CPU profiling
- How-to guide
- 2-min read
- Published Nov 22, 2018
Dynatrace offers the following capabilities that allow you to perform enhanced code-level CPU analysis:
- Gain insights into processes and process group hotspots
- Access background activity, service activity, single request executions, and specific requests
- Break down and filter data by code execution, network I/O, disk I/O, lock time, and wait times over times
- Break down and filter data by API over time
- View forward stack traces and hotspots with reverse stack traces
- Gain support for Java, .NET, PHP, Node.js, and Golang
To perform code-level CPU analysis:
- Go to
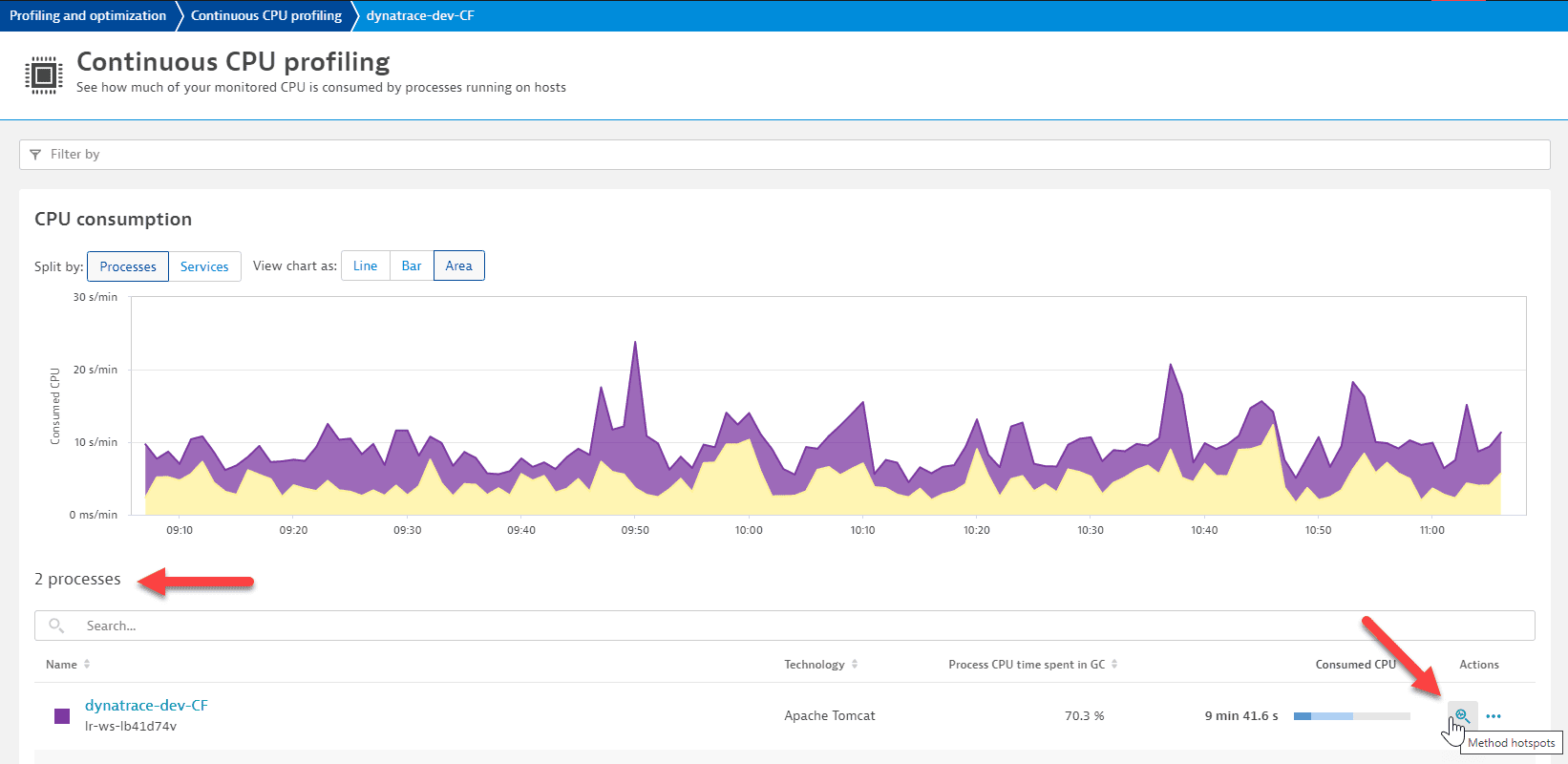
 Profiling & Optimization and select Continuous CPU profiling.
