Vulnerability source
The following explains the concepts specific to drilling down into the source of vulnerabilities:
- Vulnerable component Third-party vulnerabilities
- Entry point Code-level vulnerabilities
- Code location Code-level vulnerabilities
Vulnerable component
Third-party vulnerabilities
A vulnerable component is a software component (library) or runtime component (for example, a Kubernetes package) that has a vulnerable function causing a vulnerability:
- For Snyk-based vulnerabilities, the package name
- Example:
org.apache.tomcat:tomcat-coyote
- Example:
- For NVD-based vulnerabilities, the runtime technology
- Examples:
Java runtime,Node.js runtime
- Examples:
Use case
Drill down into the source of vulnerabilities: Explore vulnerable components.
FAQ
Why is a fixed vulnerability still showing as open.
Entry point
Code-level vulnerabilities
An entry point is a point in the code where an attacker could enter the application, for example, by passing user input fields to the application (such as a login form or search bar).
Key concepts
- URL path
The path used in the HTTP request to reach and potentially exploit the vulnerability.
- Example:
/user/1218/bio
- Example:
- Untrusted input
The input that is passed to the vulnerable function.
-
Example:
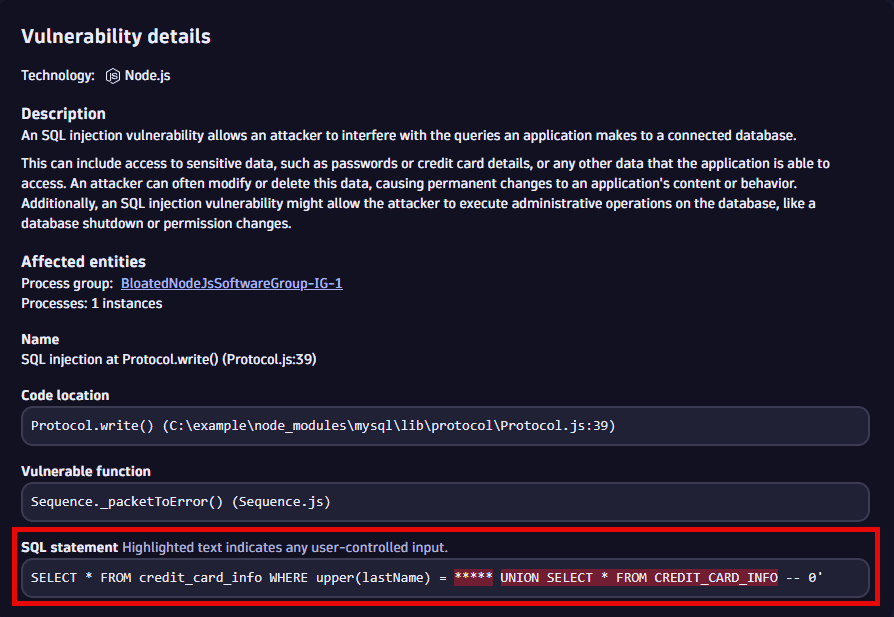
- Payloads
The user-controlled inputs that could be used to exploit the vulnerability. If there's a key for the payload (for example, an HTTP parameter name or an HTTP header name), it's displayed after the colon.
- Example:
HTTP parameter value: bioText
- Example:
Use case
Drill down into the source of vulnerabilities: Explore entry points.
Code location
Code-level vulnerabilities
A code location shows where the actual vulnerability is in the code (the location where the vulnerable function is called from).
- Example:
SQL injection at DatabaseManager.updateBio():82
Use case
Drill down into the source of vulnerabilities: Explore code location.