Address remediation
In the following, you'll learn how to manage remediation of entities affected by or related to a vulnerability. You can
- Apply fix recommendations from Snyk Third-party vulnerabilities
Apply fix recommendations from Snyk
Third-party vulnerabilities
For vulnerabilities based on the Snyk feed, a fix recommendation is displayed if one is available. It consists of a library upgrade suggestion to solve the vulnerability.
-
On the Prioritization page, select a vulnerability title.
-
On the details page of the vulnerability, look for Fix recommendation.

Make sure to restart processes after upgrading a library.
Track remediation progress
You can add links to tickets created in your issue tracking system for affected entities.
Adding a tracking link allows you to
- Navigate to the associated URL
- Track the remediation progress of the selected entities
You can easily check, for example, if someone is already working on fixing the vulnerability.
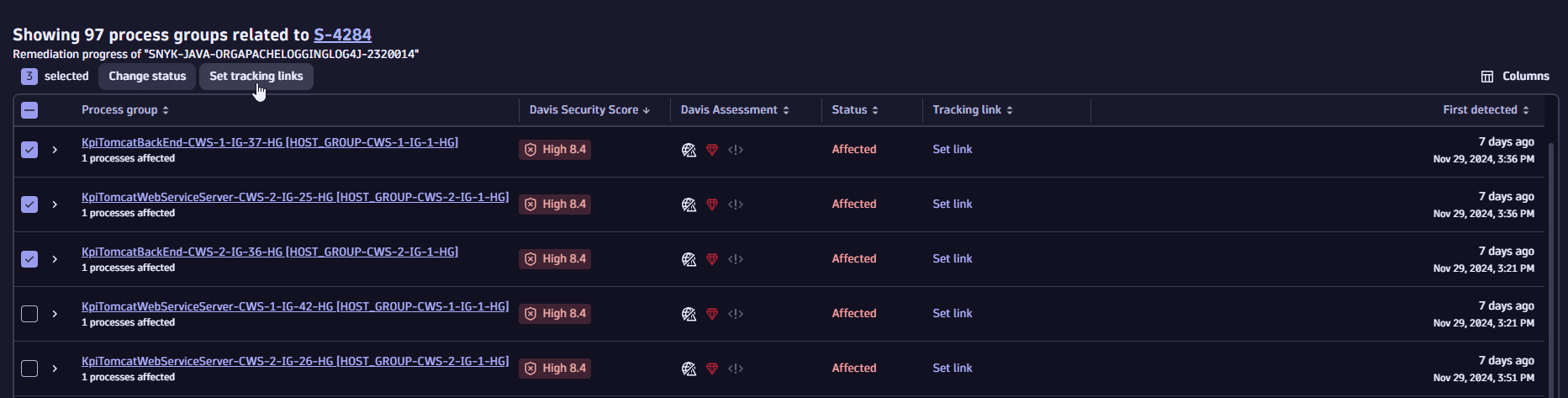
Set up tracking links
You can add, edit, or delete tracking links individually or in bulk.
-
In the vulnerability details, select View all process groups/View all Kubernetes nodes to navigate to the process group/Kubernetes node overview page related to the vulnerability.
-
You have the following options:
-
To add a tracking link, select Set link for the desired entity.
