Migrate OpenPipeline configurations to Settings API
- Latest Dynatrace
- How-to guide
- 3-min read
OpenPipeline configuration with Settings API facilitates configuration management on a larger scale. This is achieved through a fine-grained approach to permissions. It introduces a hierarchical split of configurations for enterprises with many teams, giving teams flexibility in ingesting and processing data according to their needs while maintaining adaptable control by monitoring and SRE teams.
This migration is a permanent change and cannot be undone. It introduces breaking changes to your policies and API integrations.
Why migrate
With configuration via Settings API, you get:
-
Separate objects for each pipeline and ingest source, and a single object for the configuration scope routing
Instead of a complex and large JSON file, Dynatrace Configuration as Code users can now focus on files specific to a pipeline, an ingest source, or the configuration scope routing, and distribute them in their repositories.
-
Fine-grained permissions
Administrators can create separate policies for each pipeline, each ingest source, and the configuration scope routing, providing flexibility for teams responsible for data ingestion and processing, as well as restricted routing management.
-
Owner-based access control for each pipeline and ingest source
Users can create, delete, and share access to pipelines and ingest sources they own.
What's in scope of the migration?
New API
The OpenPipeline Configurations API is replaced by the Settings API and the schemas for each configuration scope
- Routing (
builtin:openpipeline.<configuration.scope>.routing) - Pipelines (
builtin:openpipeline.<configuration.scope>.pipelines) - Ingest sources (
builtin:openpipeline.<configuration.scope>.ingest-sources)
The content of the top level keys remains unchanged, except for Davis events, which are now extracted in a separate stage. The migration affects endpoint URLs, query parameters, and the response/request body parameters structure, as well as the scope of the token for the request.
Base URL
| new Settings 2.0 | old OpenPipeline Configurations API |
|---|---|
/api/v2/settings | /api/platform/openpipeline/v1/configurations |
Authentication token scope
| new Settings 2.0 | old OpenPipeline Configurations API |
|---|---|
Read settings (settings.read)Write settings ( settings.write) | Read configuration (openpipeline:configurations:read)Write configuration ( openpipeline:configurations:write) |
Parameters
In the Settings 2.0 framework, routing for each configuration scope, individual pipelines, and individual ingest sources of your OpenPipeline configuration are represented by a settings object. An object contains some metadata (like the scope or creation timestamp) and its configuration, encapsulated in the value object. To view the parameters of routing, pipelines, and ingest sources, you can query the related schema with a GET request. To learn about new query/body parameters, see the documentation of individual requests.
Show me the documentation
- builtin:openpipeline.bizevents.ingest-sources
- builtin:openpipeline.bizevents.pipelines
- builtin:openpipeline.bizevents.routing
- builtin:openpipeline.davis.events.ingest-sources
- builtin:openpipeline.davis.events.pipelines
- builtin:openpipeline.davis.events.routing
- builtin:openpipeline.davis.problems.ingest-sources
- builtin:openpipeline.davis.problems.pipelines
- builtin:openpipeline.davis.problems.routing
- builtin:openpipeline.events.ingest-sources
- builtin:openpipeline.events.pipelines
- builtin:openpipeline.events.routing
- builtin:openpipeline.events.sdlc.ingest-sources
- builtin:openpipeline.events.sdlc.pipelines
- builtin:openpipeline.events.sdlc.routing
- builtin:openpipeline.events.security.ingest-sources
- builtin:openpipeline.events.security.pipelines
- builtin:openpipeline.events.security.routing
- builtin:openpipeline.logs.ingest-sources
- builtin:openpipeline.logs.pipelines
- builtin:openpipeline.logs.routing
- builtin:openpipeline.metrics.ingest-sources
- builtin:openpipeline.metrics.pipelines
- builtin:openpipeline.metrics.routing
- builtin:openpipeline.security.events.ingest-sources
- builtin:openpipeline.security.events.pipelines
- builtin:openpipeline.security.events.routing
- builtin:openpipeline.spans.ingest-sources
- builtin:openpipeline.spans.pipelines
- builtin:openpipeline.spans.routing
- builtin:openpipeline.system.events.ingest-sources
- builtin:openpipeline.system.events.pipelines
- builtin:openpipeline.system.events.routing
- builtin:openpipeline.user.events.ingest-sources
- builtin:openpipeline.user.events.pipelines
- builtin:openpipeline.user.events.routing
- builtin:openpipeline.user.sessions.ingest-sources
- builtin:openpipeline.user.sessions.pipelines
- builtin:openpipeline.user.sessions.routing
New permissions
The new Settings API has dedicated permissions for routing, pipelines, and ingest sources. They substitute the previous permissions as described in the table below.
| new Settings 2.0 | old OpenPipeline Configurations API |
|---|---|
settings:objects:read | openpipeline:configurations:read |
settings:objects:write | openpipeline:configurations:write |
Owner-based access control
Pipelines and ingest source have owners and accessors.