Profiling & Optimization and select Continuous CPU profiling. - Select the process group that contains the process that you want to analyze.
- Find the process you want to analyze and, in the Actions column, select the corresponding Method hotspots icon to view the Method hotspots page.
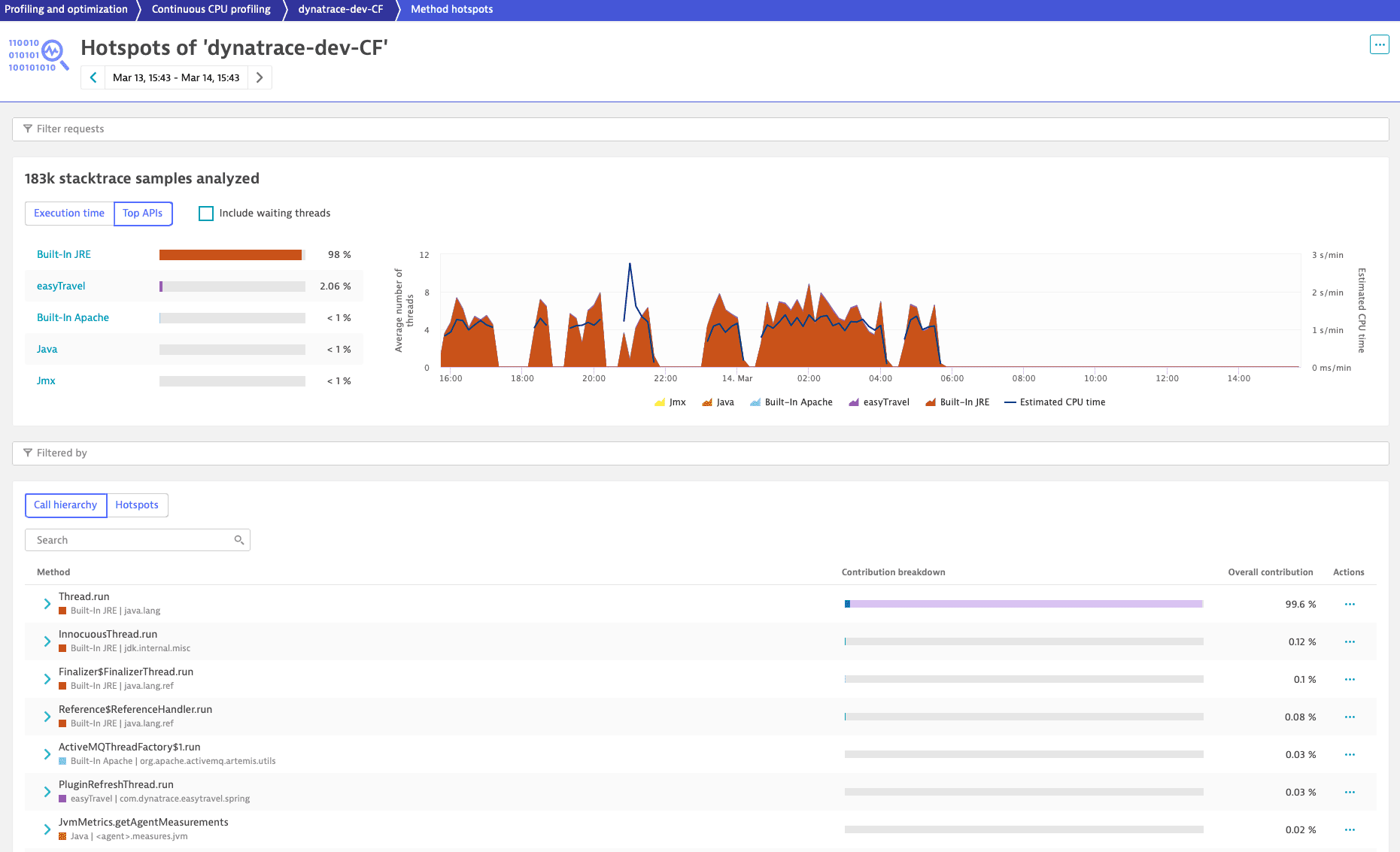
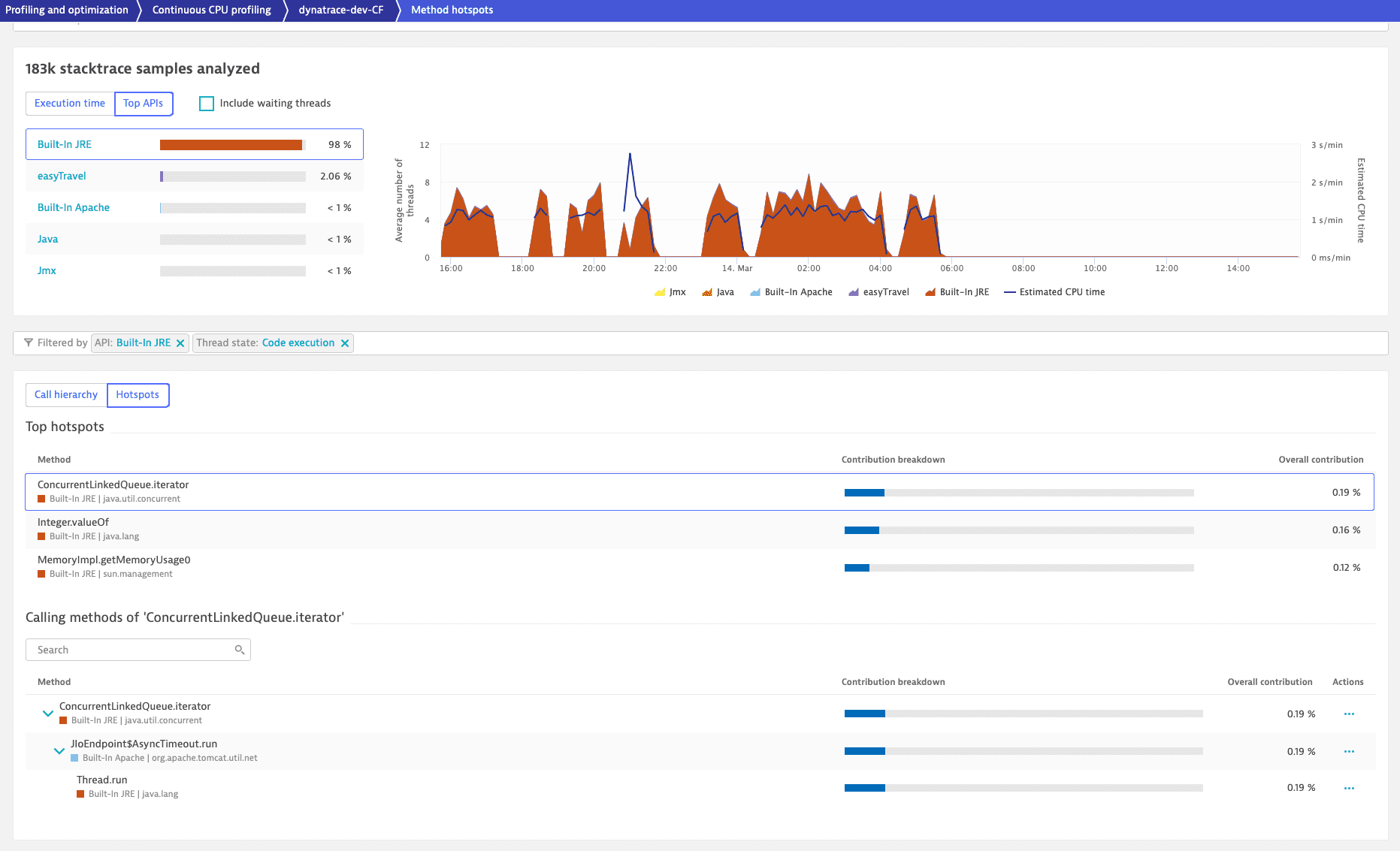
Analysis options
To analyze a process group, remove the filters.