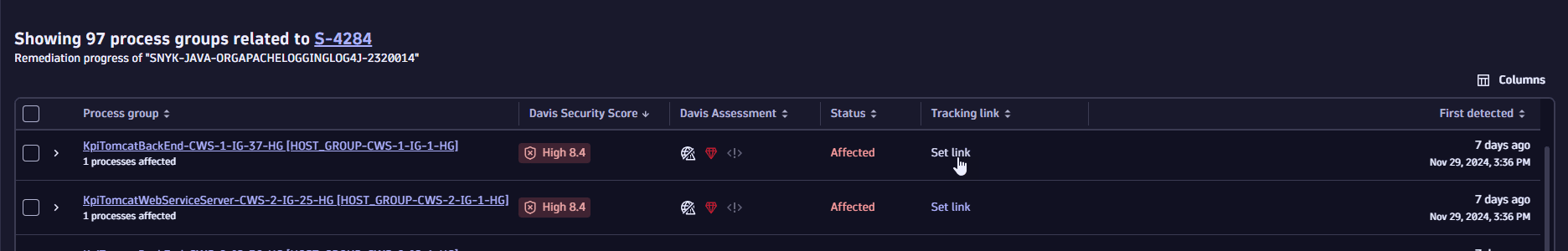
-
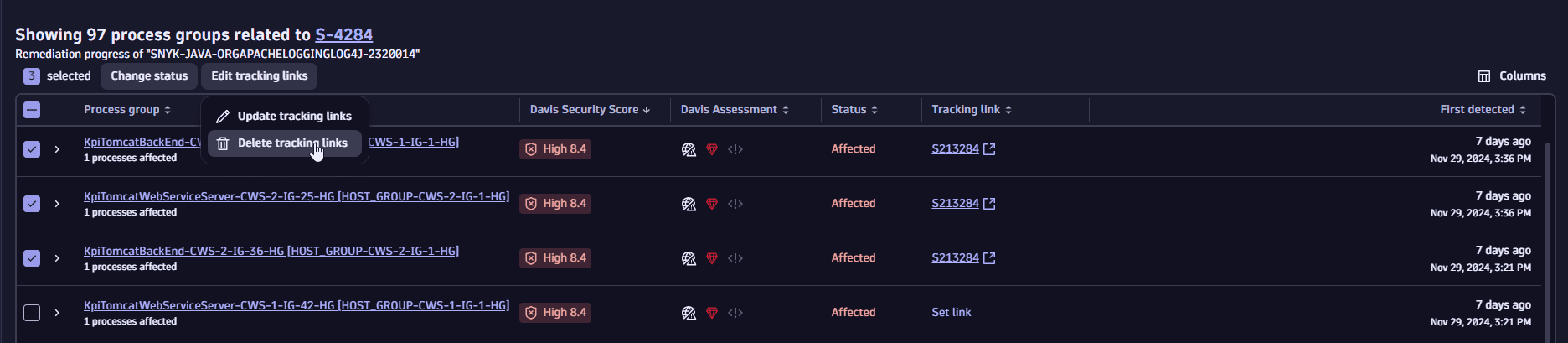
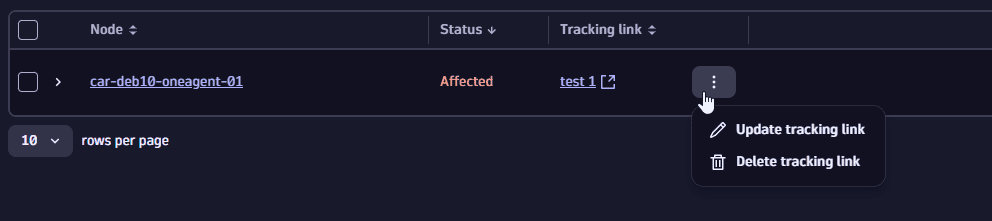
To edit or delete a link, select
next to the tracking link for the desired entity, and then select Update tracking link / Delete tracking link.
-
Drill down into the source of vulnerabilities
To fix vulnerabilities you need to find the root cause. You can examine
- Vulnerable components Third-party vulnerabilities
- Entry points Code-level vulnerabilities
- Code location Code-level vulnerabilities
Examine vulnerable components
Third-party vulnerabilities
There are several ways to see information about the vulnerable component:
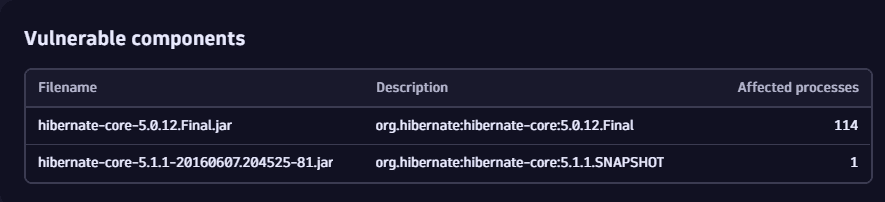
On the details page of a vulnerability
In the Vulnerable components section, you can get information about the name and description of the libraries containing the identified vulnerability and the number of affected processes.
- On the Prioritization page, select a vulnerability title.
- On the details page of the vulnerability, look for Vulnerable components.