- Owner
The first user to store the object. Owners have read and write access to the objects they create and can delete it or share it with other users. It can be set to all users or a single user.
- Accessor
One or multiple users who can access an object shared by an owner. It can be set to all users, a single user, or multiple users.
Administrators have unlimited read and write access to all objects. Additionally, they can share access to objects and change the owner.
Therefore a pipeline or ingest source can be accessed by a user that is one of the following:
- Administrator (
settings:objects:admin) - The owner of the object
- An accessor of the object with sufficient permissions (
settings:objects:readorsettings:objects:write)
Owner-based control is not availalble for routing. Routing management is restricted to administrators (settings:objects:admin). Administrators can grant write access to a configuration scope routing via policies.
To learn more, see Owner-based access control in OpenPipeline.
What's not in scope of the migration
The migration won't affect
- Other OpenPipeline API endpoints and their permissions
- The OpenPipeline Preview API, Matcher API, Processor API, and Technology API remain unchanged.
- The existing permissions (
openpipeline:configurations:read) remain valid for the above endpoints.
- OpenPipeline Ingest API
How to migrate
Before you migrate
 Breaking change
Breaking change
- You must update policies and integrations based on the OpenPipeline Configurations API.
- If you are using Dynatrace Configuration as Code, you must download the new configuration immediately after the migration.
We recommend that you back up your existing configuration before starting the migration.
Prerequisites
-
When you go to
 Settings > Process and contextualize > OpenPipeline and select any configuration scope, you see the migration banner.
Settings > Process and contextualize > OpenPipeline and select any configuration scope, you see the migration banner.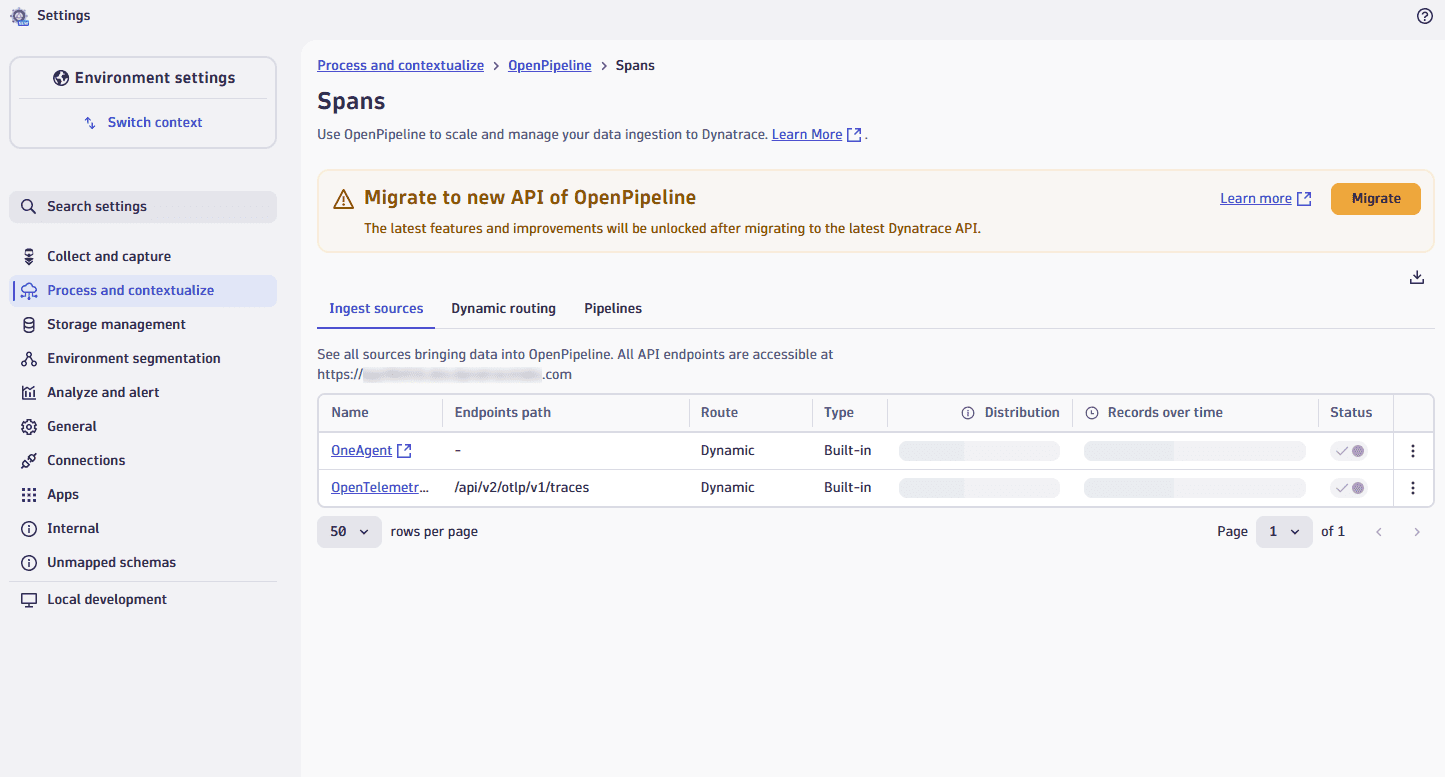
If you don't see the migration banner, your environment might have already been migrated or will be migrated soon. If your environment has already been migrated, ingest sources and pipelines have a new Owners column. If you don't see either, check again in the upcoming days.