The color coding of the pie chart, the area chart, and the bars in the code-level stack facilitate code-level diagnostics.
To access the breakdown of processes, select the Top APIs tab. You can configure the list of APIs.
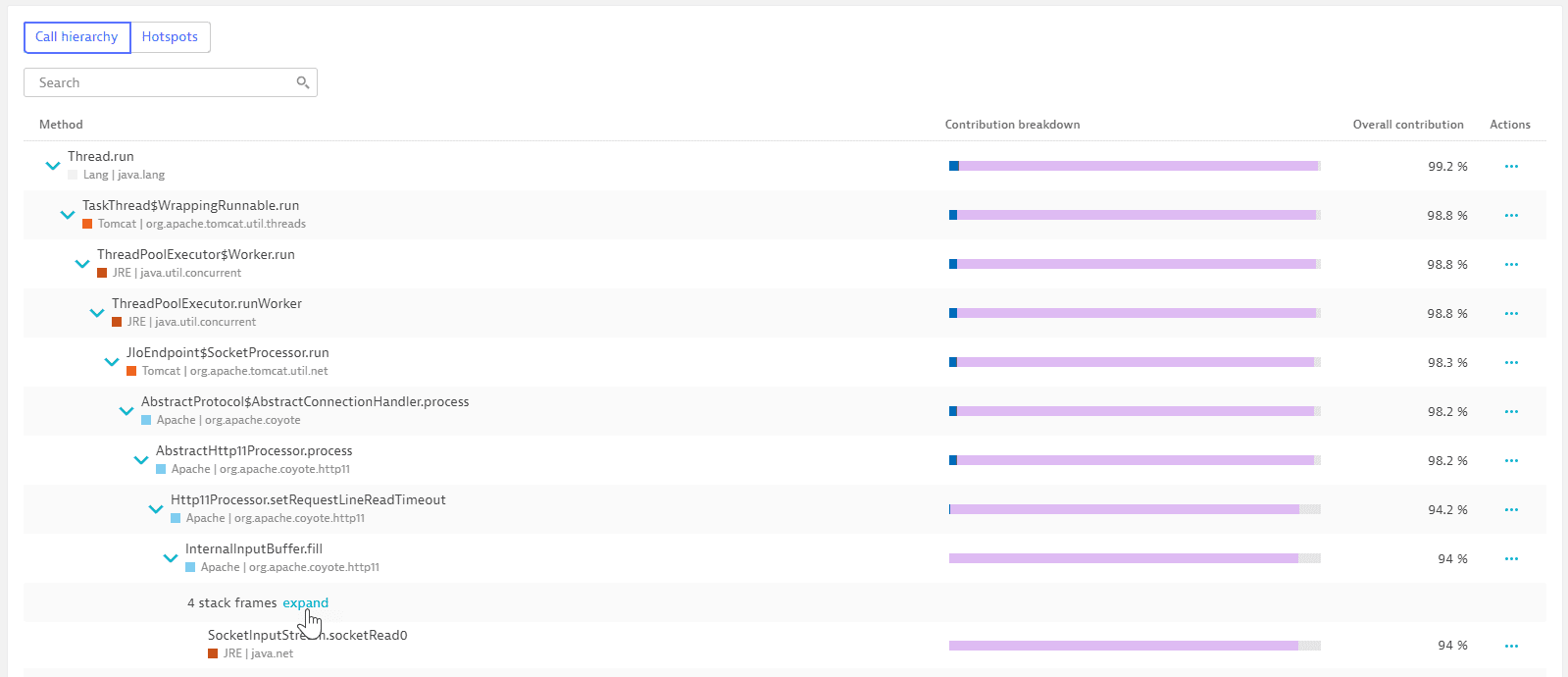
To view the forward stack trace, select the Call hierarchy tab. Each listed method is tagged with the name and color of the API.