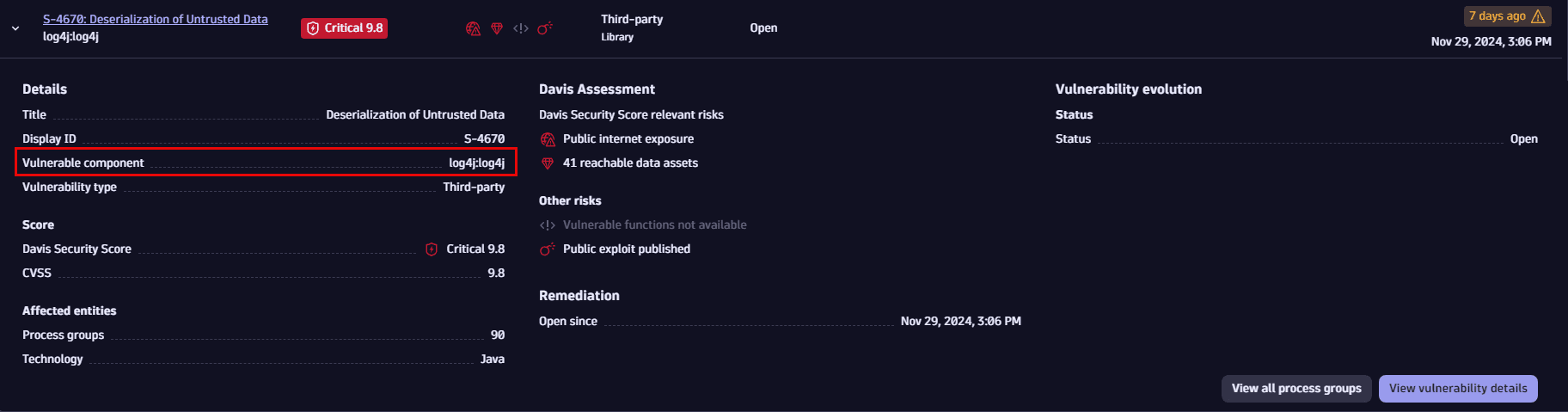
On the Prioritization page
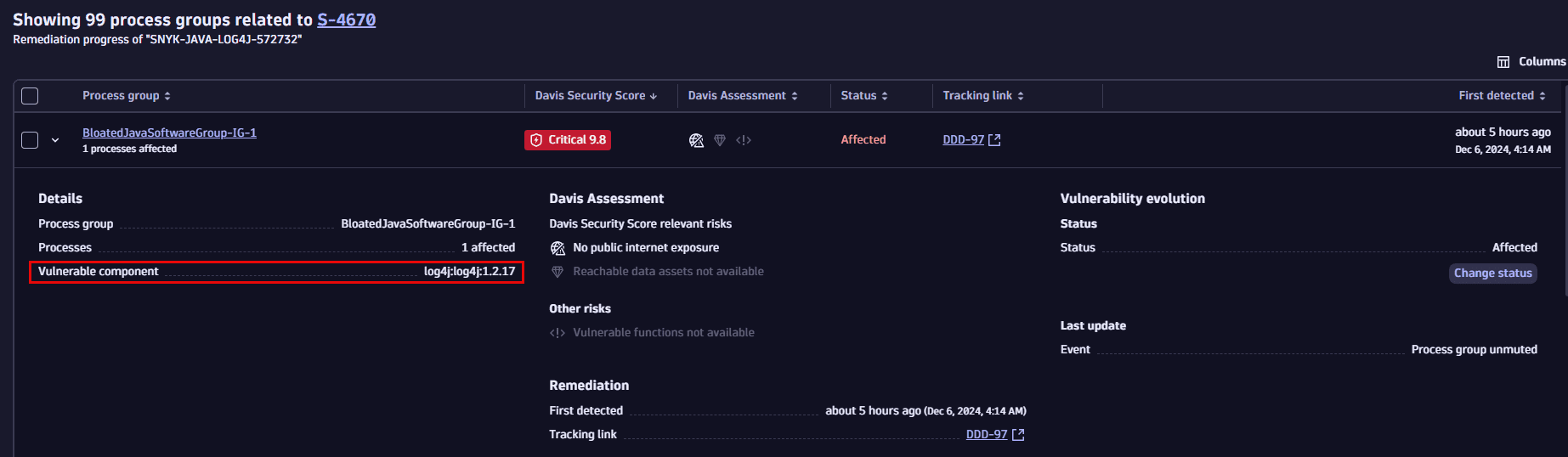
- On the Prioritization page, expand a row for a selected vulnerability.
- Look for Details > Vulnerable component.
