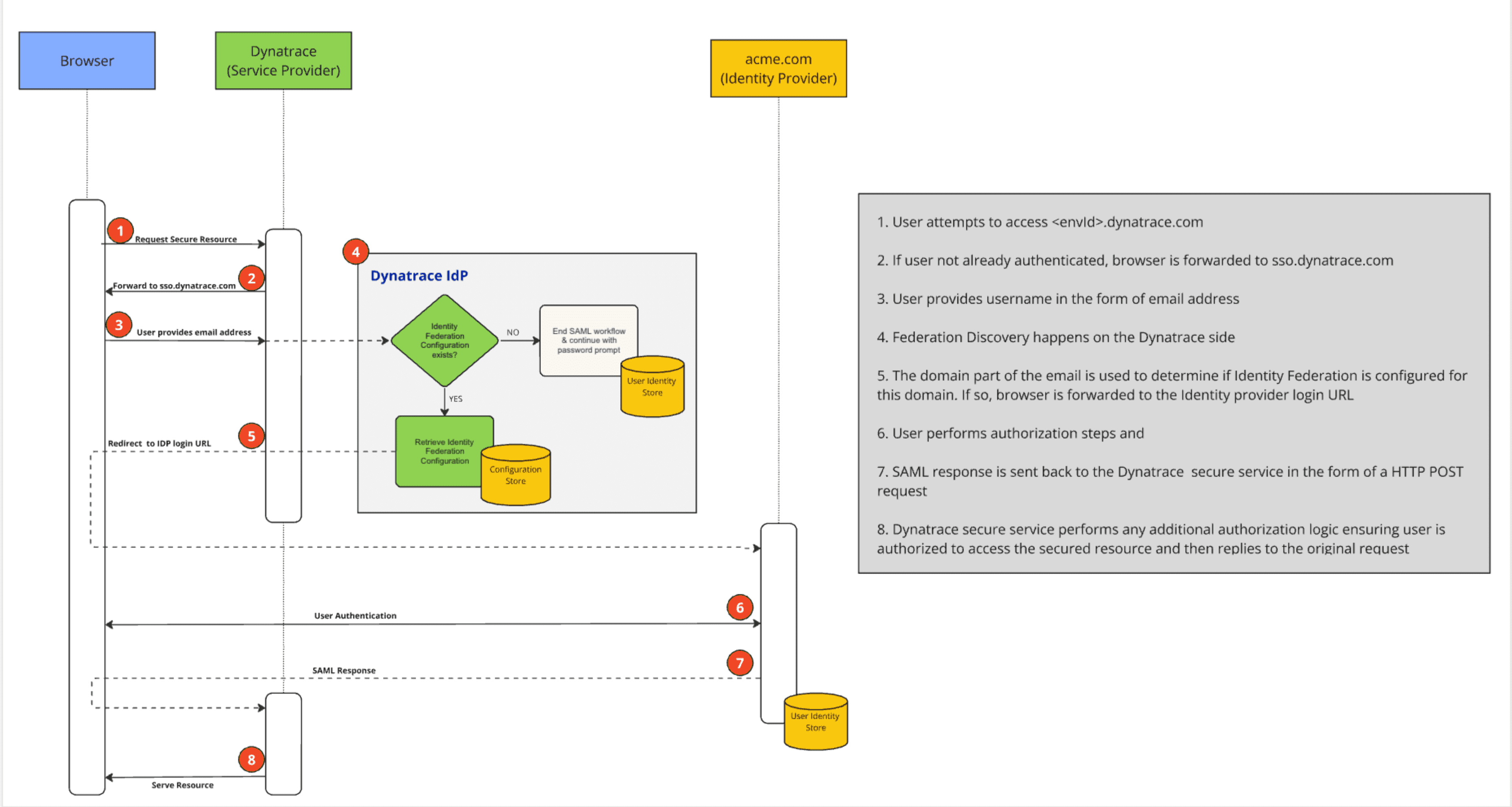
Configuration
Admins can configure SAML integration at three levels:
- Environment: Authentication requests are forwarded to the configured IdP whenever users attempt to access the specified environments.
- Account: Authentication requests are forwarded to the configured IdP independent of the environment being accessed within that account.
- Global: Authentication requests are forwarded to the configured IdP independent of the environment being accessed.