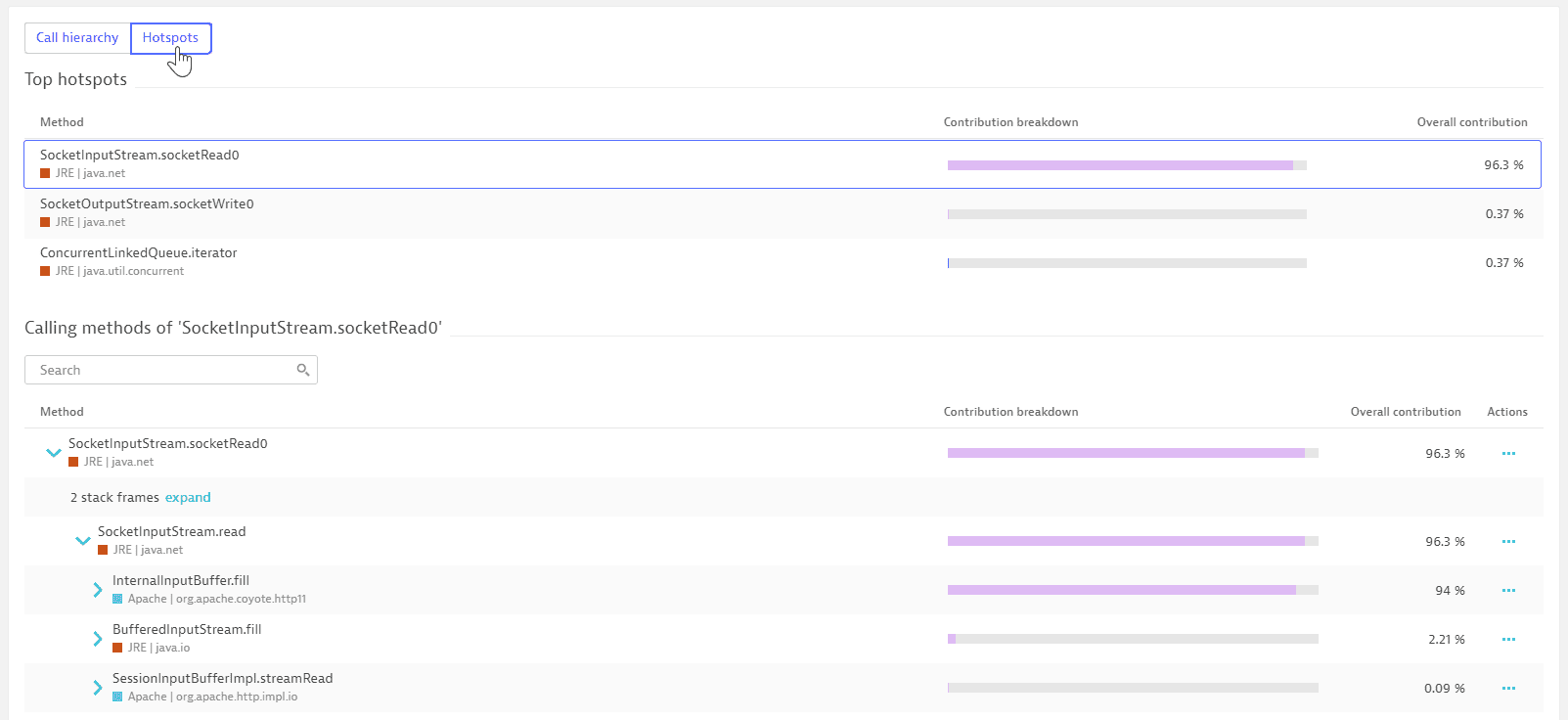
Select the Hotspots tab to view the top three hotspots with reverse stack traces.
Filter
When you filter the execution times and top APIs, the Call hierarchy and Hotspots views inherit the defined filters.
In the following example, filtering by code execution and Built-In JRE (by selecting Code execution under the Execution time tab and selecting Built-In JRE under the Top APIs tab) reveals in the Hotspots tab that most of the built-in JRE API execution time is within the ConcurrentLinkedQueue.iterator call. When you open the stack frames, you can identify the culprit.
Download code
Prerequisites
Ensure you have the View sensitive request data permission in your environment.
Downloading the code is supported for Java, .NET, and Node.js.
To download the code for an execution,
-
Go to Actions and select > Source code.
-
Choose the process from which you want to download the code.
-
Select Download for the execution you're interested in.
-
Open the source code.
The source code is directly visible in Dynatrace.
 Profiling & Optimization
Profiling & Optimization