On the overview page of process groups or Kubernetes nodes
- In the vulnerability details, select View all process groups/View all Kubernetes nodes to navigate to the process group/Kubernetes node overview page related to the vulnerability.
- Expand a row for an affected entity.
- Look for Details > Vulnerable component.
FAQ
Why is a fixed vulnerability still showing as open.
Further reading
-
To learn more about vulnerable components, see Concepts: Vulnerable component.
-
To understand how Dynatrace evaluates vulnerable components, see Vulnerability evaluation: Third-party vulnerabilities.
Examine entry points
Code-level vulnerabilities
In Entry points you can determine in which ways a vulnerability could be exploited.
- On the Prioritization page, select a vulnerability title.
- On the details page of the vulnerability, look for Entry points.
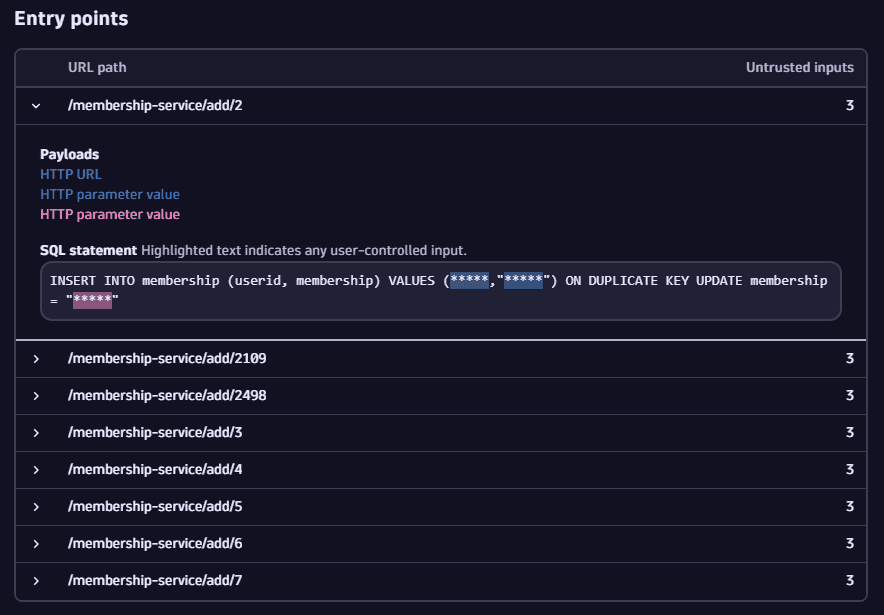
If the same vulnerability is reachable by multiple HTTP paths, multiple entry point entries are listed. To save memory and network traffic, a limited number of entries is displayed.
If a code-level vulnerability is resolved or is about to be resolved in the next 30 minutes, the entry points are no longer open (vulnerable).
Further reading
To learn more about entry points, see Concepts: Entry points.
Examine code location
Code-level vulnerabilities
In Code location you can see the location where the vulnerable function is called from.
You have two options to navigate there.
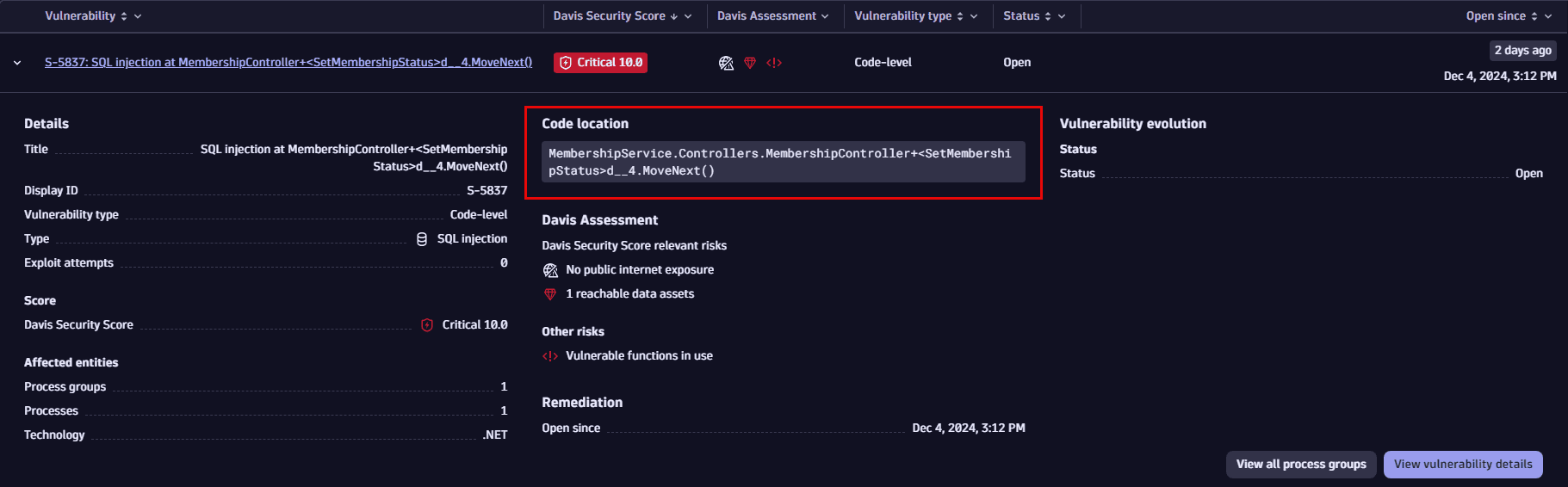
On the Prioritization page
- Expand a row for a selected vulnerability.
