Microsoft 365 Connector
- Latest Dynatrace
- 6-min read
You can automate sending out-of-the-box emails using Microsoft 365 Connector  based on the events and schedules defined by your workflows.
based on the events and schedules defined by your workflows.
Set up
1. Allow External Requests
External requests enable outbound network connections from your Dynatrace environment to external services. They allow you to control access to public endpoints from the AppEngine with app functions and functions in Dashboards, Notebooks, and Automations.
-
Go to
 Settings > General > External requests.
Settings > General > External requests. -
Select New host pattern.
-
Add the domain names.
-
Select Add.
This way you can granularly control the web services your functions can connect to.
You need to add these domain names login.microsoftonline.com and graph.microsoft.com.
2. Grant permissions to Workflows
Workflows requires some permissions to run actions on your behalf. Actions that come bundled with the Connector require other permissions.
To fine-tune permissions granted to Workflows
- Go to Workflows
 and go to Settings > Authorization settings.
and go to Settings > Authorization settings. - Select the following permissions besides the general Workflows permission.
app-settings:objects:read
For more on general Workflows user permissions, see User permissions for workflows.
3. Set up integration with Dynatrace
Configure your Microsoft Azure tenant to establish a connection with your Dynatrace environment.
-
Open
portal.azure.comto access your Microsoft Azure tenant and navigate toApp registrationsto set up a new app. For the necessary setup steps, see Register a client application in Microsoft Entra ID in Microsoft Azure documentation. -
Grant your newly created Azure app the
Microsoft Graph/Mail/Mail.Sendpermission.For more information, see API permissions and Introduction to permissions and consent in Microsoft Azure documentation.
To be able to use the API to send emails in the background without a currently signed-in user, you need to select Application permissions. Delegated permissions aren't sufficient.
-
After registering the app, create a new client secret. For details, see Certificates & secrets in Microsoft Azure documentation.
- To create a client secret, make sure that you either have admin permissions or are part of the app owners.
- Make sure you store the client secret Value (not the Secret ID) after creation for establishing the connection to your Dynatrace environment in the next section.
Limit mailbox access through an application access policyWe strongly recommend using a technical email address as the sender used by the Dynatrace Workflows action and limiting the permissions of your Microsoft Azure app registration to these specific mailboxes by setting up an application access policy. This ensures that only specified email addresses can be used in the app registration and eventually in Dynatrace Workflows. This helps to reduce risks from impersonation.
For details on how to set up a new application access policy, see Limiting application permissions to specific Exchange Online mailboxes in Microsoft Azure documentation.
If you don't set up an application access policy for your Microsoft Azure tenant and restrict the possible email senders, any email address of your tenant can be used as the sender for your emails sent via Dynatrace Workflows.
Application access policies can be assigned to users or groups. Microsoft supports groups as outlined in the section PolicyScopeGroupID.
The
fromemail address must be an online-hosted mailbox.
4. Authorize connection
Microsoft 365 Connector requires a client secret from Microsoft Azure for authorization.
- Get the following credentials from your app registration in your Microsoft Azure tenant on
portal.azure.com.- Directory (tenant) ID: Available on the Overview menu.
- Application (client) ID: Available on the Overview menu.
- Client secret: Is the Value (not the Secret ID) of the client secret from the preceding Set up Microsoft Azure for integration with Dynatrace section.
- Return to Dynatrace, go to Settings and select Connections > Connectors > Microsoft 365.
- Select
Connection and provide the following information.
- Connection name: Needs to be unique. Will be listed and selectable in the connection field in Microsoft 365 Connector.
- Directory (tenant) ID
- Application (client) ID
- "From" email address: See Limit mailbox access through application access policy in the Set up Microsoft Azure for integration with Dynatrace section.
- Type:
Client secret - Client Secret: This is the Value of the client secret from the Set up Microsoft Azure for integration with Dynatrace section.
- Select Create.
Additional notes
-
To add connection settings, you need the following permissions.
ALLOW settings:objects:read, settings:objects:write, settings:schemas:read WHERE settings:schemaId = "app:dynatrace.microsoft365.connector:connection"For details, see Permissions and access.
