AWS Fargate log integration on ECS and EKS
- Latest Dynatrace
- How-to guide
- 3-min read
AWS Fargate provides a serverless container runtime for ECS (Elastic Container Service) and EKS (Elastic Kubernetes Service) environments where traditional agent installation isn't possible. This makes it ideal for log forwarding scenarios using log routers like Fluent Bit to stream container logs to external monitoring platforms.
Ingest Fargate logs
You can ingest AWS Fargate logs:
-
For containers running on ECS, using AWS FireLens, which uses Fluent Bit as its log router.
-
For containers running on EKS, using EKS’s Fluent Bit log router. Log forwarding is possible through Amazon Data Firehose, or directly to CloudWatch.
AWS FireLens:
-
Simplifies log management by routing container logs to log monitoring platforms including Dynatrace or destinations like Amazon S3, CloudWatch.
-
Reduces storage and ingestion costs by supporting advanced log filtering and routing.
-
Helps to meet compliance requirements by ensuring enhanced security with encrypted log transmission.
Example: Ingest ECS Fargate logs with Fluent Bit
The example below describes how to configure the ingestion of ECS Fargate logs.
When creating a new task definition using the AWS Management Console, the FireLens integration section makes it easy to add a log router container. Follow the steps below to configure log ingest:
- In the AWS Management Console, go to the Firelens integration section.
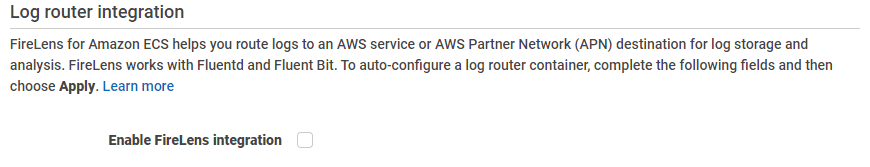
- Pick the built-in Fluent Bit image.
- Edit the container in which your log-generating apps are running.
- In the Storage and Logging section, select awsfirelens as the log driver.
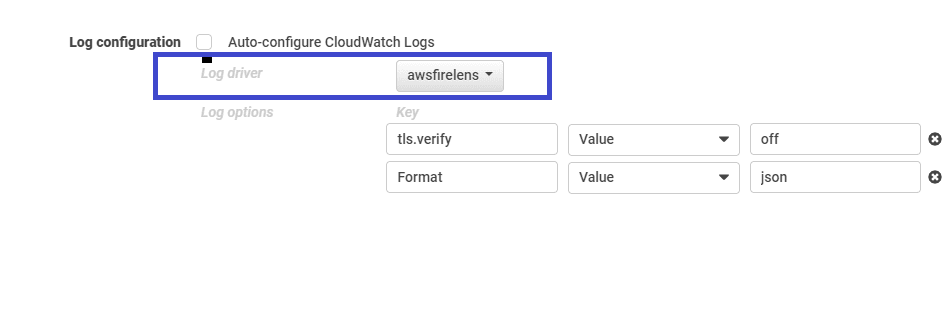
The settings for the log driver should point to the log ingest API of your SaaS tenant. You need to provide two headers for Fluent Bit: content type and authorization token. As FireLens supports only one header, you can pass the content type as part of the URL. Your configuration for AWS FireLens should contain certain key-value pairs, as shown in the code block below.
Name: httpTLS: onFormat: jsonHeader: Authorization Api-Token {your-API-token-here}Host: {your-environment-id}.live.dynatrace.comPort: 443URI: /api/v2/logs/ingest?Content-Type=application/jsonAllow_Duplicated_Headers": "false"Json_Date_Format": "iso8601"Json_Date_Key": "timestamp"
To avoid publishing the token in plaintext, follow the steps in AWS Secrets Manager. Once your application starts publishing logs, you can view them in the Dynatrace UI.
Refer to AWS sample repository for the task definition JSON with Dynatrace configuration.
For more configuration details, see Amazon ECS Developer Guide.