Note that configuring identity federation requires that you verify the ownership of your domain to avoid any misuse. Dynatrace SSO services implement the following Federation Configuration Discovery flow to determine which configuration applies to a given user.
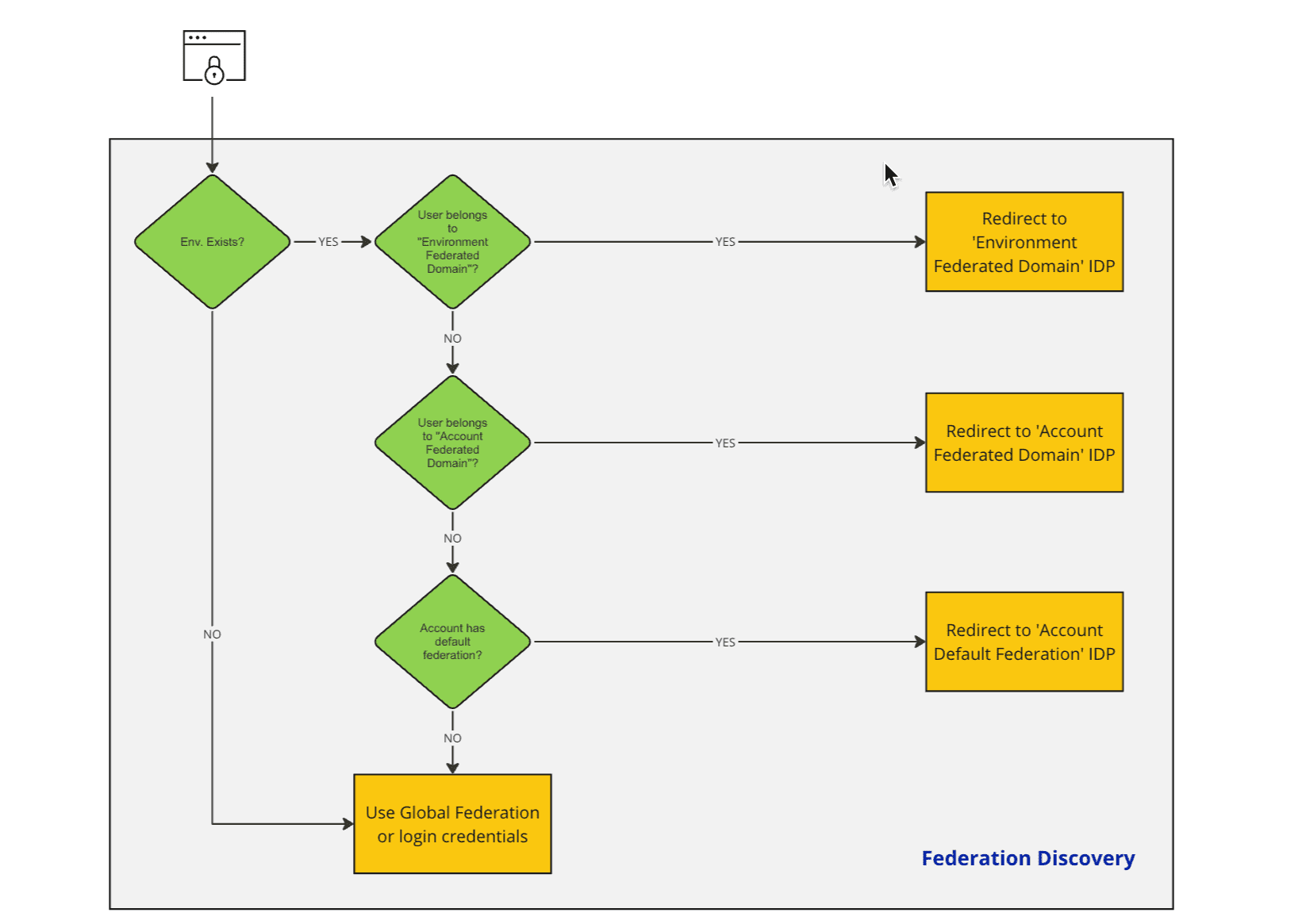
For more information, see SAML, SCIM, and Sign in with Microsoft in Dynatrace SaaS SSO.