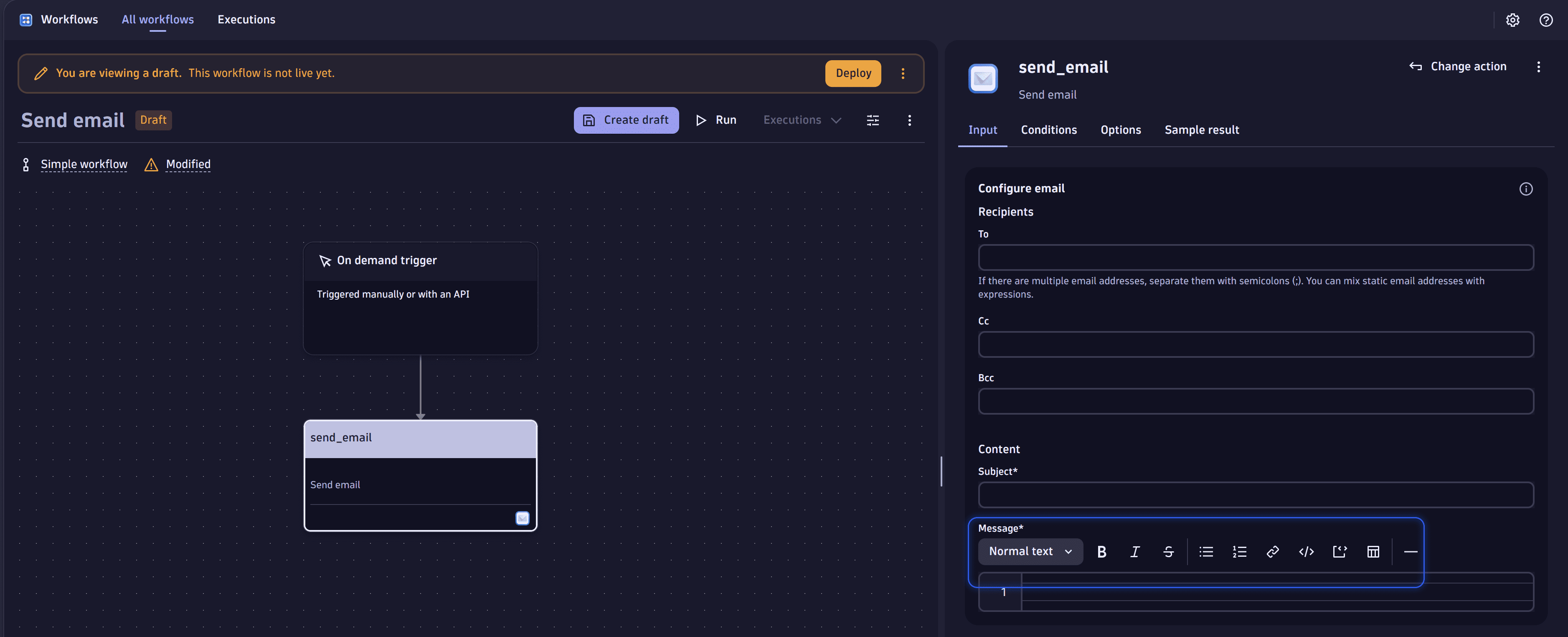
Send an email with workflows
-
Go to Workflows
 and select
and select to create a new workflow.
-
In the side panel, select the trigger best suited to your needs.
-
On the trigger node, select
to browse available actions.
-
In the side panel, search the actions for Microsoft 365 and select Send email.
-
Select a preconfigured Microsoft 365 connection.
-
Enter the email addresses for the recipients.
The number of email addresses is currently restricted to 10 per field.
-
Enter a subject.
-
Enter a message.
-
To test your workflow, select Run.
Format email
To format the body of an email
-
Select Message.
-
Enter your text.
When you select, for example, the bold style, your text is rendered as bold in the sent email. You won't be able to preview it without the formatting symbols. However, when you send an email, the recipient will see the properly formatted text, and the formatting symbols won't be visible.
You can use the toolbar to insert common elements like a heading, bold text, or a link.
Attaching an image or inserting JavaScript code into the email body is impossible. It's just shown as plain text.
Format syntax
Italics
Wrap text in single asterisks (*like this*) to get italics like this.
Bold
Wrap text in double asterisks (**like this**) to get bold text like this.
Strikethrough
Wrap text in double tildes (~~like this~~) to get strikethrough (crossed out) text like this.
Code
-
Wrap text in backticks (`like this`) to get bold text
like this. -
Wrap text in triple backticks (```like this```) to show a code block (multiple lines of
code text).
Headings
To add a heading, start the line with the # character like this: # This is your heading text.
Horizontal line
To visually separate sections of your annotation, add a horizontal line with three dashes (---):
Lists
Each line of an unordered (bulleted) list starts with an asterisk (*):
* Line 1* Line 2
Alternatively, you can use a dash (-):
- Line 1- Line 2
An ordered (numbered) list starts with a number and a period (1.) followed by a space and then your text:
1. The first line of my procedure.2. The second line of my procedure.3. The third line of my procedure.
Tables
To add a table, define the headers, the column formatting row, and then the rows of data you want to display
| Header 1 | Header2--- | ---content2 | content2
| Header 1 | Header2 |
|---|---|
| content2 | content2 |
Links
To link to a website, use this format:
[Example text label](https://www.example.com)
Here's a link to the [Dynatrace website](www.dynatrace.com).
When using markdown links in email messages, only certain protocols are supported and are transformed to HTML links:
httphttpsftpftpsmailtotelsms
Links using unsupported protocols (such as file://) aren't transformed from markdown to HTML links and remain plain text. Depending on your email client, these links might still be highlighted or rendered as clickable links by the client itself.
Line break
To add a single line break and a new line, select Enter in the Message field of the Connector.
This Connector only allows formatting of the message body using the listed formatting options. It doesn't offer support for HTML.
Email formatting is disabled for messages with a size greater than or equal to 1 MB.
Inputs
| Field | Description | Required |
|---|---|---|
| To | The recipients of the email. | Required |
| Cc | The cc recipients of the email. | Required |
| Bcc | The bcc recipients of the email. | Required |
| Subject | The subject of the email. | Required |
| Content | The content of the email. | Required |
You must enter at least one and a maximum of ten recipients in one of the fields (to, cc, bcc).
If you are using expressions for the recipients, the expressions must be evaluated as a list of email addresses, for example, ["user1@domain.com", "user2@domain.com"].
Action result
The Send email action provides the following result.
Sending JSON payloads as message content
When sending an object or non-string data as message content, ensure it is properly formatted as a string.
The recommended approach is to wrap your input in an expression and convert it to a JSON string using the to_json filter:
{{ result("run_javascript_1") | to_json }}
This approach ensures your data is properly formatted for transmission. For more information, see Expression reference.
Troubleshooting
The following are solutions to problems some people have.