-
You have the following permissions:
openpipeline:configurations:writeandsettings:objects:admin. -
For Terraform users, make sure to use Dynatrace Terraform version 1.85+.
Steps
1. Adapt policies and permissions
By default, after the migration all users have settings:objects:read (read access) and become owners of all pipelines and ingest sources. However, to enable owners to modify existing pipelines or users to create new pipelines, you must grant settings:objects:write (write access).
-
Go to Account Management > Identity and Access Management
-
Create new policies to grant
settings:objects:write(write access) to specific users.Show me policy examples
-
Example 1: Grant write permission to a single object of a configuration scope
The following policy grants write permission only to the pipeline object for the logs configuration scope. Users listed in the policy can modify the log pipelines if they own or have been granted edit access.
ALLOW settings:objects:write WHERE settings:schemaId = "builtin:openpipeline.logs.pipelines" -
Example 2: Grant write permission to multiple objects of multiple configuration scopes
The following policy grants write permission to the pipeline and ingest source objects for both the user event and span configuration scopes. Users listed in the policy can modify the user event and span ingest sources and pipelines if they own or have been granted edit access.
ALLOW settings:objects:write WHERE settings:schemaId IN ("builtin:openpipeline.user.events.pipelines", "builtin:openpipeline.user.events.ingest-sources", "builtin:openpipeline.spans.pipelines", "builtin:openpipeline.spans.ingest-sources") -
Example 3: Grant write permission to all objects of a single configuration scope
The following policy grants write permission to the pipeline, ingest source, and the configuration scope routing objects for business events. Users listed in the policy can modify the business event routes and, if they own or have been granted edit access, also the ingest sources and pipelines.
Use with cautionThis policy gives users write permissions to all routes for a configuration scope and should therefore be used with caution.
ALLOW settings:objects:write WHERE settings:schemaId startsWith "builtin:openpipeline.bizevents" -
Example 4: Grant write permission to all pipelines and ingest sources.
The following policy grants write permission to all pipeline and ingest source objects of all configuration scopes. Users listed in the policy can modify ingest sources and pipelines if they own or have been granted edit access.
ALLOW settings:objects:write WHERE settings:schemaGroup IN ("group:openpipeline.all.pipelines");ALLOW settings:objects:write WHERE settings:schemaGroup IN ("group:openpipeline.all.ingest-sources")
-
2. Adapt API integrations
Review the integrations that use the OpenPipeline Configurations API endpoints, such as API calls, scripts, configurations-as-code files, or third-party integrations. Make sure to use the new Settings API schemas instead.
3. Migrate to the new format
To migrate your OpenPipeline configuration to the new API
-
Go to
 Settings > Process and contextualize > OpenPipeline and select any configuration scope.
Settings > Process and contextualize > OpenPipeline and select any configuration scope.This process will migrate all configuration scopes, regardless of which one you select.
-
In the upper part of the configuration scope page, select Migrate in the dedicated banner.
The migration process will start automatically. It will take a few minutes to complete.
When the migration completes successfully, a Migration successful message appears. Configurations for all configuration scopes have been migrated to the new API.
