Prioritize vulnerabilities
In the following, you'll learn to prioritize third-party, code-level, and runtime vulnerabilities based on
Prioritize by Davis Security Score
Third-party vulnerabilities
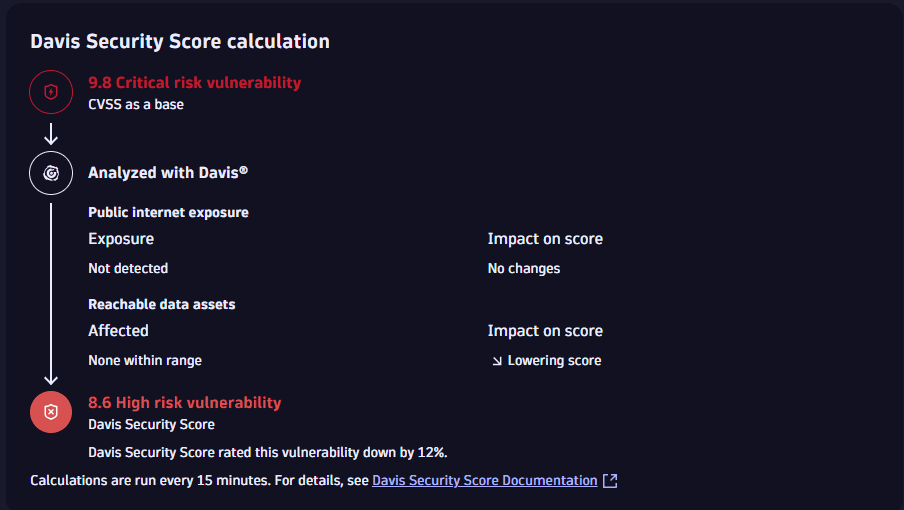
The severity of a vulnerability is calculated based on Davis Security Score (DSS), so you can focus on fixing vulnerabilities that are relevant in your environment, instead of on those that have only a theoretical impact.
You can
Filter by DSS
To filter vulnerabilities based on their Davis Security Score (DSS)
- On the Prioritization page, in the filter bar, select Risk level.
- Select the severity you're interested in.
Get details about DSS calculation
To see details about the DSS calculation process
- On the Prioritization page, select a vulnerability title.
- On the details page of the vulnerability, look for Davis Security Score calculation.
FAQ
Further reading
To learn more about DSS, see Concepts: Davis Security Score.
Prioritize by risk factors
You can prioritize vulnerabilities by analyzing the associated risk factors.
You can
-
Get details about vulnerable functions Third-party vulnerabilities
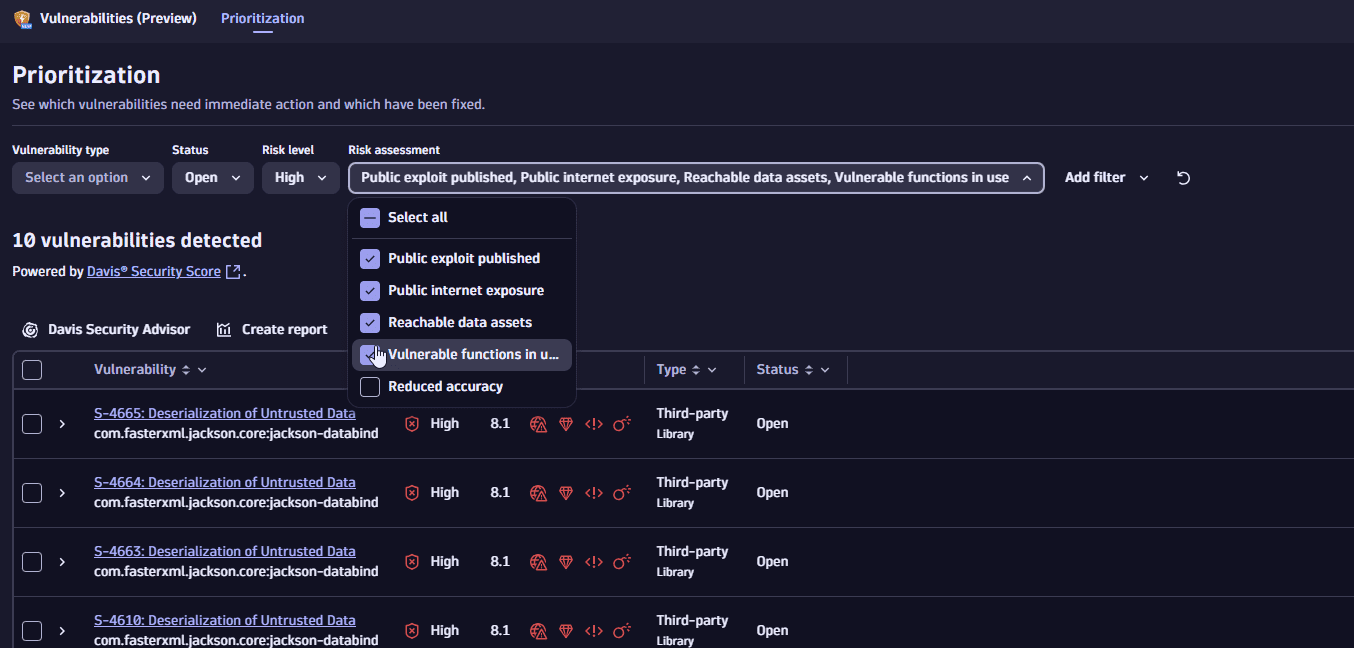
Filter by risk factors
- On the Prioritization page, in the filter bar, select Risk assessment.