- Look for Code location.
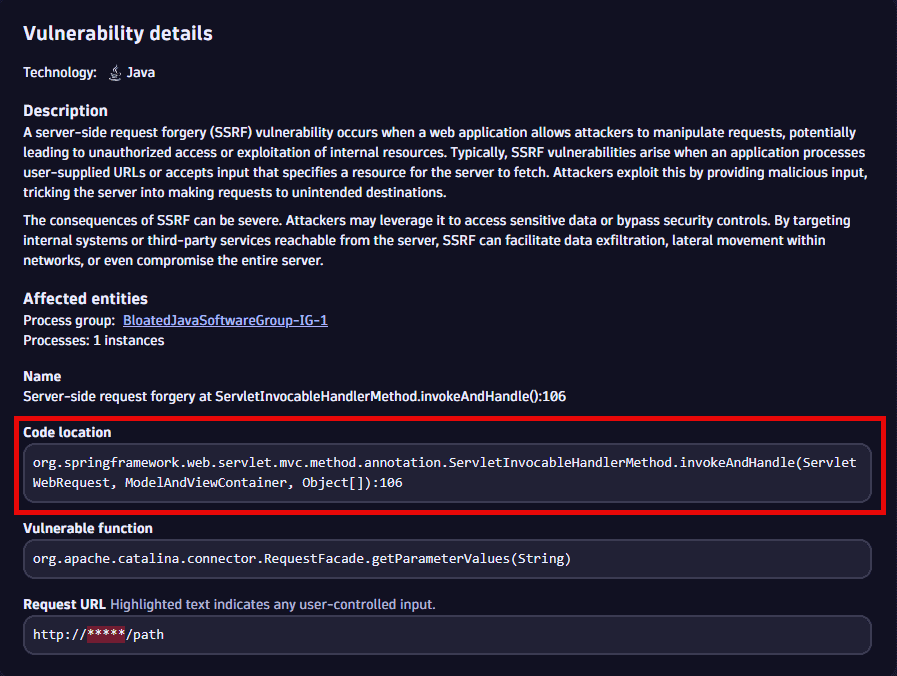
On the details page of a vulnerability
- On the Prioritization page, select a vulnerability title.
- On the details page of the vulnerability, look for Vulnerability details > Code location.