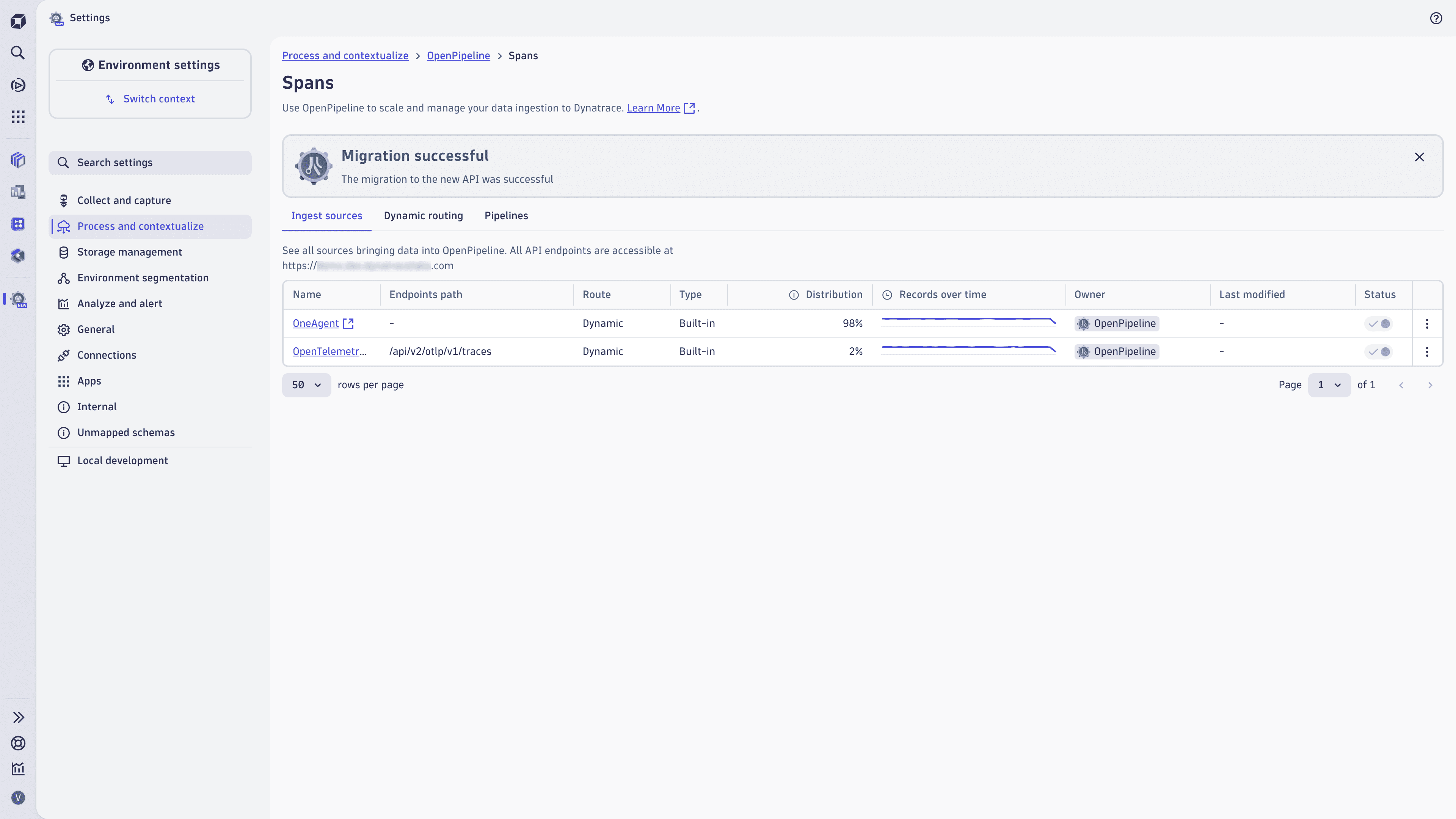
The following endpoints can no longer be used:
-
GET /platform/openpipeline/v1/configurations -
GET /platform/openpipeline/v1/configurations/{id} -
PUT /platform/openpipeline/v1/configurations/{id}
-
If you are not using configuration as code, your migration is completed.
4. Adapt DQL queries for Davis event extraction
The Davis event processor is now part of a separate stage, Davis, and is no longer part of the Data extraction stage. If you are using the Davis event processor, make sure to adapt your DQL queries.
5. Download the configuration-as-code files
Dynatrace has migrated the OpenPipeline Configurations API to the Settings API schema automatically for you, therefore you don't need to manually look into the configuration files.
To complete the migration,
-
Download and create new configuration-as-code files containing the new configuration.
- Via Dynatrace Terraform provider, use the
exportutility. - Via Dynatrace Monaco CLI, use the
downloadcommand. To learn more about how Settings 2.0 objects are handled, see Monaco configuration YAML file - list of special configuration types
- Via Dynatrace Terraform provider, use the
-
Modify all necessary configuration files containing the old schema ID with the new schema ID.
-
Delete the old configurations files.
What to do after the migration?
-
Set access control in OpenPipeline to start handing over the configuration responsibility for pipelines to the individual teams who own the data.
-
Preview You can enroll in the Preview program with higher configuration limits, up to 2,000 pipelines. To enroll in the program, contact a Dynatrace product expert via live chat.