- Select the options you're interested in.
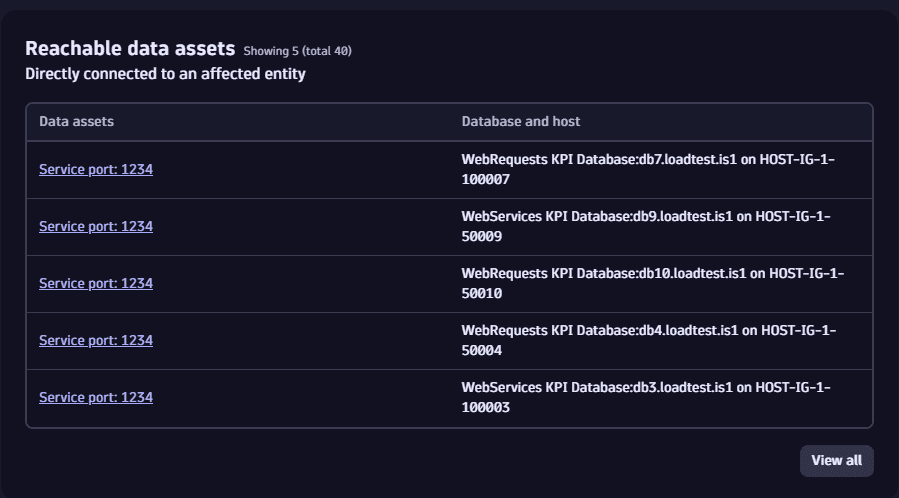
Get details about reachable data assets
In the Reachable data assets section you can
- Get information about the last five database services accessed by affected processes containing the identified vulnerability
- Track the reachable databases directly connected to a vulnerability
- On the Prioritization page, select a vulnerability title.
- On the details page of the vulnerability, look for Reachable data assets.
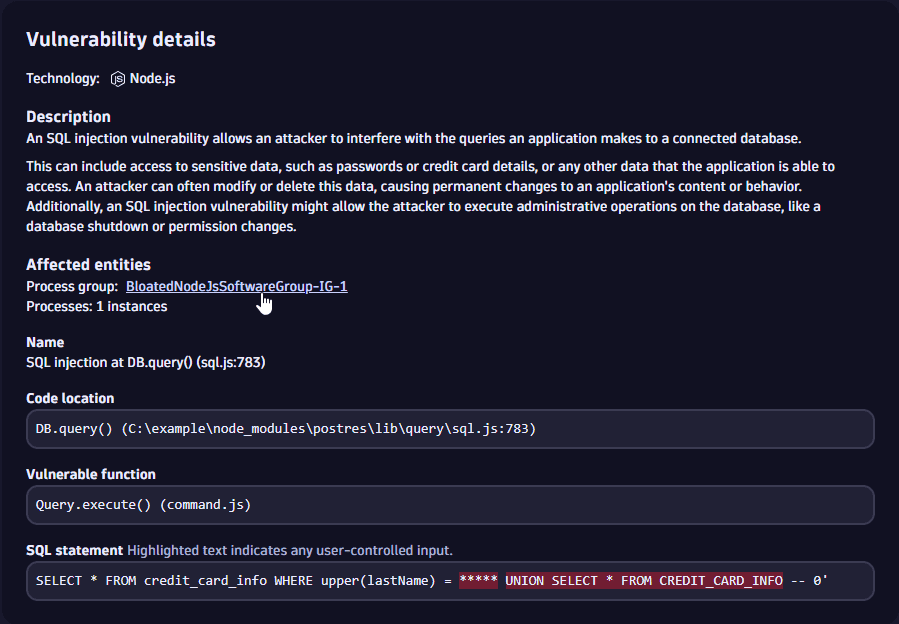
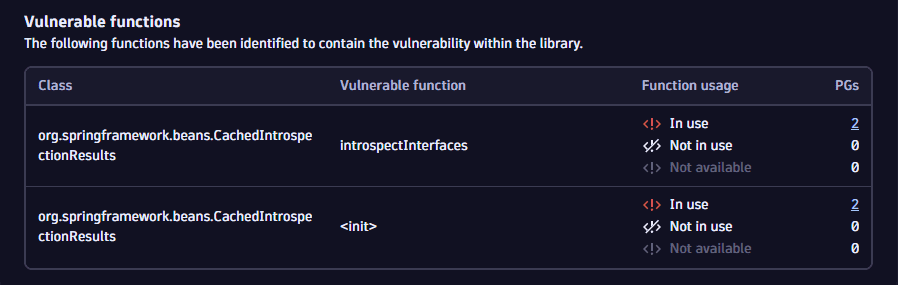
Get details about vulnerable functions
Third-party vulnerabilities
In the Vulnerable functions section you can
- Get information about the function and the class that contains the vulnerable function related to the vulnerability
- Check whether the vulnerable function is being used by your application
- On the Prioritization page, select a vulnerability title.