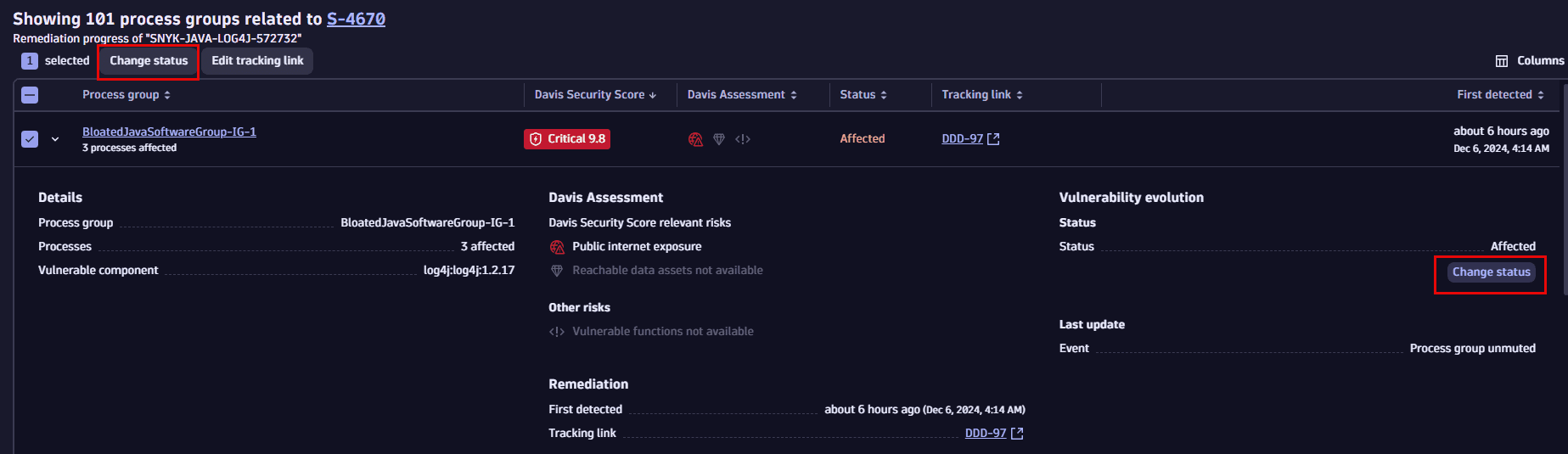
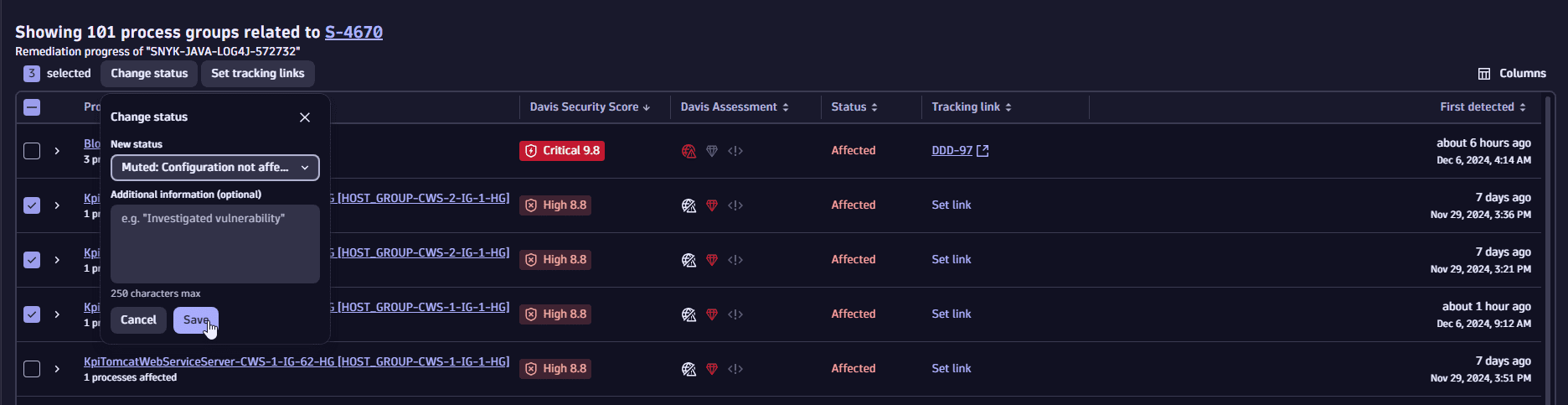
Change the mute status of affected entities
You can change the mute status of affected entities according to your findings and needs. For example, you can set the status of an affected entity to Mute if you wish to ignore the vulnerability for this particular entity:
- It could be a false flag, meeting some additional conditions that make the vulnerability irrelevant.
- Or maybe there’s no remediation available and a workaround has been applied.
Muting all affected entities of a vulnerability sets the vulnerability status to Muted (Open). For details, see Vulnerability status.
You can change the status of affected entities individually or in bulk.
- In the vulnerability details, select View all process groups/View all Kubernetes nodes to navigate to the process group/Kubernetes node overview page related to the vulnerability.
- Select an entity (or select
on the left side of an entity to expand the row).
- Select Change status.