- On the details page of the vulnerability, look for Vulnerability details > Vulnerable functions.
Further reading
To learn more about the risk factors, see Concepts: Risk factors.
Prioritize by related and affected entities
To understand what is at risk, you can examine
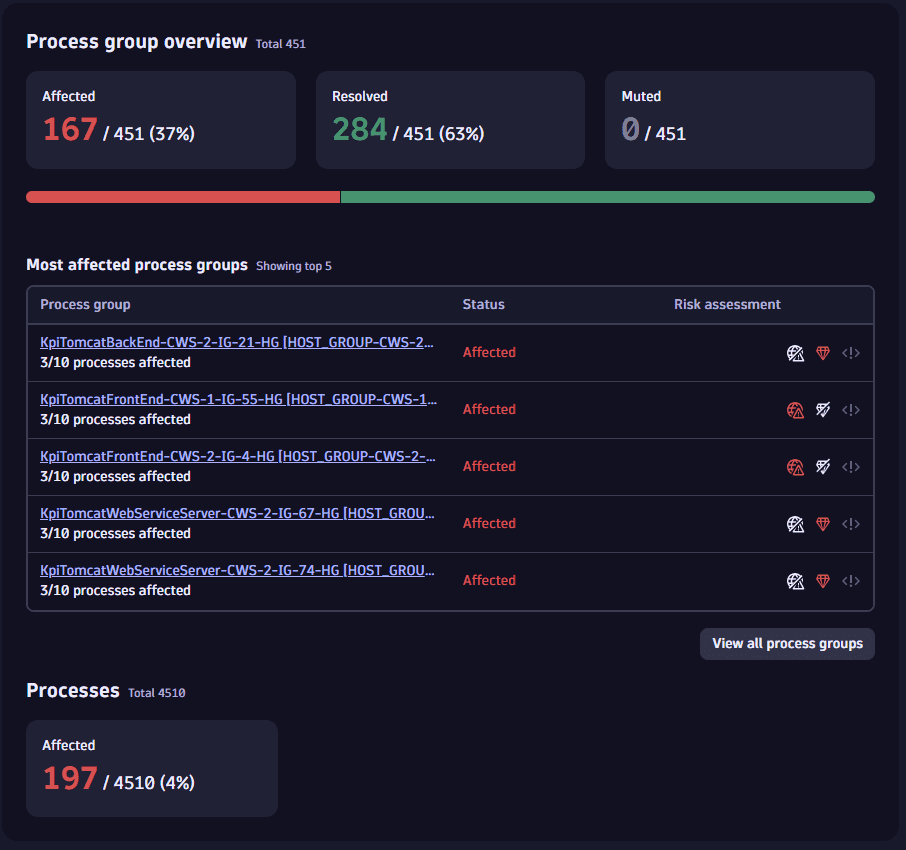
- The related and affected process groups
- For Kubernetes environments, the related and affected Kubernetes nodes Third-party vulnerabilities
- The related applications, services, hosts, databases, Kubernetes workloads and clusters
Examine related and affected process groups
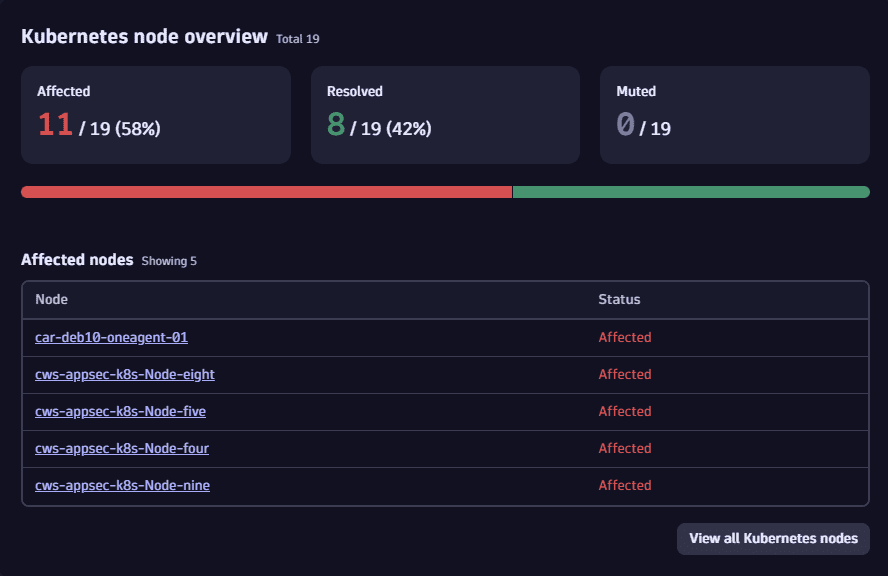
Examine related and affected Kubernetes nodes
Third-party vulnerabilities
For Kubernetes environments, in the Kubernetes node overview section, you can
- Track down how many Kubernetes nodes are affected by a vulnerability:
- The number of Kubernetes nodes and the percentage of affected Kubernetes nodes out of the total number of Kubernetes nodes (
Affected,Resolved, andMuted). The number of affected Kubernetes nodes matches the total count only if all functions in all used software component versions are vulnerable. - The number of affected Kubernetes nodes that have been resolved by fixing the vulnerable libraries and the percentage of resolved Kubernetes nodes out of the total number of related Kubernetes nodes.
- The number of affected Kubernetes nodes that have been muted (silenced) and the percentage of muted Kubernetes nodes out of the total number of related Kubernetes nodes.
- The number of Kubernetes nodes and the percentage of affected Kubernetes nodes out of the total number of Kubernetes nodes (
- Evaluate Kubernetes nodes by their current status (
Affected, thenResolved, and thenMuted). - Access the overview page of related Kubernetes nodes where you can set tracking links and check the remediation progress for related Kubernetes nodes.
- On the Prioritization page, select a vulnerability title.
- On the details page of the vulnerability, look for Kubernetes node overview.
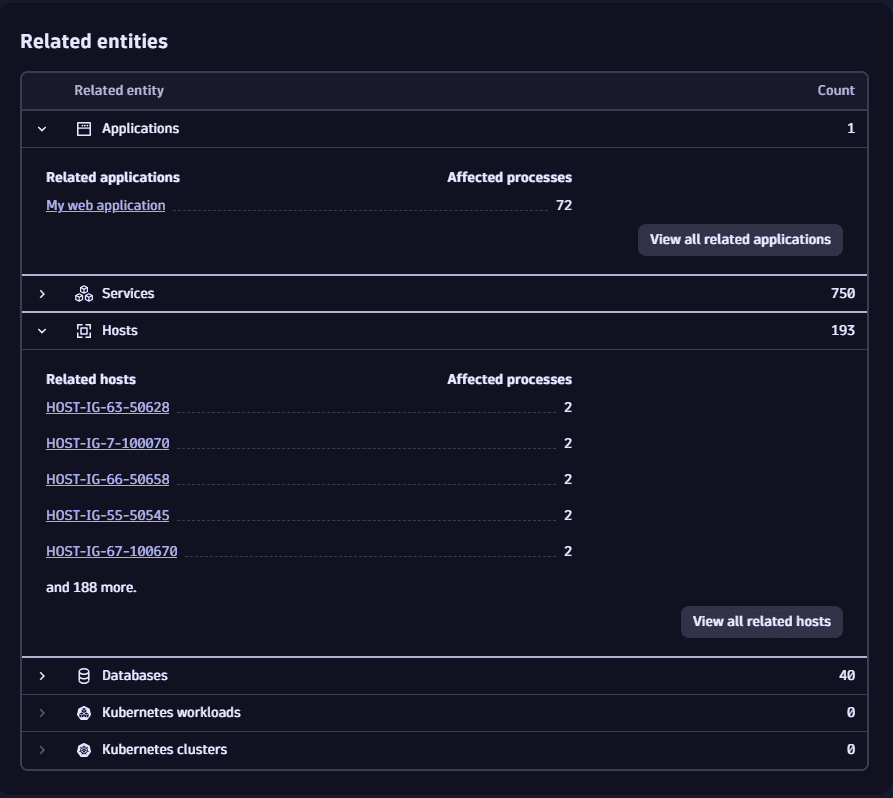
Examine other related entities
In the Related entities section, you can examine and track down entities (other than process groups and Kubernetes nodes) that are connected to one of the affected entities, thus indirectly affected by the vulnerability.
-
On the Prioritization page, select a vulnerability title.
-
On the details page of the vulnerability, look for Related entities.
-
Expand a row and select
- A related entity, to open it in another compatible app for further insights.
- View all related (…), to navigate to the overview page of the related entities.
Rows are expandable for the sections counting at least one related entity.
Further reading
To learn more about affected and related entities, see Concepts: Affected and related entities.
Prioritize by vulnerability evolution
In the Vulnerability evolution section, you can better understand the historical context and evolution of a vulnerability over time based on current status and the latest events.
For example, in case a vulnerability increases in severity, it's good to know when and why the increase happened: Given that a vulnerability with Medium severity, which is not on your "immediately to fix" radar, suddenly becomes Critical, it's helpful to know that you didn't overlook a Critical vulnerability for a long time, but the vulnerability was Medium before and now has become a priority.
Without history, you only have the current criticality and know how long it has been open. That could lead to questions when a Critical vulnerability seems to have been open for one week.
- On the Prioritization page, select a vulnerability title.
- On the details page of the vulnerability, look for Vulnerability evolution.
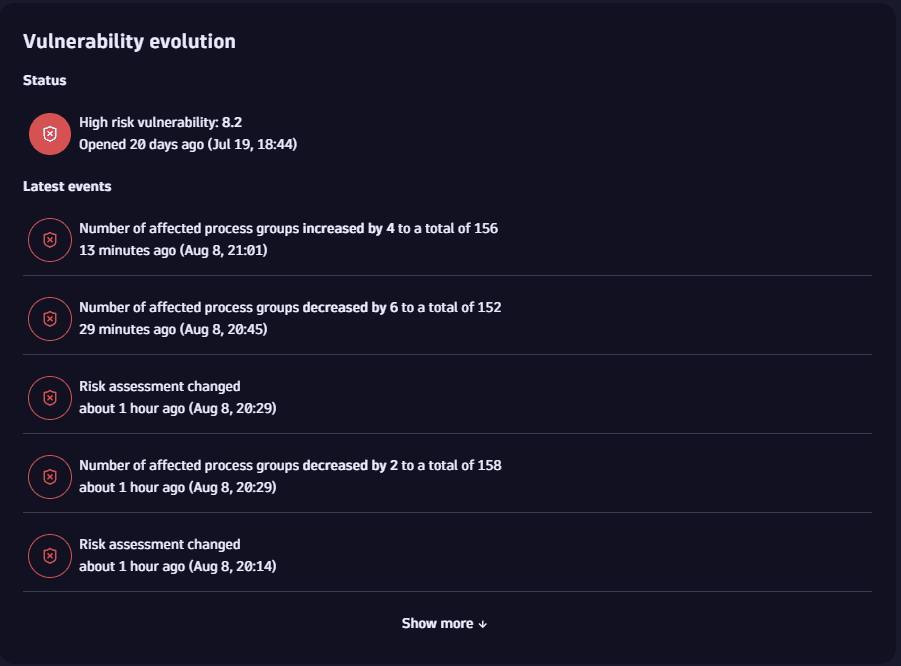
Events are stored for one year and can only be queried up to the timestamp of when the vulnerability was first detected.